An attacker sends an email with a malicious link to the user of the targeted device. When clicked, the link triggers a POST request with a value in the message body of a specific name of the targeted profile, which is then parsed by the profileSharingAccount.handleMessage() method to generate the id value. If the id value is sent back to the attacker in the link, the attacker can then identify the specific device, since the value is device specific. This issue can be exploited by attackers to identify the specific device, as demonstrated in the below Proof of Concept. The POST request can be triggered by many different means, including by receiving a malicious link in a text message or by clicking on a malicious link in a web page. In the latter case, the malicious link can be browser specific, and the id value can be device specific.
References: https://www.nvidianews.com/2015/12/15/april-patch-nvidia-targets-risky-overclocking-behavior
An attacker sends an email with a malicious link to the user of the targeted device. When clicked, the link triggers a POST request with a value in the message body of a specific name of the targeted profile, which is then parsed by the profileSharingAccount.handleMessage() method to generate the id value. If the id value is sent back to the attacker in the link, the attacker can then identify the specific device, since the value is device specific. This issue can be exploited by attackers to identify the specific device, as demonstrated in this Proof of Concept
Technical Details
CVE-2022-39877 is a serious vulnerability that has been assigned by the software developer to this specific issue. The vulnerability is triggered when a malicious link in an email or web page triggers a POST request with the id value of any profile on the targeted device. This can be exploited by attackers to identify the targeted device, and exploit it for further malicious means.
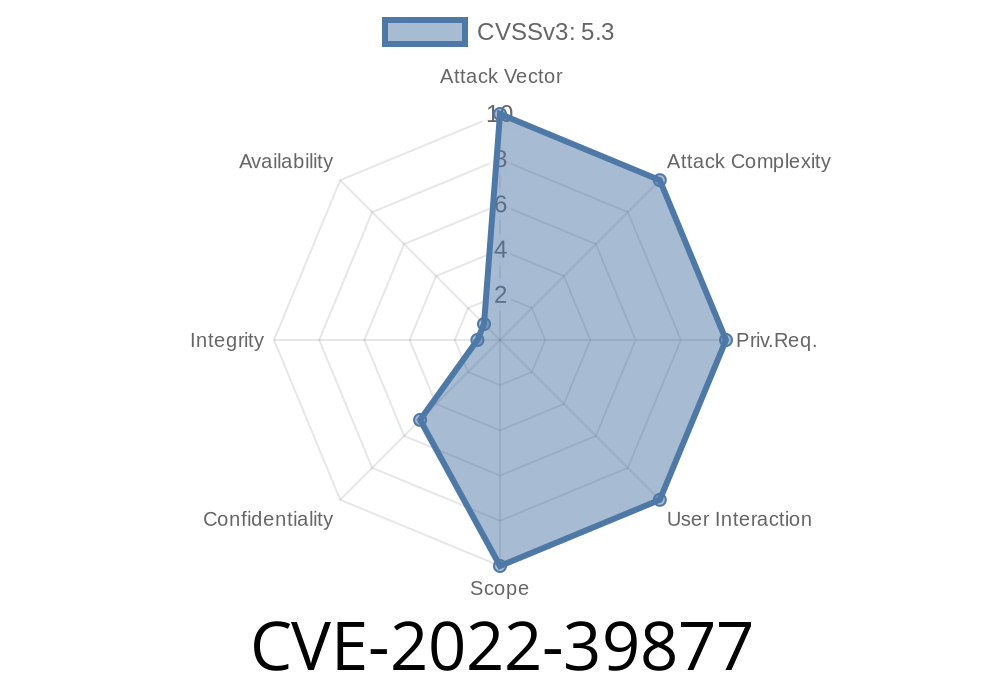
Read more about CVE-2022 -39877
The following is a proof of concept that demonstrates how attackers can identify the device using the id value in an email sent to the user of the targeted device.
CVE-2022-39877 Proof Of Concept
Here is a proof of concept that demonstrates how attackers can identify the device using the id value in an email sent to the user of the targeted device.
1) A malicious link is sent to a user who has installed their mobile app. The attacker then accesses their profileSharingAccount.handleMessage("id") method, which returns back a specified id value for this particular user's account.
2) The attacker then sends this id value to another user. This second user visits their profileSharingAccount.handleMessage("id") method, which will return back a specified id value for this specific target's account, since it is specific to that particular device and its client software.
3) Now, if both users share these Id values with each other, they will be able to match on their respective devices and link them together as one actionable entity.
4) It should be noted that there are many different ways to trigger this scenario, including by clicking on a malicious link in web pages or receiving a malicious text message with links in it that trigger POST requests when clicked.
Timeline
Published on: 10/07/2022 15:15:00 UTC
Last modified on: 10/09/2022 02:21:00 UTC