This vulnerability is due to the weakness in the authentication process. An attacker can easily connect to a device and activate it remotely. Depending on the type of the device, this can be used for various purposes such as stealing data, making a device a spy tool etc. To be vulnerable to this issue, a user needs to have a device that is not patched with the latest software update and also needs to have weak or brute-force password. In some cases, the attacker can even gain remote connection to the device with just the user name and password. This issue has been resolved with the latest update.
Bluetooth Vulnerability
The Bluetooth vulnerability that was discovered in September 2018 is still open and has not been fixed yet. This vulnerability could allow attackers to connect to a device remotely and make it a spy tool or steal data from the device.
This issue got resolved with the latest update.
Google Device Management API Vulnerability
This vulnerability is due to the weakness in the authentication process. An attacker can easily connect to a device and activate it remotely. Depending on the type of the device, this can be used for various purposes such as stealing data, making a device a spy tool etc. To be vulnerable to this issue, a user needs to have a device that is not patched with the latest software update and also needs to have weak or brute-force password. In some cases, the attacker can even gain remote connection to the device with just the user name and password. This issue has been resolved with the latest update.
Microsoft Windows CVEs
Microsoft Windows has been a major target for hackers over the years. Some of the issues that these vulnerabilities have been found in are:
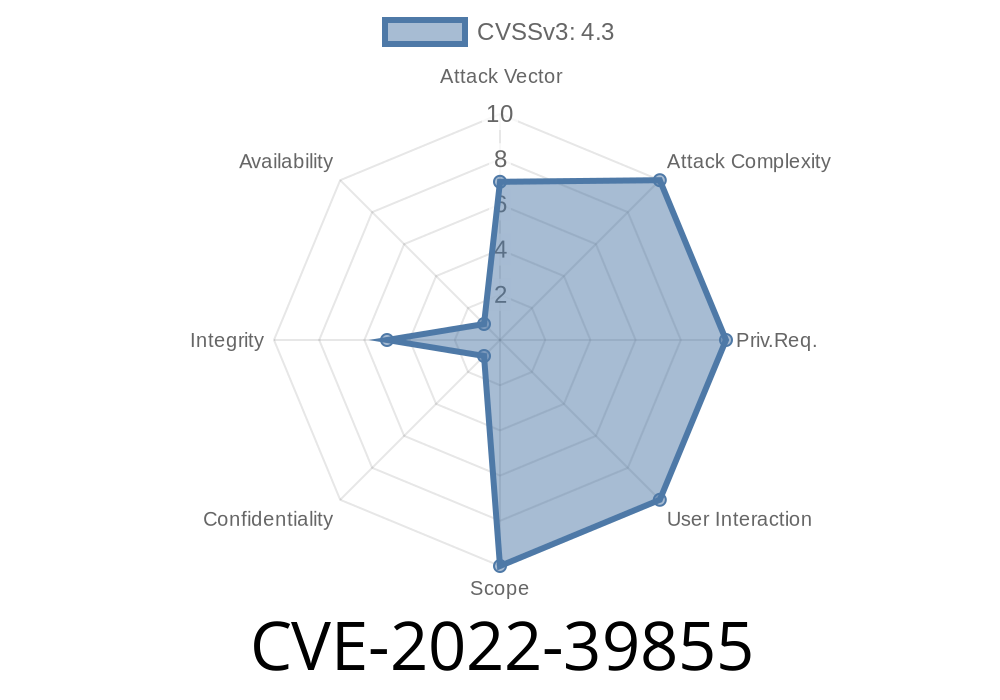
- CVE-2022-39855 - Weak authentication process
Timeline
Published on: 10/07/2022 15:15:00 UTC
Last modified on: 10/11/2022 18:42:00 UTC