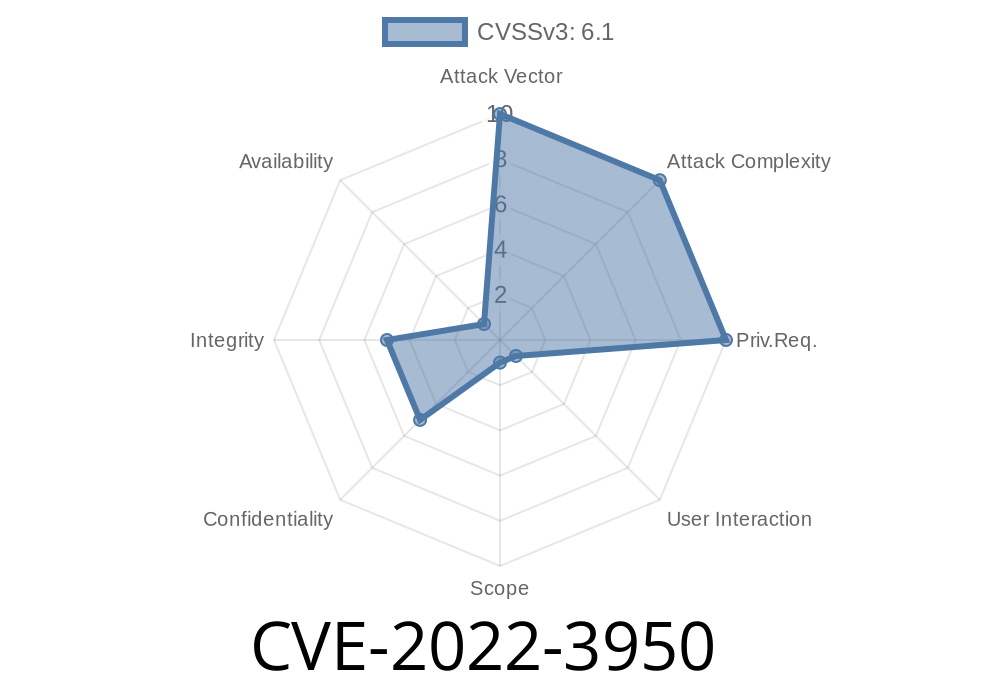
A cross site scripting vulnerability, identified as CVE-2022-3950, has recently been discovered in the Sanluan PublicCMS. As a problematic vulnerability, the affected function is initLink of the dwz.min.js file of the Tab Handler component. The exploit can be launched remotely and could lead to considerable security risks. The proposed solution to mitigate this issue involves applying a patch named a972dc9b1c94aea2d84478bf26283904c21e4ca2. The vulnerability has an assigned identifier VDB-213456.
Vulnerability Details
The initLink function in the Tab Handler component's dwz.min.js file contains a cross site scripting vulnerability, which can be exploited remotely. An attacker can manipulate the vulnerability to execute malicious code. The consequences of this vulnerability include unauthorized access to user data, identity theft, and potential spread of malware.
Vulnerability Code Snippet
$(document).ready(function () {
$('#tab-wrapper').tabs({
'initLink': function (id) {
var link = tabLink(id);
if (link) {
//Here comes the risky code
var br = '<a href="' + link + '">Click here to access the vulnerable tab</a>';
$('#' + id).html(br);
}
}
});
});
In the code snippet above, you can see that the vulnerability lies in the initLink function, as it does not sanitize the input properly. As a result, the malicious code can be executed through the improper handling of the link variable.
Original References
1. CVE-2022-3950
2. VDB-213456
Exploit Details
The attacker can accomplish the exploit by crafting and injecting malicious code in the form of a malformed URI, which can then compromise the functionality of the initLink function. This code can be passed as part of a URL or as input to a web form.
Mitigation
To address this vulnerability, it is highly recommended that users apply the patch a972dc9b1c94aea2d84478bf26283904c21e4ca2. The patch aims to sanitize and validate user inputs to prevent cross site scripting attacks. The process of applying the patch may vary depending on the specific version of the software being used, but it generally involves updating the affected files and restarting the web server.
Links to the Patch
1. Patch a972dc9b1c94aea2d84478bf26283904c21e4ca2
Conclusion
In summary, the CVE-2022-3950 vulnerability in Sanluan PublicCMS poses significant risk if left unaddressed. Thankfully, users can quickly mitigate the issue by applying the a972dc9b1c94aea2d84478bf26283904c21e4ca2 patch, which should prevent cross site scripting attacks and protect users from potential data breaches and other threats. As with any software vulnerability, it is crucial to stay informed and apply security updates as soon as possible. Stay safe and secure online!
Timeline
Published on: 11/11/2022 14:15:00 UTC
Last modified on: 11/15/2022 21:06:00 UTC