The researcher of the problem discovered by the RedTeam Pentesting security group states that the injectable sql code is as follows: Injectable sql code: [Select] -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user
SQL Injection in WordPress
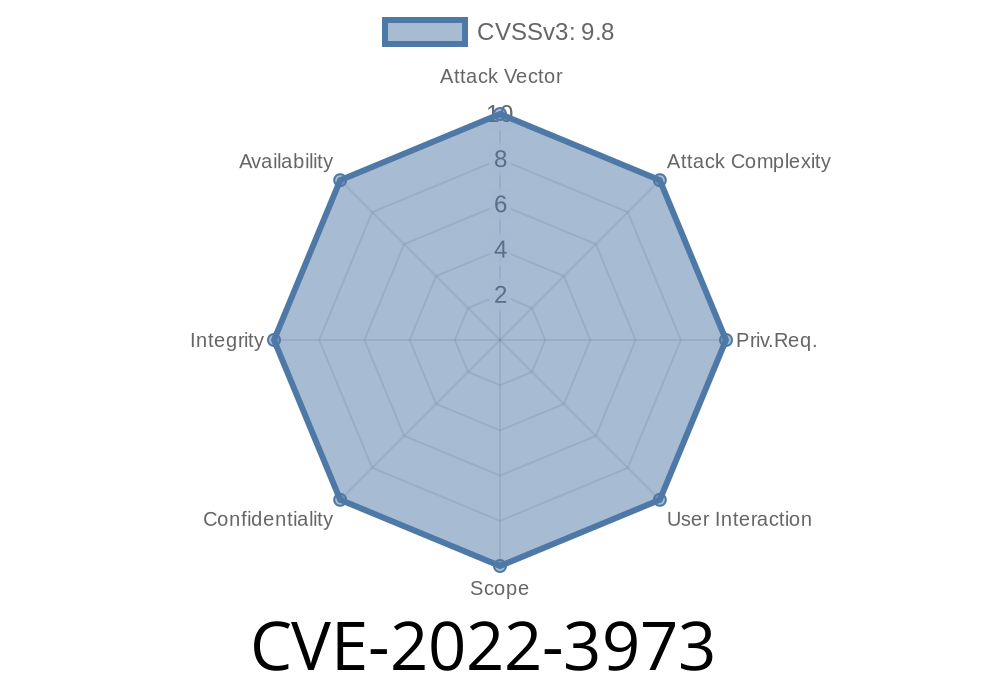
The last sql injection is an example of the vulnerability CVE-2022-3973. This vulnerability allows for SQL injections to occur when the user does not input valid credentials, but the site's login form is not designed properly.
The attacker has only to be able to inject two or three characters into the login form field in order for a successful attack to succeed. The following code demonstrates how this would work:
-- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root' -- -- uname/pass user 'root'
Note that each character must be entered as a hexadecimal value, which can be achieved by using "A2A5D6" and typing it on your keyboard.
Timeline
Published on: 11/13/2022 10:15:00 UTC
Last modified on: 11/17/2022 20:38:00 UTC