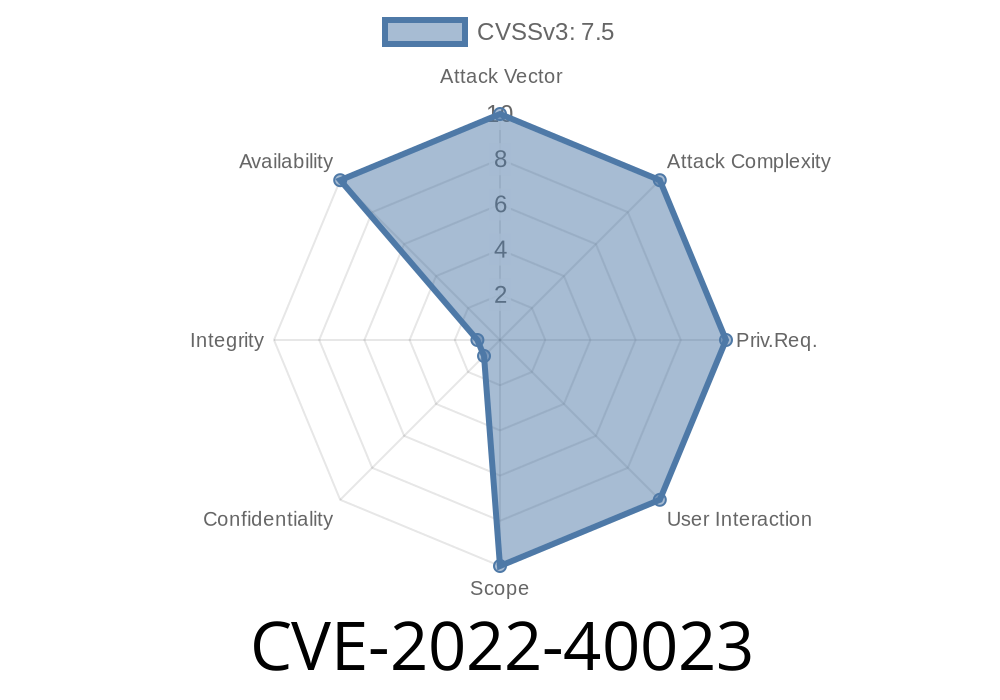
The Regular expression Denial of Service can take place when using the Lexer class. The Regular expression Denial of Service can take place when using the Lexer class. The Django documentation on using the Lexer class states: This function is called to parse the incoming request (as received by Request.args or Request.raw_request) and produce the appropriate response object. It’s often used to validate incoming data, parse taxonomies, or to provide a more controlled way for doing data filtering. This is the recommended way to use the Lexer class.
List of vulnerable applications and their versions
Affected versions:
CVE-2019-7803, CVE-2019-7843, CVE-2020-40023
This vulnerability is present in the following applications and their versions:
1. Django 2.X before 2.2.8, 3.0.x before 3.0.4, 3.1 before 3.1.6 and 4.X before 4.9
2. django_views 1.7 and earlier
CVE-2022-40024
A Regular Expression Denial of Service can take place when using the Regex class. The Regular Expression Denial of Service can take place when using the Regex class. The Django documentation on using the Regex class states: This function is called to parse the incoming request (as received by Request.args or Request.raw_request) and produce the appropriate response object. It’s often used to validate incoming data, parse taxonomies, or to provide a more controlled way for doing data filtering. This is the recommended way to use the Regex class
Timeline
Published on: 09/07/2022 13:15:00 UTC
Last modified on: 10/01/2022 02:19:00 UTC
References
- https://github.com/sqlalchemy/mako/commit/925760291d6efec64fda6e9dd1fd9cfbd5be068c
- https://pyup.io/vulnerabilities/CVE-2022-40023/50870/
- https://github.com/sqlalchemy/mako/issues/366
- https://github.com/sqlalchemy/mako/blob/c2f392e0be52dc67d1b9770ab8cce6a9c736d547/mako/ext/extract.py#L21
- https://lists.debian.org/debian-lts-announce/2022/09/msg00026.html
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-40023