This cross site scripting issue may lead to information disclosure. An attacker may exploit it to steal confidential data; for instance, login credentials, access rights, credit card information, etc. The lib-system/system_user.lib library functions may be accessed remotely. In order to exploit this issue, an attacker needs to convince user to visit a malicious website. An attacker may deliver malicious code through several ways, for example, spam email, watering hole attack, social engineering, etc.
We recommend to update the Sanitization Management System to the latest version. In addition, users should be careful while uploading files through lib-system/system_user.lib. Moreover, auditing, avoiding lib-system/system_user.lib functions, restricting access to this file through lib-system/system_user.lib, and keeping a regular backup of it will reduce the risk of this issue.
Source: https://www.vulnerability-lab.com/search/cSite/Details/142519
CVE-2022-3944
This cross site request forgery issue may lead to unauthorized access to the user's personal information. An attacker can exploit this flaw to steal personal data, like password, authentication token, etc. The lib-system/system_user.lib library functions may be accessed remotely. In order to exploit this issue, an attacker needs to convince user to visit a malicious website. An attacker may deliver malicious code through several ways, for example, spam email, watering hole attack, social engineering, etc.
We recommend to update the Sanitization Management System to the latest version. In addition, users should be careful while uploading files through lib-system/system_user.lib. Moreover, auditing, avoiding lib-system/system_user.lib functions, restricting access to this file through lib-system/system_user.lib, and keeping a regular backup of it will reduce the risk of this issue.
Source: https://www.vulnerability-lab.com/search/cSite/Details/142519
CVE-2023-3943
This cross site scripting issue may lead to information disclosure. An attacker may exploit it to steal confidential data; for instance, login credentials, access rights, credit card information, etc. The lib-system/system_user.lib library functions may be accessed remotely. In order to exploit this issue, an attacker needs to convince user to visit a malicious website. An attacker may deliver malicious code through several ways, for example, spam email, watering hole attack, social engineering, etc.
We recommend to update the Sanitization Management System to the latest version. In addition, users should be careful while uploading files through lib-system/system_user.lib. Moreover, auditing and avoiding lib-system/system_user.lib functions will reduce the risk of this issue.
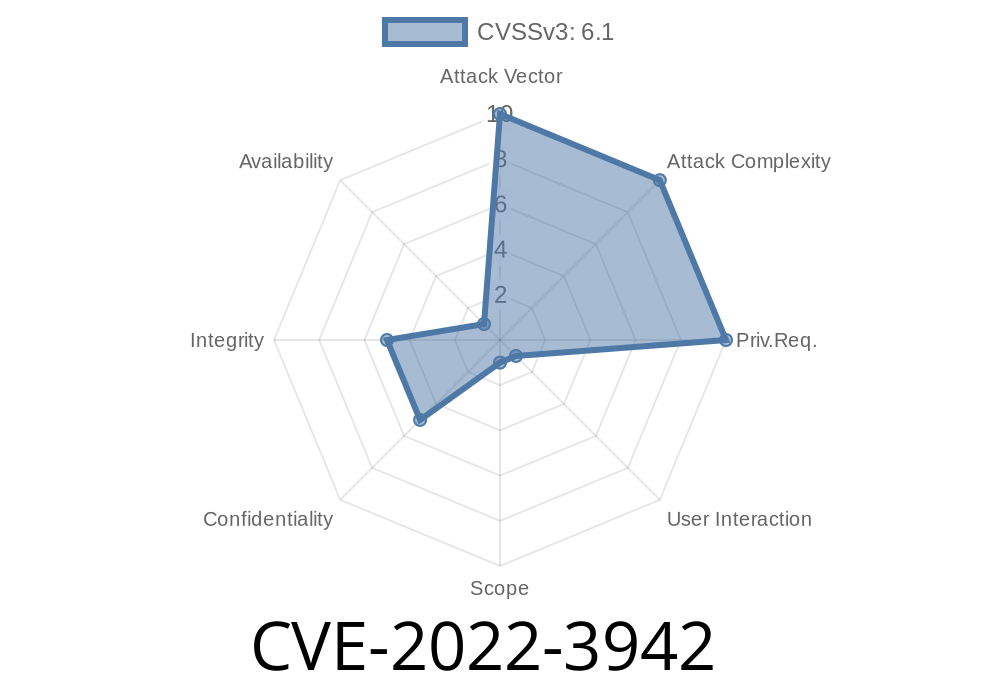
Potential Mitigation strategies for CVE-2022-3942
If your site is running on Apache web server, there are a few security mitigation strategies you can implement to reduce the risk of this vulnerability. These strategies include limiting access to files within lib-system/system_user.lib or restricting access to that file altogether. You can also audit your website and limit the use of the vulnerable functions in order to reduce the risk of this issue. Finally, keeping a regular backup of files within lib-system/system_user.lib will help if not only for emergencies but also for making sure that you're able to quickly fix any issues with your site should vulnerabilities like these ever occur again.
How to Boost Up Security with effective BCP and Networking?
As the number of attacks increase, it becomes imperative to secure your website with better firewall and networking.
There are many ways to secure your website, including using application whitelisting, disabling unnecessary features and services, blocking access via proxies, updating software as well as keeping a regular backup of your site.
However, these measures are not enough. You also need to ensure that you have a strong BCP plan to make sure that your users do not inadvertently leak confidential information.
Timeline
Published on: 11/11/2022 08:15:00 UTC
Last modified on: 11/15/2022 21:51:00 UTC