Or if you have to parse a non-XML document, then use the `parseNonXml` method. Please refer to the issue for more details. ------------------------- If you are using a version of xmldom older then 0.7.7, then you are vulnerable to a very specific attack. The attack works by having two documents, one that is well-formed and one that is not. The not well-formed one embeds an element with a `Content-Type` of `xml` to try and trick xmldom into treating it as a XML document. If a user then loads the well-formed one into an xmldom parser (for example by saving it to a file, then loading it via JavaScript), then an attacker can control the data in the well-formed one. This is possible because xmldom will pass the not well-formed one’s data through as though it were the well-formed one. The way to protect against this attack is to always validate the `Content-Type` of the document you are trying to parse. -------------------------- If you are using xmldom version 0.8.4 or later, then you are not vulnerable to this attack. -------------------------- If you are using a version of xmldom older then 0.8.4, then you are vulnerable to a very specific attack. The attack works by having two documents, one that is well-formed and one that is not
What do we know about the vulnerability?
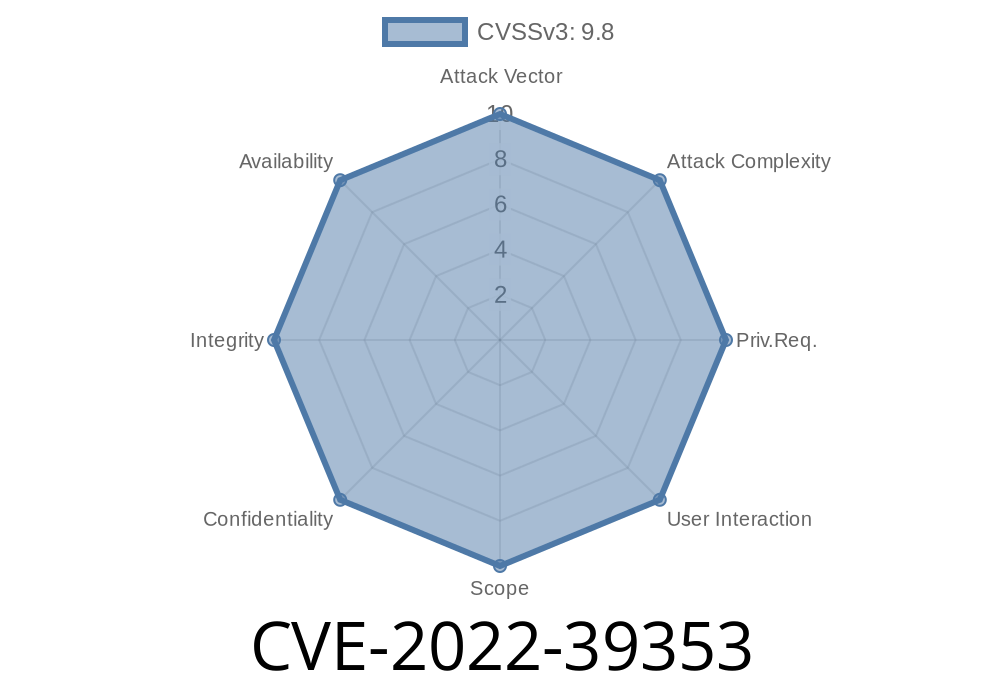
In the xmldom project, we have been made aware of a vulnerability in the parser module. This vulnerability is specific to versions of xmldom older then 0.7.7 and allows an attacker to control the data in a well-formed document by passing it through as if it were a not well-formed one. -------------------------- If you are using xmldom version 0.8.4 or later, then you are not vulnerable to this attack. -------------------------- If you are using a version of xmldom older then 0.8.4, then you are vulnerable to a very specific attack. The attack works by having two documents, one that is well-formed and one that is not
Please refer to the issue for more details on how the vulnerability works and some possible solutions: https://github.com/xmldom/xmldom/issues/39353
What do you need to do to protect against this attack?
The way to protect against this attack is to always validate the `Content-Type` of the document you are trying to parse. -------------------------- If you are using xmldom version 0.8.4 or later, then you are not vulnerable to this attack. -------------------------- If you are using a version of xmldom older then 0.8.4, then you are vulnerable to a very specific attack. The attack works by having two documents, one that is well-formed and one that is not
People often overlook the importance of digital marketing in their business’s growth. With the right strategies, like pay per click (PPC) advertising on Facebook and search engine optimization (SEO), a company can get more traffic and increase brand awareness and trustworthiness with their customers while spending less money in return. One effective strategy is using pictures in your ad campaigns on Facebook as people respond well to pictures.
Timeline
Published on: 11/02/2022 17:15:00 UTC
Last modified on: 11/04/2022 12:29:00 UTC