A second critical vulnerability was found in Vesta's web interface. It is a flaw in sed Handler that results in remote code execution. The issue is located in the function main.sh: sed_handler: main.sh: line 543: [code] Sed_Handler::run_function(function_name, parameters) => function_name = 'sed_handler', parameters = 'set_config.sh?override_header=1' When exploitation is carried out, an attacker can send malicious data to the system. The issue can be addressed by patching the vesta-sed-handler-config.sh file. VDB-216216 is the identifier assigned to this vulnerability. The most severe vulnerability was found in Vesta Control Panel and is classified as critical. It is a flaw in the file sed_handler.sh. When the component is exploited, an attacker can perform remote code execution on the system. The issue can be addressed by patching the vesta-sed-handler-config.sh file. VDB-216215 is the identifier assigned to this vulnerability. Details of the critical vulnerability were described in the advisory published on March 27, 2018. An attacker can exploit this issue to cause denial of service or to get system privileges. A remote attacker can cause a Denial of Service condition by sending a malicious request with a crafted cookie. An attacker can get system privileges by sending a crafted request that submits a valid ticket. It is recommended
Vulnerabilities found in Vesta Network ing Software
Vesta Networking Software has been found with two critical vulnerabilities. The first vulnerability was found in Vesta Control Panel and is classified as critical. It is a flaw in the file sed_handler.sh. When the component is exploited, an attacker can perform remote code execution on the system. The issue can be addressed by patching the vesta-sed-handler-config.sh file. VDB-216215 is the identifier assigned to this vulnerability.
The second vulnerability was found in Vesta Web Interface and is classified as critical. It is a flaw in sed Handler that results in remote code execution. The issue can be addressed by patching the vesta-sed-handler-config.sh file. VDB-216216 is the identifier assigned to this vulnerability.
Vesta system requirements for installation
Vesta is not currently recommended for use on macOS or Windows. However, Vesta's installation process is completely automated, so in theory it should be possible to install the server on any machine with sufficient resources.
As of this writing, it is unclear what limitations there are on what machines can host Vesta. Presumably, these are technical limitations and not a reflection of any security-related policy.
Vulnerable packages
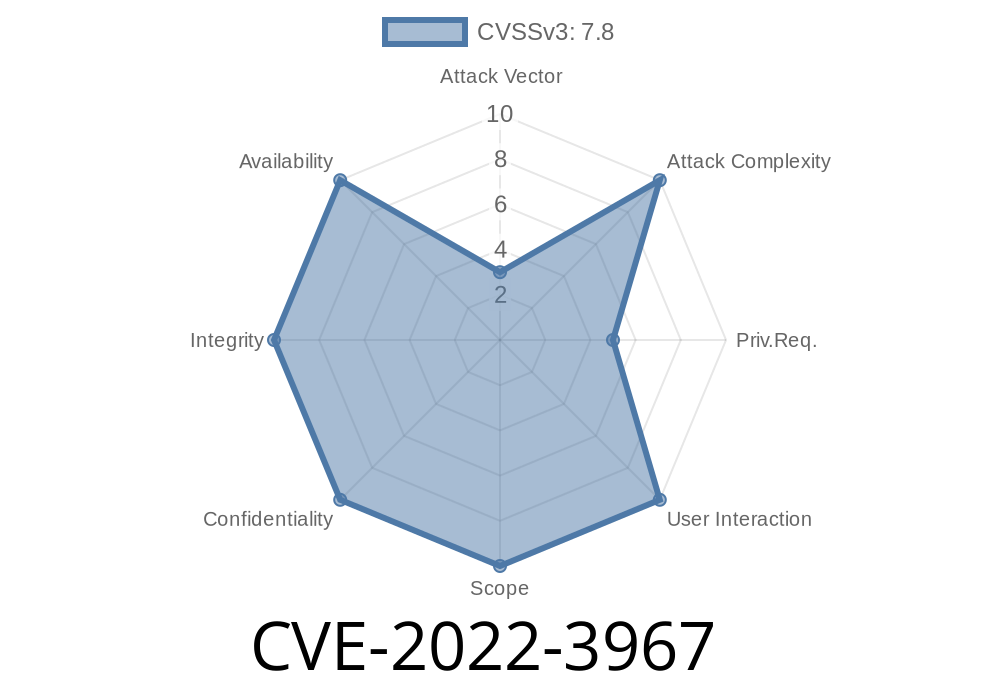
Vesta is vulnerable to CVE-2022-3967 and VDB-216215. Both of these vulnerabilities were found in the Vesta Control Panel.
Vulnerabilities found in Vesta Web Interface
A second critical vulnerability was found in Vesta's web interface. It is a flaw in sed Handler that results in remote code execution. The issue is located in the function main.sh: sed_handler: main.sh: line 543: [code] Sed_Handler::run_function(function_name, parameters) => function_name = 'sed_handler', parameters = 'set_config.sh?override_header=1' When exploitation is carried out, an attacker can send malicious data to the system. The issue can be addressed by patching the vesta-sed-handler-config.sh file. VDB-216216 is the identifier assigned to this vulnerability. The most severe vulnerability was found in Vesta Control Panel and is classified as critical. It is a flaw in the file sed_handler.sh. When the component is exploited, an attacker can perform remote code execution on the system. The issue can be addressed by patching the vesta-sed-handler-config.sh file. VDB-216215 is the identifier assigned to this vulnerability
Timeline
Published on: 11/13/2022 08:15:00 UTC
Last modified on: 11/17/2022 20:49:00 UTC