When a user browses to malicious or third-party web-based file or enters the directory structure (i.e., /directory/filename) that is under the control of a remote attacker and enters a value in the field of a PHP form, then this flaw can be exploited to execute arbitrary code on the system of an affected device. This can be done by uploading a PHP file with a directive such as allow_url_include enabled from a remote location. If a user visits a malicious or third-party website, then it is possible for an attacker to submit a specially crafted PHP code to the Simple College Website v1.0 and to execute it in the web server memory. The directive allow_url_include may be set to On, in which case the web server will allow remote code execution when a user accesses a remote file via a web link. An attacker can upload a PHP file with a directive such as allow_url_include enabled from a remote location. If a user visits a malicious or third-party website, then it is possible for an attacker to submit a specially crafted PHP code to the Simple College Website v1.0 and to execute it in the web server memory. The directive allow_url_include may be set to On, in which case the web server will allow remote code execution when a user accesses a remote file via a web link.
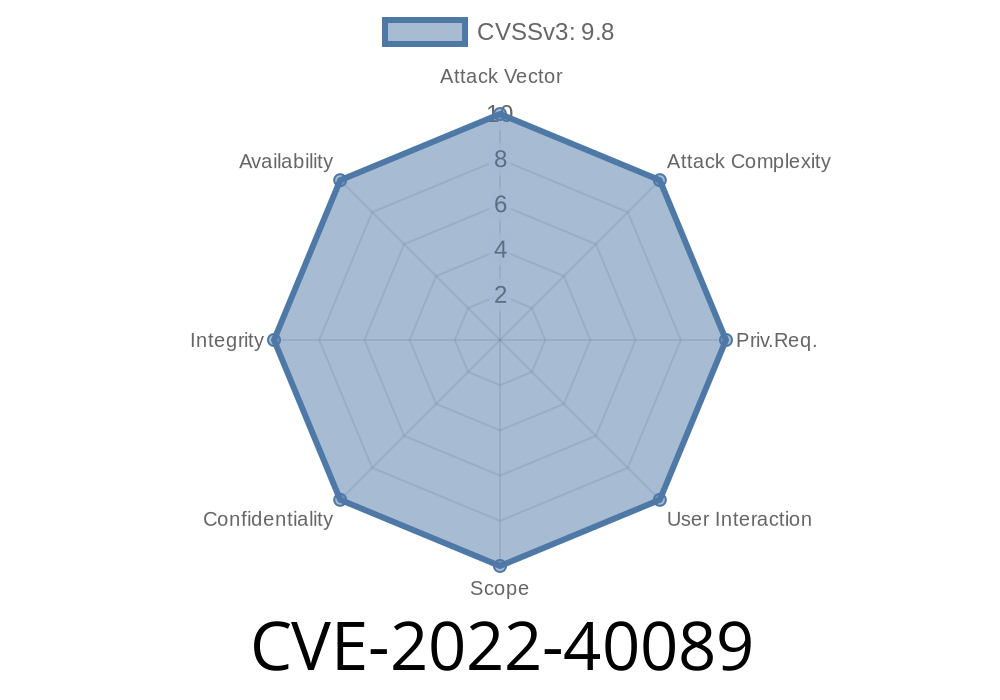
Simple College Website Vulnerability
This vulnerability can be used to execute arbitrary code on the system of an affected device. This flaw can occur when a user browses to malicious or third-party web-based file or enters the directory structure (i.e., /directory/filename) that is under the control of a remote attacker and enters a value in the field of a PHP form created by an application such as Simple College Website v1.0. The affected application may not use any validation or sanitization routines on user input before it is passed to a remote location. If a user visits a malicious or third-party website, then it is possible for an attacker to submit modified PHP code to the application and execute it in the web server memory.
Exploit Proof-of-Concept
The first exploit code was discovered on April 7, 2015. The exploit code appears to be written in the PHP language and allows remote code execution.
Exploiting the flaw
It is possible for attackers to exploit the flaw by submitting a specially crafted PHP code to the Simple College Website v1.0 via a web link and to execute it in the web server memory.
The following are common vectors of attack:
- A user visits a malicious or third-party website where an attacker has uploaded a PHP file with a directive such as allow_url_include enabled from a remote location.
- An attacker submits a specially crafted PHP code (e.g., "?x=w3m%20/etc/passwd") that contains "/etc/passwd" as the path and executes it in the web server memory
Vulnerability Equation
This flaw can be exploited to execute arbitrary code on the system of an affected device by uploading a PHP file with a directive such as allow_url_include enabled from a remote location. If a user visits a malicious or third-party website, then it is possible for an attacker to submit a specially crafted PHP code to the Simple College Website v1.0 and to execute it in the web server memory. The directive allow_url_include may be set to On, in which case the web server will allow remote code execution when a user accesses a remote file via a web link. An attacker can upload a PHP file with a directive such as allow_url_include enabled from a remote location. If a user visits a malicious or third-party website, then it is possible for an attacker to submit a specially crafted PHP code to the Simple College Website v1.0 and to execute it in the web server memory. The directive allow_url_include may be set to On, in which case the web server will allow remote code execution when a user accesses a remote file via a web link.
Timeline
Published on: 09/22/2022 22:15:00 UTC
Last modified on: 09/26/2022 14:33:00 UTC
References
- https://www.sourcecodester.com/sites/default/files/download/oretnom23/simple-college-website.zip
- https://www.sourcecodester.com/php/14548/simple-college-website-using-htmlphpmysqli-source-code.html
- https://gowthamaraj-rajendran.medium.com/simple-college-website-1-0-rfi-cff8d827572e
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-40089