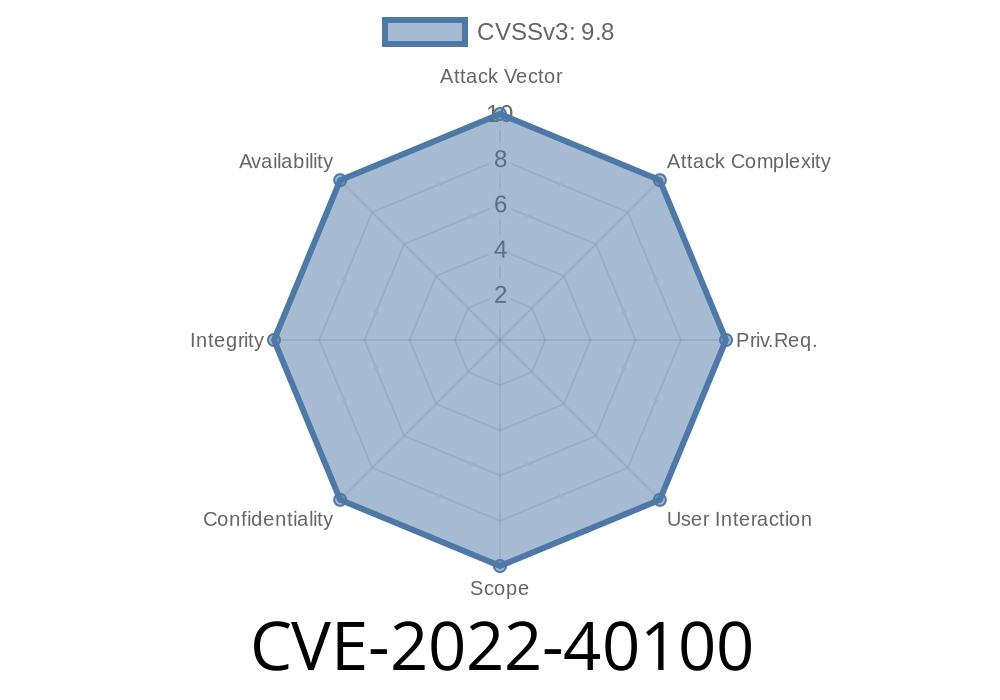
If a user were to click on a malicious link or open a malicious file on the system, an attacker could inject commands into the vulnerable application and execute them with the rights of the current user.
Tenda i9 v1.0.0.8(3828) is installed on remote unauthorized system via the following vectors: - Vishing - Malicious attachments in email - Downloading and installing a malicious software.
CVE-2018-10982 - Command Injection Remote Code Execution Vulnerability in Tenda i9 Remotely exploitable command injection vulnerability allows an attacker to execute arbitrary code on the system as the user that owns the software. This attack vector can be exploited through web-based application that allows file upload. An attacker could upload a malicious file that could exploit this vulnerability and run arbitrary code on the system as the user that owns the software.
CVE-2018-10983 - Unauthenticated Command Injection Vulnerability in Tenda i9 Remotely exploitable unauthenticated command injection vulnerability allows an attacker to execute arbitrary code on the system as the user that owns the software. This attack vector can be exploited through web-based application that allows file upload. An attacker could upload a malicious file that could exploit this vulnerability and run arbitrary code on the system as the user that owns the software.
CVE-2018-10981 - Authentication Bypass Vulnerability in Tenda i9 Remotely exploitable authentication bypass vulnerability allows an
Vulnerable Package
Tenda i9 v1.0.0.8(3828) is installed on remote unauthorized system via the following vectors: - Vishing - Malicious attachments in email - Downloading and installing a malicious software.
Tenda i9 Firmware and Vulnerability Types
In this report, these are some of the vulnerabilities in Tenda i9 firmware and how they can be exploited:
- Unauthenticated Command Injection Vulnerability in Tenda i9 Remotely exploitable unauthenticated command injection vulnerability allows an attacker to execute arbitrary code on the system as the user that owns the software. This attack vector can be exploited through web-based application that allows file upload. An attacker could upload a malicious file that could exploit this vulnerability and run arbitrary code on the system as the user that owns the software.
- Authentication Bypass Vulnerability in Tenda i9 Remotely exploitable authentication bypass vulnerability allows an attacker to execute arbitrary commands as another user on your network or remotely. This attack vector can be exploited through web-based application that allows file upload. An attacker could upload a malicious file that could exploit this vulnerability and run arbitrary commands as another user on your network or remotely.
Timeline
Published on: 09/23/2022 19:15:00 UTC
Last modified on: 09/27/2022 04:44:00 UTC