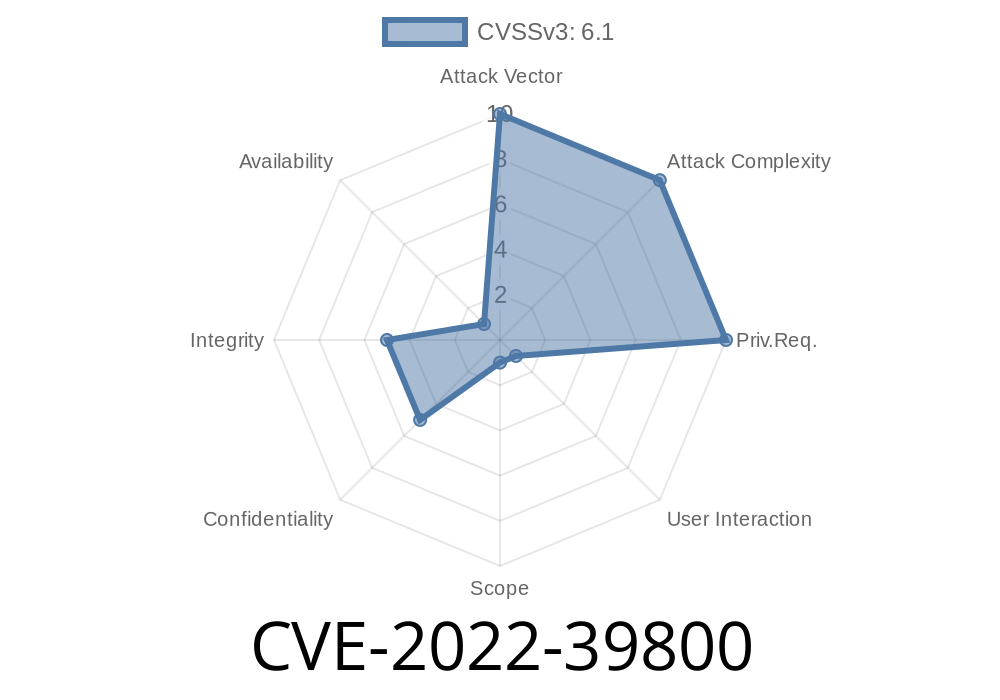
SAP BusinessObjects BI LaunchPad - versions 430 and 420 is exposed to cross-site request forgery (CSRF) due to failure to properly validate the request parameters before redirecting it to another page. An attacker can exploit this vulnerability to hijack the session or perform different actions on behalf of the legitimate users.
Redirecting to another URL through a CSRF attack can cause a significant impact to the integrity and confidentiality of the application.
Redirects can be used to bypass restrictions on accessing certain resources, such as a static page or an error page. An attacker can exploit this vulnerability to obtain access to restricted areas of the application or to perform actions that appear to come from the application. Redirects can be used to bypass restrictions on accessing certain resources, such as a static page or an error page. An attacker can exploit this vulnerability to obtain access to restricted areas of the application or to perform actions that appear to come from the application.
Redirects are HTTP URLs that take you to another URL. An attacker can exploit this vulnerability to redirect users from an insecure application to a malicious website. Redirects can be used to bypass restrictions on accessing certain resources, such as a static page or an error page. An attacker can exploit this vulnerability to obtain access to restricted areas of the application or to perform actions that appear to come from the application.
Pre-requisites
- The attacker must have knowledge of the target application.
- The attacker must be in a position to intercept requests between the application and the client.
- The target application does not require any special permissions to use redirects.
SAP BusinessObjects BI LaunchPad - versions 430 and 420 is exposed to cross-site request forgery (CSRF) due to failure to properly validate the request parameters before redirecting it to another page. An attacker can exploit this vulnerability to hijack the session or perform different actions on behalf of the legitimate users.
Redirecting to another URL through a CSRF attack can cause a significant impact to the integrity and confidentiality of the application.
How Does Cross Site Request Forgery (CSRF) Attacks occur?
The most common attack types are the following:
1. Impersonating a victim- CSRF can be used to hijack the session of another user. The attacker makes use of a vulnerable application that allows an unauthorized user to take control of the session and commandeer sensitive information, such as authentication cookies or authentication tokens.
2. Tampering with HTTP responses- If a request is made to an application and then redirected to another site (or vice versa), this is considered a CSRF attack. This attack can be performed by using an insecure application that redirects requests without validating them first, or through unsafe redirection methods on the website itself.
3. Hijacking sessions- Usually, CSRF attacks target stateful objects like sessions which maintain persistent data like cookies or authentication tokens. The attacker makes use of a vulnerable application that allows an unauthorized user to take control of the session and commandeer sensitive information, such as authentication cookies or authentication tokens.
Timeline
Published on: 10/11/2022 21:15:00 UTC
Last modified on: 10/12/2022 17:25:00 UTC