This issue was discovered by xStaCS. A patch was released by the VINASA team. Some details regarding the vulnerability have been provided by the vendor. The problem lies in the function filterAttr of the file vendor/vinades/nukeviet/Core/Request.php of the component Data URL Handler. The function is authorized to change the value of the argument attrSubSet. If an attacker modifies the value of attrSubSet, an external script can be executed. A remote attacker may exploit this vulnerability to launch cross site request forgery attacks.
VINASA Security Advisory:
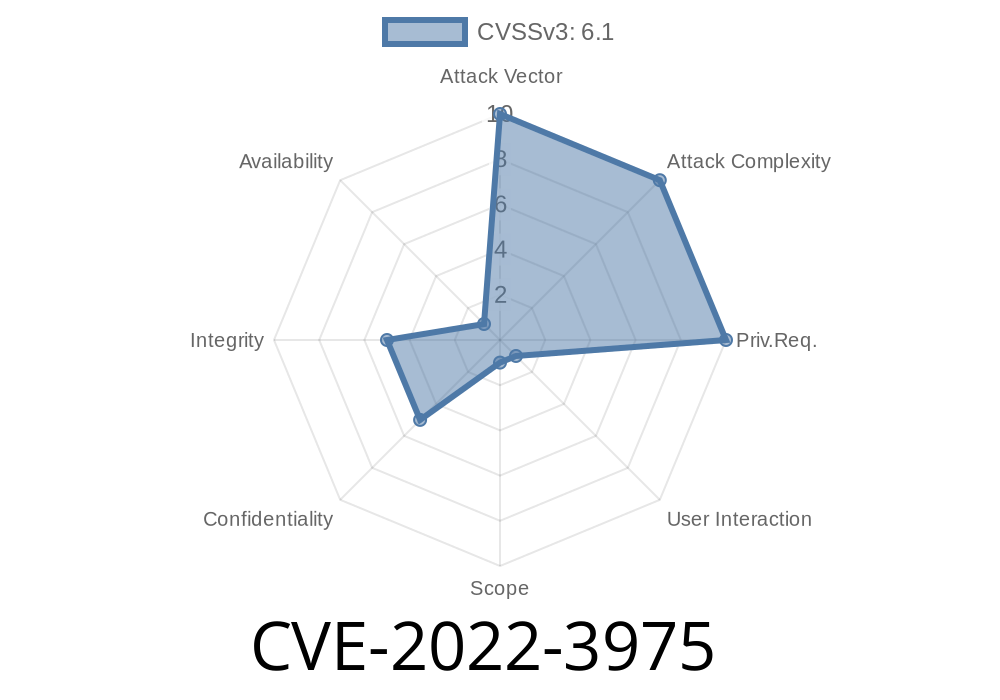
- CVSS: 4.3 (AV:N/AC:M/Au:NR/C:P/I:P/A:P)
- Reported to Vendor
- Vendor responded with patch
- Advisory published
Proof of Concept
VENDOR RESPONSE
The vendor released a patch to address this vulnerability. The VINASA team has acknowledged the issue, and the vendor has provided credit for the discovery to xStaCS.
VINASA Product
VINASA is a French company that specializes in the development of Data URL handler solutions.
Timeline
Published on: 11/13/2022 10:15:00 UTC
Last modified on: 11/18/2022 20:39:00 UTC