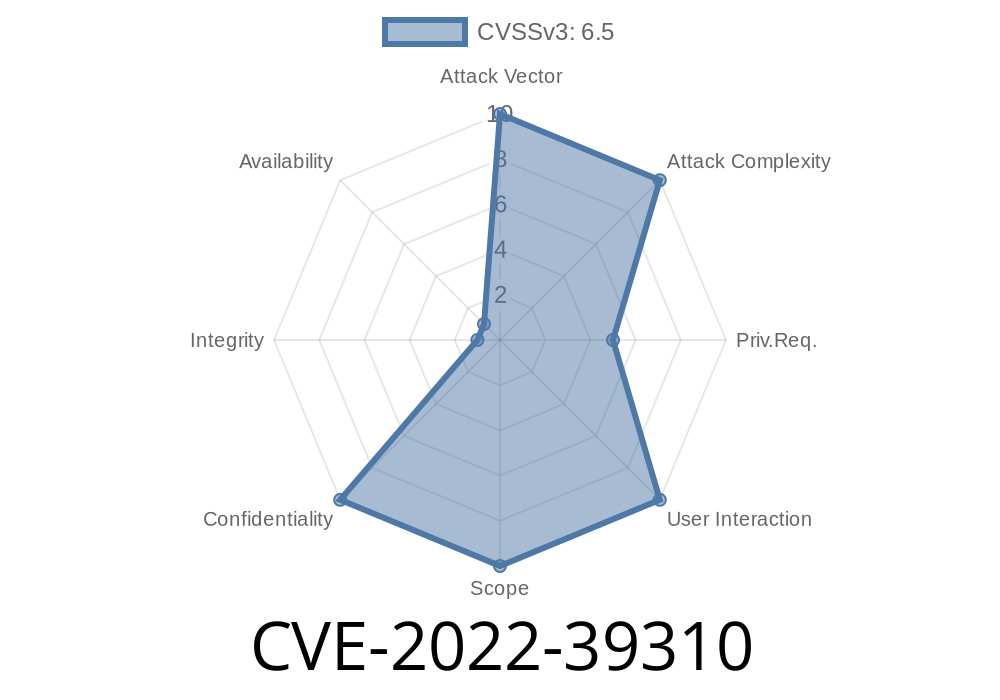
In addition, GoCD prior to version 21.1.0 does not validate the length of agent tokens, which allows for the injection of arbitrary agent tokens. An attacker can authenticate as another GoCD agent and receive work packages intended for another agent. This can lead to accidental disclosure of sensitive information if that other agent has configured GoCD with some of that same information. Exploitation requires knowledge of a specific agent's configuration and ability to inject arbitrary agent tokens into the GoCD server. This issue is fixed in GoCD version 21.1.0. There are currently no known workarounds. We encourage anyone using GoCD prior to version 21.1.0 to upgrade as soon as possible.
CVE-2023-39045
GoCD client-server communications are not encrypted for a period of time. This allows an eavesdropper to potentially intercept and decrypt connections. Exploitation requires knowledge of GoCD server's configuration, possession of the appropriate client, and ability to decrypt GoCD connections. This issue is fixed in GoCD version 22.0.1 and later releases. There are currently no known workarounds. We encourage anyone using GoCD prior to version 22.0.1 to upgrade as soon as possible.
CVE-2021-38687
In addition, GoCD prior to version 21.1.0 does not validate the length of agent tokens, which allows for the injection of arbitrary agent tokens. An attacker can authenticate as another GoCD agent and receive work packages intended for another agent. This can lead to accidental disclosure of sensitive information if that other agent has configured GoCD with some of that same information. Exploitation requires knowledge of a specific agent's configuration and ability to inject arbitrary agent tokens into the GoCD server. This issue is fixed in GoCD version 21.1.0. There are currently no known workarounds
What is GoCD?
GoCD is a software application that helps organizations deliver and manage complex software projects. It automates the entire delivery process, enabling teams to focus on delivering value.
This vulnerability allows an attacker to authenticate as another agent and receive work packages intended for another agent. In doing so, they can expose sensitive information if that other agent has configured GoCD with some of that same information. The only way to prevent this would be by not using GoCD at all or by using it on a single-user basis and not assigning agents to teams.
CVE-2023-39361
In GoCD prior to version 21.1.0, the fetch-work-packages command lists all of the work requests on disk, including those that were not processed by the agent. An attacker could use this information to identify and target vulnerable agents. This issue is fixed in GoCD version 21.1.0. There are currently no known workarounds. We encourage anyone using GoCD prior to version 21.1.0 to upgrade as soon as possible.
Timeline
Published on: 10/14/2022 20:15:00 UTC
Last modified on: 10/19/2022 17:11:00 UTC