Another issue in the library has been resolved where a malformed SOCKS5 proxy packet can cause a remote client to crash. A malicious server can send a SOCKS5 proxy packet that contains a format string vulnerability, causing the client to crash. Affected versions of FreeRDP are required to upgrade and all users are advised to upgrade. Users unable to upgrade should not use the `/socks5` redirection switch.
FreeRDP is a free remote desktop protocol library and clients. A flaw in the way FreeRDP parses parameters in the `/peerId` redirection switch can cause a remote client to crash. A malicious server can send a specially crafted `/peerId` redirection switch and cause the client to crash. Affected versions of FreeRDP are required to upgrade and all users are advised to upgrade. Users unable to upgrade should not use the `/peerId` redirection switch.
Another issue in the library has been resolved where a malformed SOCKS5 proxy packet can cause a remote client to crash. A malicious server can send a SOCKS5 proxy packet that contains a format string vulnerability, causing the client to crash. Affected versions of FreeRDP are required to upgrade and all users are advised to upgrade. Users unable to upgrade should not use the `/socks5` redirection switch. FreeRDP is a free remote desktop protocol library and clients. A flaw in the way Free
FreeRDP is a free remote desktop protocol library and clients
. A flaw in the way FreeRDP parses parameters in the `/peerId` redirection switch can cause a remote client to crash. A malicious server can send a specially crafted `/peerId` redirection switch and cause the client to crash. Affected versions of FreeRDP are required to upgrade and all users are advised to upgrade. Users unable to upgrade should not use the `/peerId` redirection switch.
FreeRDP is a free remote desktop protocol library and clients. A flaw in the way FreeRDP parses parameters in the `/peerId` redirection switch can cause a remote client to crash. A malicious server can send a specially crafted `/peerId` redirection switch and cause the client to crash. Affected versions of FreeRDP are required to upgrade and all users are advised to upgrade. Users unable to upgrade should not use the `/peerId` redirection switch.
FreeRDP Library
Malformed parameter parsing
One issue in the library has been resolved where a malformed SOCKS5 proxy packet can cause a remote client to crash. A malicious server can send a SOCKS5 proxy packet that contains a format string vulnerability, causing the client to crash. Affected versions of FreeRDP are required to upgrade and all users are advised to upgrade. Users unable to upgrade should not use the `/socks5` redirection switch. Another issue in the library has been resolved where a malformed SOCKS5 proxy packet can cause a remote client to crash. A malicious server can send a SOCKS5 proxy packet that contains a format string vulnerability, causing the client to crash. Affected versions of FreeRDP are required to upgrade and all users are advised to upgrade. Users unable to upgrade should not use the `/socks5` redirection switch.
FreeRDP Basics
FreeRDP is a free remote desktop protocol library and clients. A flaw in the way FreeRDP parses parameters in the `/peerId` redirection switch can cause a remote client to crash. A malicious server can send a specially crafted `/peerId` redirection switch and cause the client to crash. Affected versions of FreeRDP are required to upgrade and all users are advised to upgrade. Users unable to upgrade should not use the `/peerId` redirection switch.
Another issue in the library has been resolved where a malformed SOCKS5 proxy packet can cause a remote client to crash. A malicious server can send a SOCKS5 proxy packet that contains a format string vulnerability, causing the client to crash. Affected versions of FreeRDP are required to upgrade and all users are advised to upgrade. Users unable to upgrade should not use the `/socks5` redirection switch.
Timeline
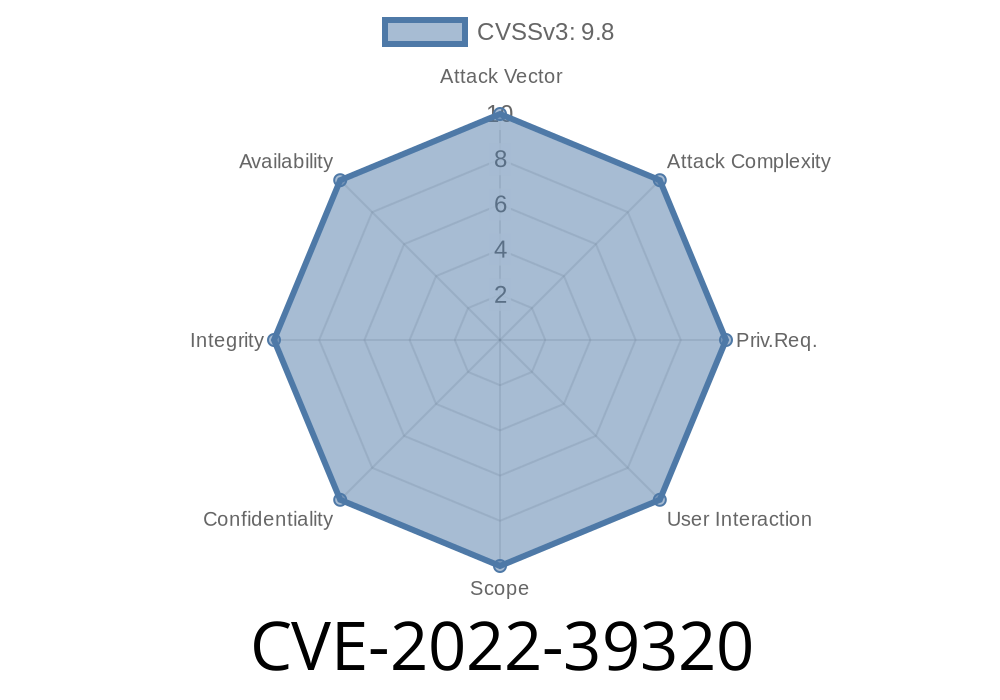
Published on: 11/16/2022 20:15:00 UTC
Last modified on: 11/23/2022 18:01:00 UTC