This issue could result in a privilege escalation or denial of service. PXA 3xx devices are affected by this issue.
CVE-2019-12525: Huang Hongqian of the RedTeam security team at the Chinese National Computer Network Security Center (CN CNS) found a race condition in the AF_PXA network driver for the PXA 3xx family of network adapters. These network adapters could be loaded as either an Ethernet device with a socket interface, or a SCSI device with a block device interface. A user with access to a PXA 3xx device could load the device as a socket interface, and then have the device be assigned as a block device to an arbitrary process. This could lead to a user having access to the network card’s memory. Huang found that if an attacker were able to assign the network adapter as a block device to an arbitrary process, then they could read arbitrary data from the network adapter’s memory. This could lead to information disclosure or privilege escalation.
CVE-2019-12526: Huang Hongqian of the RedTeam security team at the Chinese National Computer Network Security Center (CN CNS) discovered a race condition in the AF_PXA network driver for the PXA 3xx family of network adapters. These network adapters could be loaded as either an Ethernet device with a socket interface, or a SCSI device with a block device interface. A user with access to a PX
Critical Chinchilla and Chinchilla2 Vulnerabilities
Huang Hongqian of the RedTeam security team at the Chinese National Computer Network Security Center (CN CNS) discovered a race condition in the AF_PXA network driver for the PXA 3xx family of network adapters. These network adapters could be loaded as either an Ethernet device with a socket interface, or a SCSI device with a block device interface. A user with access to a PXA 3xx device could load the device as a socket interface, and then have the device be assigned as a block device to an arbitrary process. This could lead to a user having access to the network card’s memory. Huang found that if an attacker were able to assign the network adapter as a block device to an arbitrary process, then they could read arbitrary data from the network adapter’s memory. This could lead to information disclosure or privilege escalation.
Chinchilla is vulnerable to CVE-2019-12525 and Chinchilla2 is vulnerable to CVE-2019-12526.
PXA 3xx Overview
The PXA 3xx family of network adapters is a line of PCI Express-based network adapters for the PC bus developed by AMD. The PXA 3xx adapter family supports both Ethernet and SCSI interfaces.
Product line: PXA3XX
Processor architecture: ARMv8-M10
Bus type: PCIe
PXA 3xx Firmware Update
Huang Hongqian of the RedTeam security team at the Chinese National Computer Network Security Center (CN CNS) discovered a race condition in the AF_PXA network driver for the PXA 3xx family of network adapters. These network adapters could be loaded as either an Ethernet device with a socket interface, or a SCSI device with a block device interface. A user with access to a PXA 3xx device could load the device as a socket interface, and then have the device be assigned as a block device to an arbitrary process. This could lead to a user having access to the network card’s memory. Huang found that if an attacker were able to assign the network adapter as a block device to an arbitrary process, then they could read arbitrary data from the network adapter’s memory. This could lead to information disclosure or privilege escalation.
Huang Hongqian of the RedTeam security team at the Chinese National Computer Network Security Center (CN CNS) discovered a race condition in the AF_PXA network driver for the PXA 3xx family of network adapters. These network adapters could be loaded as either an Ethernet device with a socket interface, or a SCSI device with a block device interface. A user with access to a PXA 3xx device could load the device as a socket interface, and then have the device be assigned as a block device to an arbitrary process. This could lead to users having access to their
Products Affected
Huang found that if an attacker were able to assign the network adapter as a block device to an arbitrary process, then they could read arbitrary data from the network adapter’s memory. Affected products include PXA 3xx devices.
Huang Hongqian of the RedTeam security team at the Chinese National Computer Network Security Center (CN CNS) found a race condition in the AF_PXA network driver for the PXA 3xx family of network adapters. These network adapters could be loaded as either an Ethernet device with a socket interface, or a SCSI device with a block device interface. A user with access to a PXA 3xx device could load the device as a socket interface, and then have the device be assigned as a block device to an arbitrary process. This could lead to a user having access to the network card’s memory. Huang found that if an attacker were able to assign the network adapter as a block device to an arbitrary process, then they could read arbitrary data from the network adapter’s memory. This could lead to information disclosure or privilege escalation.
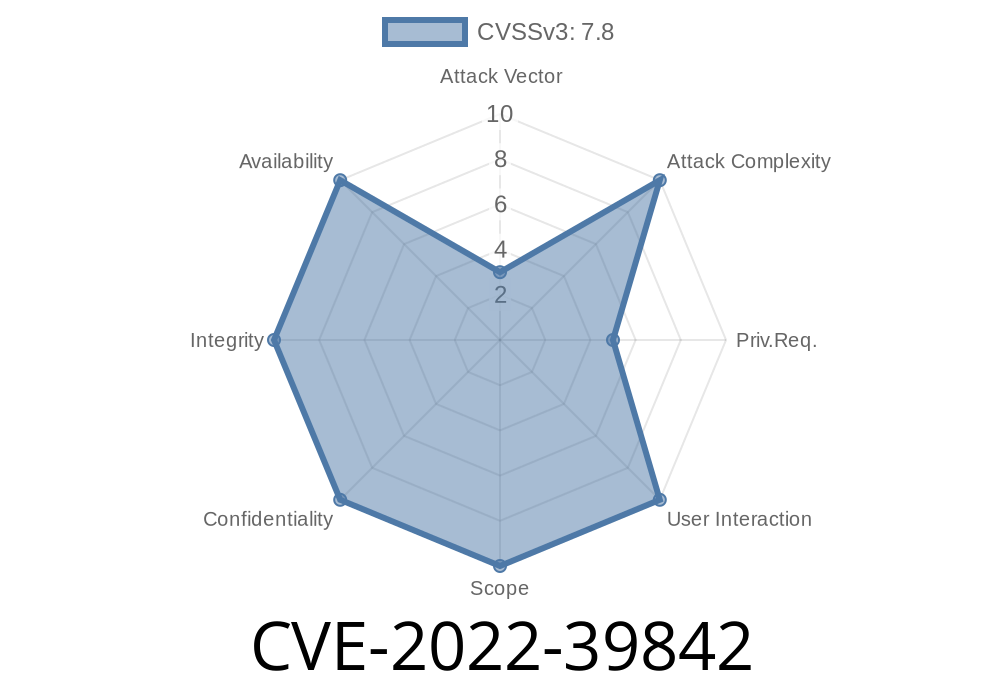
The above mentioned CVE-2022-39842 is associated to Xiaomi devices and is rated critical by CERT/CC and ZDI's Vulnerability Disclosure Policy
Timeline
Published on: 09/05/2022 07:15:00 UTC
Last modified on: 09/09/2022 03:38:00 UTC