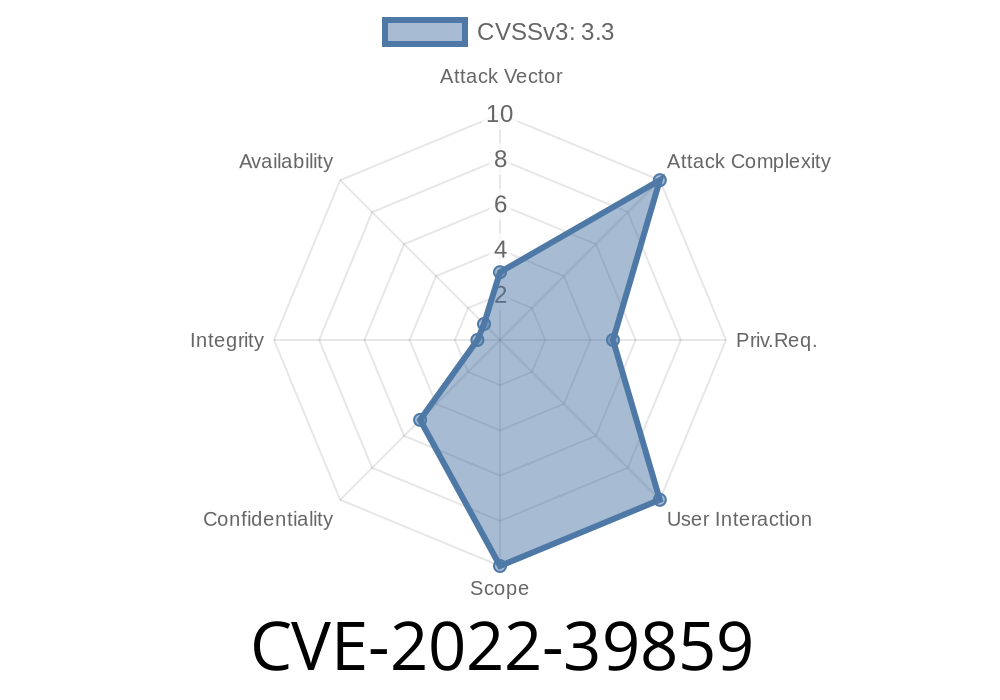
Attackers can trick users to send them self-destructing text messages by sending them links to self-destructing applications or links to UphSms(SMS) self-destructing applications. UPHELPER library before version 3.0.12 does not have any feature for handling implicit intents. The libUphSms library prior to version 3.0.12 does not have any feature for handling implicit intents. UphSms is an SMS self-destructing application, which sends the user an SMS with a link to a self-destructing application once the user sends out the first SMS. Once clicked by the user, the link would take the user to the attacker’s website. Due to this patched UPHELPER library, attackers can exploit this vulnerability using implicit intents to get the user to click on malicious links sent by the attacker. In order to exploit this vulnerability, an attacker must know the exact location of the UPHELPER library on the targeted device. This can be achieved by installing the UPHELPER library on a device and then sending a malicious link to the targeted device. The user would then be forced to open the malicious link and would be exposed to the attack. In order to exploit this vulnerability, an attacker must know the exact location of the UPHELPER library on the targeted device. This can be achieved by installing the UPHELPER library on a device and then sending a malicious link to
Vulnerability Details
Attackers can trick users to send them self-destructing text messages by sending them links to self-destructing applications or links to UphSms(SMS) self-destructing applications. UPHELPER library before version 3.0.12 does not have any feature for handling implicit intents. The libUphSms library prior to version 3.0.12 does not have any feature for handling implicit intents. UphSms is an SMS self-destructing application, which sends the user an SMS with a link to a self-destructing application once the user sends out the first SMS. Once clicked by the user, the link would take the user to the attacker’s website. Due to this patched UPHELPER library, attackers can exploit this vulnerability using implicit intents to get the user to click on malicious links sent by the attacker. In order to exploit this vulnerability, an attacker must know the exact location of the UPHELPER library on the targeted device. This can be achieved by installing the UPHELPER library on a device and then sending a malicious link to the targeted device
Timeline
Published on: 10/07/2022 15:15:00 UTC
Last modified on: 10/07/2022 21:11:00 UTC