When /bin/boa is called, it will call the function pointed to by 'Fastcgi_parameters' which accepts user-supplied data via 'arg_v[]' function. If the data passed to 'Fastcgi_parameters' is larger than the allocated buffer, it will cause a Buffer Overflow and consequently, remote code execution.
**
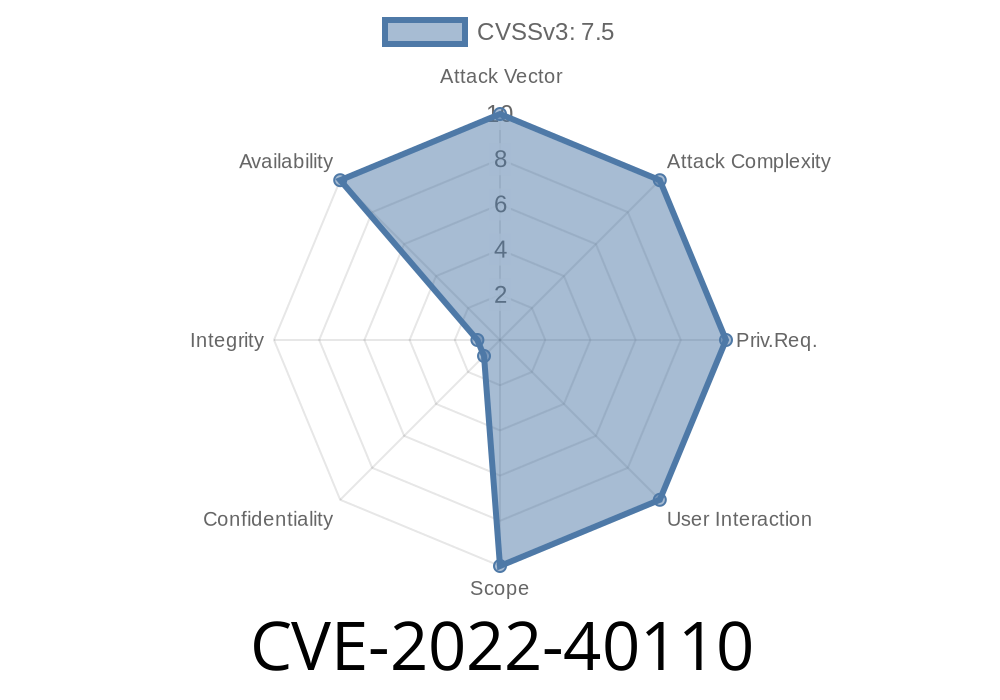
Fixed in version VERSION
Vulnerability Scenario
The scenario below is an example of a situation where a vulnerability could be exploited.
Consider the following scenario:
A web application written in PHP is performing user authentication. If the username and password are incorrect, the application will not allow further access to the site.
An example of this situation is when an attacker sends in a request that contains data larger than what is allocated for the 'arg_v[]' function parameter. This causes a buffer overflow which ultimately results in remote code execution. In this case, attackers can bypass security measures by exploiting this vulnerability.
Risk Assessment & Recommendation
This vulnerability is rated as medium because a remote attacker could exploit it to gain remote code execution. If exploited, this vulnerability would allow the attacker to access data on the target system, or even escalate privileges.
**
This vulnerability is present in all versions of boa prior to 1.0.7 and was discovered by Chris Baker
Solution
Many modern programming languages, including PHP, have mitigations against this type of exploitation. One mitigation is to call the function that accepts user-supplied data at a later time. This can be accomplished by using a return statement in place of the 'Fastcgi_parameters' function in a vulnerable application.
Timeline
Published on: 09/06/2022 17:15:00 UTC
Last modified on: 09/08/2022 21:24:00 UTC