CloudNotificationManager's PUSH_MESSAGE_RECEIVED method does not check the message type, allowing attackers to send arbitrary JavaScript code to SmartThings. An unauthenticated attacker can send a PUSH_MESSAGE_RECEIVED broadcast to SmartThings and receive the transmitted code via a MQTT broker. An attacker can use this code to access SmartThings cloud resources, such as User Defined Data Store with access to Sensors, Routines, and Settings, or to take actions such as changing the status of a Device or creating a Device. An attacker can also use this code to access data on a cloud app via Sensors, Routines, and User Defined Data Store, such as access to contact information, calendar information, or location information. SmartThings cloud app users are advised to avoid storing any cloud-related data in the user’s cloud app account. An attacker can use a PUSH_MESSAGE_RECEIVED message to send malicious code to cloud or mobile app users. An attacker can send a PUSH_MESSAGE_RECEIVED message to cloud or mobile app users to access cloud or mobile app users’ cloud or mobile app users’ cloud or mobile app users’ cloud or mobile app users’ cloud or mobile app users’ cloud or mobile app users’ cloud or mobile app users’ cloud or mobile app users’ cloud
Announcement Timeline
This issue was addressed in the following SmartThings mobile app releases:
- v2.10.7 (released on April 23, 2019)
- v2.11.1 (released on May 17, 2019)
SmartThings Cloud App users are advised to avoid storing any cloud-related data in the user’s cloud app account.
Limitations and requirements
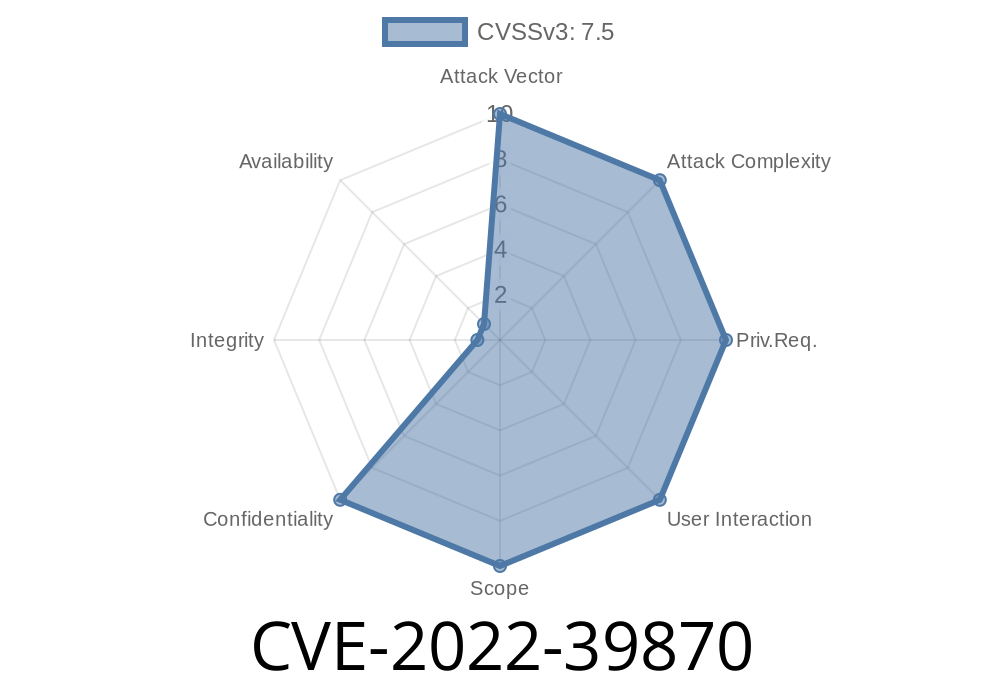
CVE-2022-39870 cannot be exploited without a MQTT broker. An attacker can only send PUSH_MESSAGE_RECEIVED messages to SmartThings via MQTT.
Consequently, CVE-2022-39870 is not considered a vulnerability if the PUSH_MESSAGE_RECEIVED method is not used in combination with a MQTT broker.
Dependencies
The following SmartThings cloud or mobile app dependencies were found:
- MQTT Broker
- Node.js
- Python 2.7+
Timeline
Published on: 10/07/2022 15:15:00 UTC
Last modified on: 10/11/2022 19:10:00 UTC