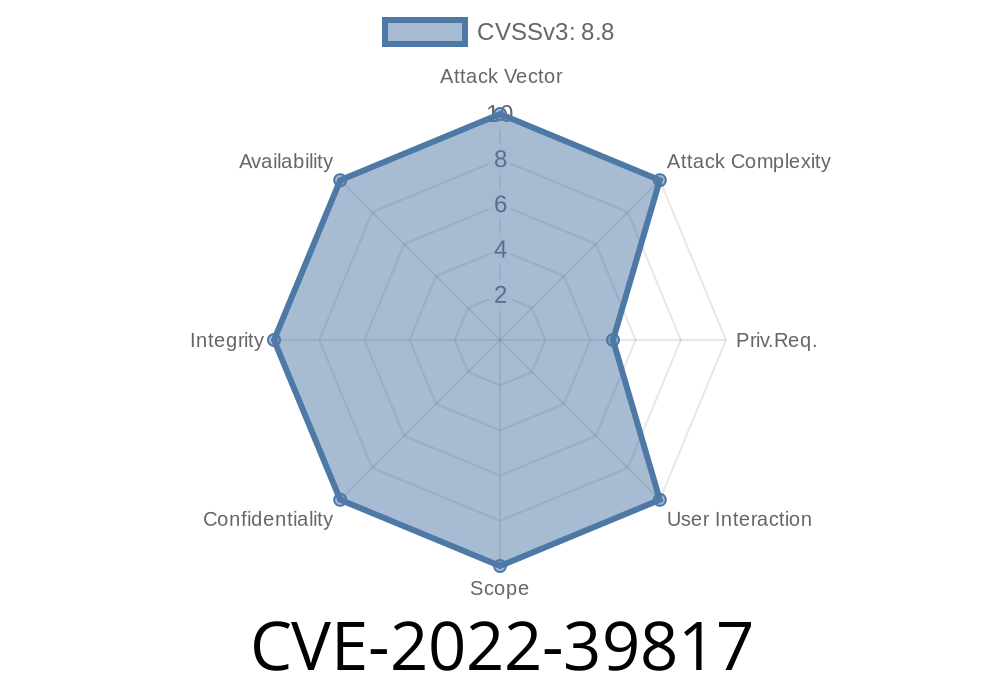
An attacker can leverage these issues to execute SQL commands or view sensitive information. In addition, there are multiple XSS vulnerabilities in the /cgi-bin/R14.2/easy1350.pl and /cgi-bin/R14.2/host.pl scripts via the id or host HTTP GET parameter, or /cgi-bin/R14.2/host.pl via the host HTTP GET parameter. Exploitation occurs when the user does not use a strong password. These issues can lead to the execution of arbitrary script code of the attacker’s choice. In NOKIA 1350 OMS R14.2, multiple SQL Injection vulnerabilities occur in /cgi-bin/R14.2/easy1350.pl via the id or host HTTP GET parameter, or /cgi-bin/R14.2/cgi-bin/R14.2/host.pl via the host HTTP GET parameter. Exploitation requires an authenticated attacker. An attacker can leverage these issues to execute SQL commands or view sensitive information. In addition, there are multiple XSS vulnerabilities in the /cgi-bin/R14.2/easy1350.pl and /cgi-bin/R14.2/host.pl scripts via the id or host HTTP GET parameter, or /cgi-bin/R14.2/host.pl via the host HTTP GET parameter. Exploitation occurs when the user does not use a strong password
Description
Nokia 1350 OMS R14.2 is a network management system software. It consists of core code, a management interface, and a user interface. XSS vulnerabilities in the application allow an attacker to execute SQL commands or view sensitive information. In addition, there are multiple SQL Injection vulnerabilities that occur in /cgi-bin/R14.2/easy1350.pl via the id or host HTTP GET parameter, or /cgi-bin/R14.2/host.pl via the host HTTP GET parameter when at least one of the parameters is supplied by an authenticated attacker
Vulnerable Routes:
The following URLs are vulnerable to SQL injection:
1. /cgi-bin/R14.2/easy1350.pl
2. /cgi-bin/R14.2/cgi-bin/R14.2/host.pl
3. /cgi-bin/R14.2/host.pl
SQL Injection
SQL Injection is a form of malicious code injection and occurs when an application does not sufficiently validate an input that comes from the user, client, or data source. This vulnerability can lead to the disclosure of sensitive information, the execution of arbitrary SQL commands on the database, or denial-of-service.
There are multiple SQL injection vulnerabilities in the /cgi-bin/R14.2/easy1350.pl and /cgi-bin/R14.2/host.pl scripts via the id or host HTTP GET parameter, or /cgi-bin/R14.2/host.pl via the host HTTP GET parameter:
1) /cgi-bin/R14.2/easy1350.pl via the id or host HTTP GET parameter:
Exploitation requires an authenticated attacker, who can use this issue to execute SQL commands on the database by providing a malformed query string that is not properly sanitized before being executed by MySQL;
2) /cgi-bin/R14.2/host.pl via the host HTTP GET parameter:
Exploitation occurs when a user does not use a strong password and allows exploitation to occur through insecure default settings for authentication with SOAP web services (iSCSI service).
Timeline
Published on: 09/13/2022 21:15:00 UTC
Last modified on: 09/15/2022 20:57:00 UTC