Improving security is a top priority for the team. Therefore, we take the severity of these security issues very seriously. We aim to provide the best possible experience for our users, and therefore do not recommend removing this protection until an official patch has been released by the community. If you are running an outdated version of Tiny CSRF, you can upgrade by following the instructions outlined in the Tiny docs.
What is Tiny?
Tiny is a lightweight, minimalistic cross-site request forgery (CSRF) protection library created by the team at Laravel.
Tiny provides a simple and unobtrusive way to add cross-site request forgery (CSRF) protection to any existing Eloquent model. Tiny utilizes the CSRF token generated by Laravel's default authentication system, which provides an excellent level of protection against XSRF attacks.
2 - What is CSRF?
Cross-site request forgery (CSRF) is an attack that occurs when malicious software on one web site is able to force a user's computer or mobile device to send a request to another web site by exploiting the victim's trust in the first site. It takes advantage of insecurely configured web applications that do not require users to enter credentials when performing actions on behalf of the application.
Summary
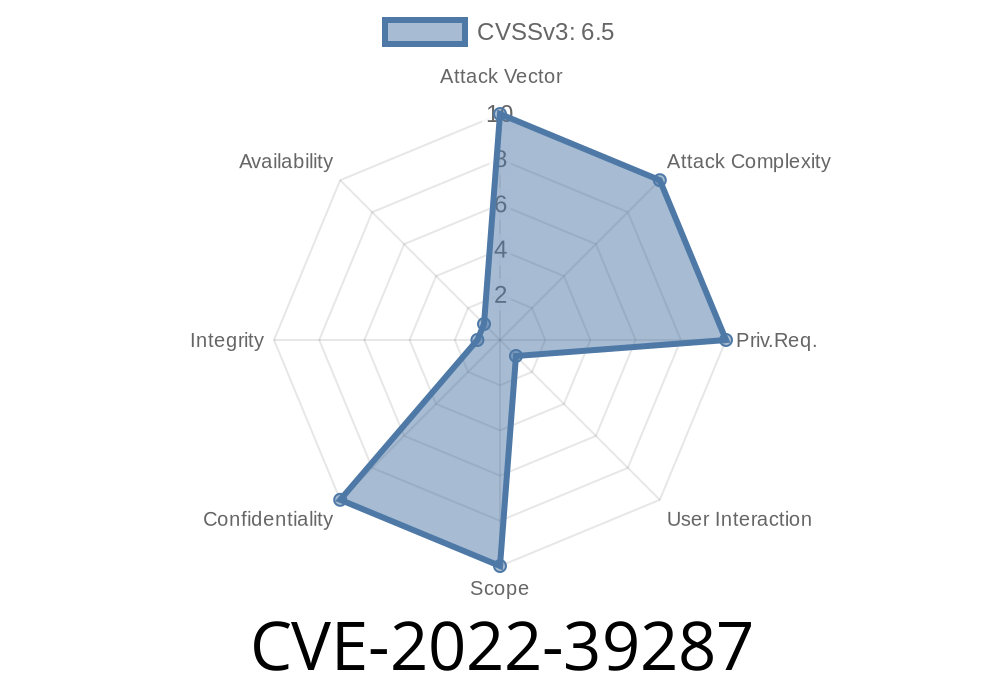
A bug has been found in Tiny CSRF. It is a critical vulnerability that may allow malicious users to take over your account. If you are running an outdated version of Tiny CSRF, you can upgrade by following the instructions outlined in the Tiny docs.
Current version of Tiny CSRF
The current version of Tiny CSRF is 1.4.0.
Potential Impact of Tiny CSRF
A potential impact of this issue is that the user would be able to execute code in their browser's context. This is possible by using an injection attack, where a malicious web page can inject JavaScript code into a target web site. The potential consequences of these attacks include:
- Theft of personal information
- Tampering with the website's functionality
- Disclosure of data stored by the website or its users
- Exploitation of vulnerabilities in the website
Timeline
Published on: 10/07/2022 20:15:00 UTC
Last modified on: 10/11/2022 13:12:00 UTC