In V18, this issue was partially patched by changing the "f" parameter to '/' in CssEditor. By abusing the path traversal vulnerability, authenticated attackers can inject the code of their choice into the system.
In addition, the update also fixed the XSS vulnerability via the "title" parameter at /DesignTools/CssEditor.aspx. This update is recommended for all Paraview users. V17.1 was discovered to contain a path traversal vulnerability via the "f" parameter at /DesignTools/CssEditor.aspx. This update is recommended for all Paraview users.
In V17.2, the "f" parameter was changed to '/' at /DesignTools/CssEditor.aspx. By abusing the path traversal vulnerability, authenticated attackers can inject the code of their choice into the system. In addition, the update also fixed the XSS vulnerability via the "title" parameter at /DesignTools/CssEditor.aspx. This update is recommended for all Paraview users. V17.3 was discovered to contain a path traversal vulnerability via the "f" parameter at /DesignTools/CssEditor.aspx. This update is recommended for all Paraview users. V18.1 was discovered to contain a path traversal vulnerability via the "f" parameter at /DesignTools/CssEditor.aspx. This update is recommended for all Paraview users. V17.1
V17.2
In V17.2, the "f" parameter was changed to '/' at /DesignTools/CssEditor.aspx. By abusing the path traversal vulnerability, authenticated attackers can inject the code of their choice into the system. In addition, the update also fixed the XSS vulnerability via the "title" parameter at /DesignTools/CssEditor.aspx. This update is recommended for all Paraview users. V17.3 was discovered to contain a path traversal vulnerability via the "f" parameter at /DesignTools/CssEditor.aspx. This update is recommended for all Paraview users.
Vulnerability Summary
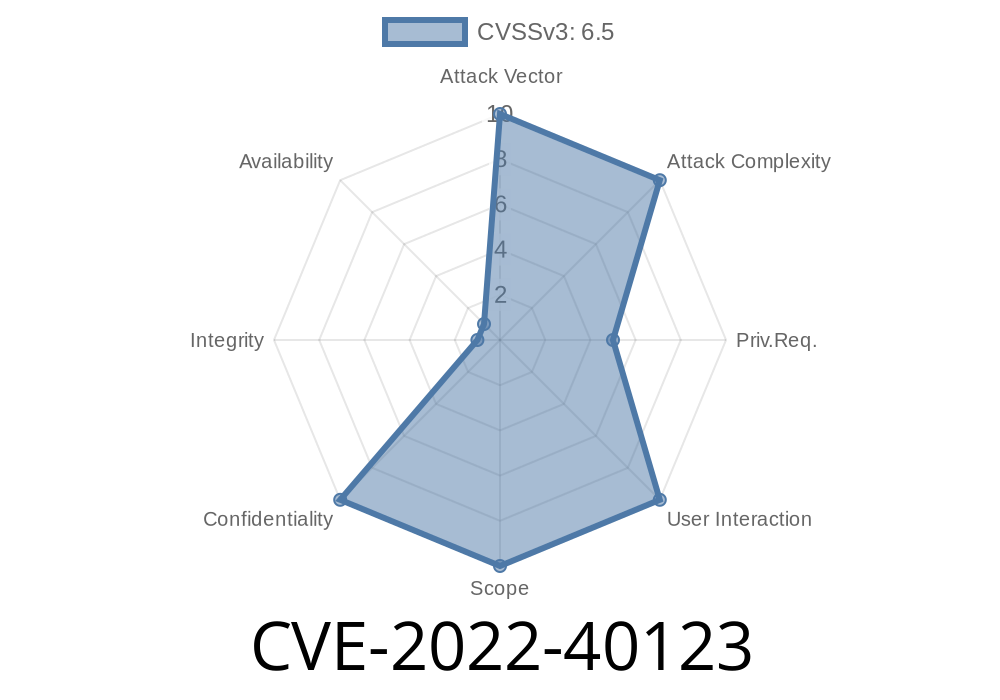
There are two path traversal vulnerabilities that exist in Paraview v17.1, 17.2 and 18.1. These vulnerabilities allow an authenticated attacker to inject the code of their choice into the system by abusing the file upload functionality of Paraview.
In V17.3, the "f" parameter was changed to '/' at /DesignTools/CssEditor.aspx. By abusing the path traversal vulnerability, authenticated attackers can inject the code of their choice into the system.
In V18, this issue was partially patched by changing the "f" parameter to '/' in CssEditor. By abusing the path traversal vulnerability, authenticated attackers can inject the code of their choice into the system
Timeline
Published on: 10/03/2022 13:15:00 UTC
Last modified on: 10/05/2022 13:01:00 UTC