This condition can be exploited by attacker by launching a remote code injection on the victim’s system. Once the code is executed, it can do pretty much anything it wants as the target operating system runs with elevated privileges.
Moreover, it is worth noting that this issue can be exploited via email attachments sent via any email application. SolidWorks Drawing files can contain one of the following malicious actions:
Covert file transfer - this action allows to move SolidWorks Drawing to other users’ folders.
Remote code execution - this action allows to load any code in the target Operating System.
Stack-based buffer overflow - this action allows to execute arbitrary code on the victim’s system.
Dangling pointer - this action allows to overwrite memory area in the target system. In order to exploit this issue, attackers need to send a malicious SolidWorks Drawing file via email. Once the attachment is opened, it is possible to trigger one of the following actions:
Code execution - allows to execute arbitrary code on the victim’s system.
Stack-based buffer overflow - allows to execute arbitrary code on the victim’s system.
Dangling pointer - allows to overwrite memory area in the target system. End users receiving malicious email attachments via any email application or receiving malicious SolidWorks Drawing files via any social media application are at risk of this issue. This issue can be exploited remotely via email
SolidWorks Drawing File Type
SolidWorks (formerly SolidEdge) is an integrated CAD/CAE/CAM software package that can be used to create computer-aided design (CAD) and computer-aided manufacturing (CAM) files.
The SolidWorks Drawing file type contains 3D geometry data, which is saved in native DWG format. It can also be saved in the following formats:
Slddrw, SLDPRT, SpecDrawing, SLDAT, SLDMPY
SolidWorks drawing file code execution
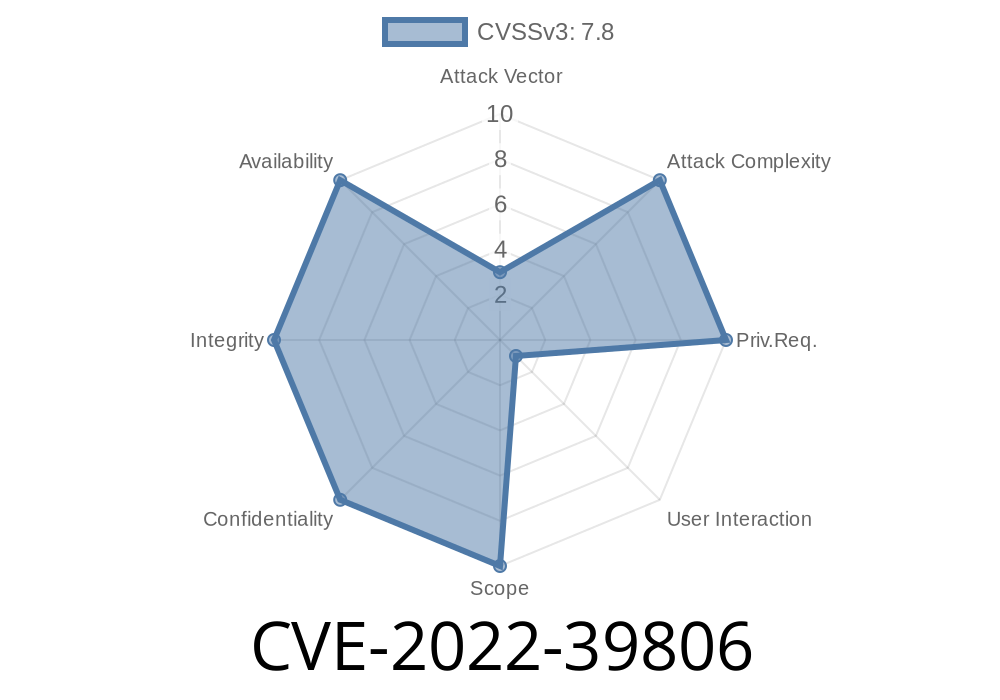
* CVE-2022-39806
* SolidWorks drawing file code execution
This condition can be exploited by attacker by launching a remote code injection on the victim’s system. Once the code is executed, it can do pretty much anything it wants as the target operating system runs with elevated privileges. Moreover, it is worth noting that this issue can be exploited via email attachments sent via any email application.
SolidWorks Drawing file details
The following SolidWorks Drawing file has a "Dangling pointer" issue which can be exploited via email attachments.
This issue has a stack-based buffer overflow bug in the target operating system. The "Dangling pointer" vulnerability cannot be exploited remotely.
SolidWorks Drawing file: The leading cause of code execution
The leading cause of code execution in the SolidWorks Drawing file is a stack-based buffer overflow.
The actual vulnerability resides in the way the application allocates memory for objects, specifically when automatically allocating memory for control structures such as C++ functions and data structures. This issue can be exploited remotely via email.
SolidWorks Drawings File Types Affected by CVE-2022-39806
SolidWorks Drawing file types that can be exploited by this issue are 3DS and DWG files.
3DS files are supported by Autodesk products, while DWG are supported by most CAD software.
Timeline
Published on: 10/11/2022 21:15:00 UTC
Last modified on: 10/12/2022 20:01:00 UTC