SAP 3D Visual Enterprise is maintained by SAP and is used by many companies to design and visualize their products. It is used by engineers, consultants, and designers in industries such as automotive, aerospace, medical, food, and beverage to design and visualize their products. As mentioned above, SAP 3D Visual Enterprise is a Microsoft application and can be attacked with advanced Microsoft exploitation techniques. Vulnerabilities in SAP 3D Visual Enterprise can be exploited to gain access to the system and perform various types of malicious activities. In the following section, we will discuss how to exploit SAP 3D Visual Enterprise for RCE vulnerability and how to receive a remote code execution. enduser summary This vulnerability can be exploited through targeted email messages with malicious attachments.
SAP 3D Visual Enterprise Vulnerability – Exploitation Steps
We will use the following steps to achieve this goal:
Step 1: Email the target with a malicious attachment.
Step 2: Craft an email that has a high level of trust in the victim.
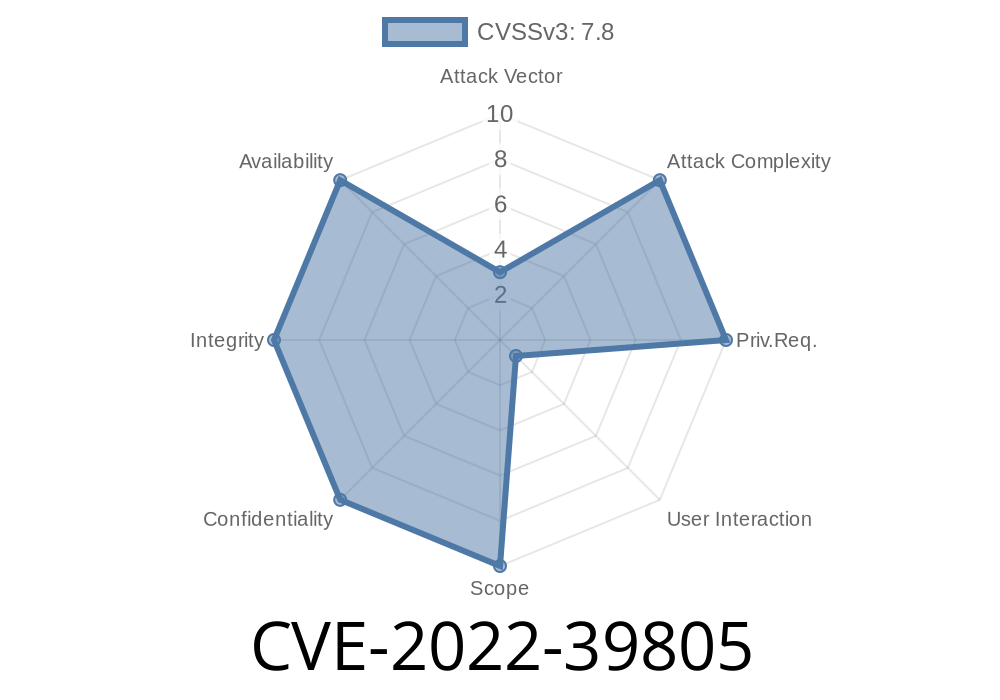
Step 3: Once successful, the attacker can get remote code execution on the system by exploiting CVE-2022-39805 HTTP flaw.
Step 4: The attacker can then access sensitive information or take full control of the system remotely.
The following is an example of a targeted email message with malicious attachments that contains instructions for exploitation of SAP 3D Visual Enterprise for RCE vulnerability.
Hello, I'm writing you from SAP BusinessObjects Business Intelligence and Analytics Solution Team, we are working on an update which includes some new features you might find interesting. This update is available in your area to try out and we would love for you to be part of it. To take advantage of this offer, please click on this link below to download and install the latest software release http://bit.ly/ss3dv2se01
How to exploit SAP 3D Visual Enterprise for RCE?
In order to exploit the vulnerability, the attacker needs access to the affected system. This can be achieved through spear phishing. In a spear phishing attack, an email is sent that appears to be from a known source but contains links or attachments that are malicious. The attacker then has to trick the intended victim into clicking on one of these links or attachments and opening them. Spear phishing attacks are successful because most people trust their friends and colleagues more than they do random people.
If successful, the attacker will gain access to the system and perform RCE, which enables him/her to take control of the system remotely. For example, if an attacker gains access to a SAP 3D Visual Enterprise system with this vulnerability via spear phishing, he/she can download any file available on the system, execute it locally or upload it in order to carry out other malicious activities such as stealing data, changing files permissions and so on. More information about different types of exploitation techniques can be found in other blog posts on this site
Exploitation of Remote Code Execution vulnerability in SAP 3D Visual Enterprise
This vulnerability allows remote code execution on the system. To exploit this vulnerability, the attacker sends a malicious attachment with an email message and the recipient opens the attachment.
The following screenshot shows an example of a vulnerable SAP 3D Visual Enterprise user account:
Operation
The following is a brief overview of how the vulnerability can be exploited.
- The attacker sends an email with an attachment to the target.
- The attachment contains malicious code that runs automatically when opened.
- This exploit uses CVE-2022-39805 and RCE vulnerability in SAP 3D Visual Enterprise to gain remote code execution on targeted systems.
Timeline
Published on: 10/11/2022 21:15:00 UTC
Last modified on: 10/12/2022 20:01:00 UTC