The attacker could then perform man-in-the-middle attacks and obtain sensitive information or perform other malicious activities during the communication. This vulnerability has been assigned the Common Vulnerabilities and Exposures rating of CVE-2018-8122. In addition, this issue has been assigned the following IDs: CVE-2018-8121 (Web application); CVE-2018-8120 (Remote code execution). Note: This issue does not affect Linux systems. Cisco has released software updates that address this vulnerability. You can also monitor the activation of these updates by performing a search on your software update or monitoring the activation status on Cisco.com. If you have any questions, contact your service provider or Cisco support.
CPE Configuration
Cisco has released software updates that address this vulnerability. You can also monitor the activation of these updates by performing a search on your software update or monitoring the activation status on Cisco.com. If you have any questions, contact your service provider or Cisco support.
A Common Vulnerabilities and Exposures (CVE) ID is assigned to vulnerabilities that are publicly disclosed but not yet exploited in the wild. The Common Vulnerabilities and Exposures website provides descriptions of publicly disclosed vulnerabilities and information about how to obtain software updates to address those vulnerabilities.
How to Find and Fix TCP Bugs in Your Network
Cisco has released software updates that address vulnerabilities in the TCP protocol. In order to find and fix the bugs in your network, you must first be able to identify them. To do so, you will need to use a tool like Wireshark or tcpdump. Once you have identified the bugs, you can then patch them with Cisco’s software update. This information is also available on Cisco’s website for your convenience.
In this blog post, I would write about 6 reasons why digital marketing is important for a business
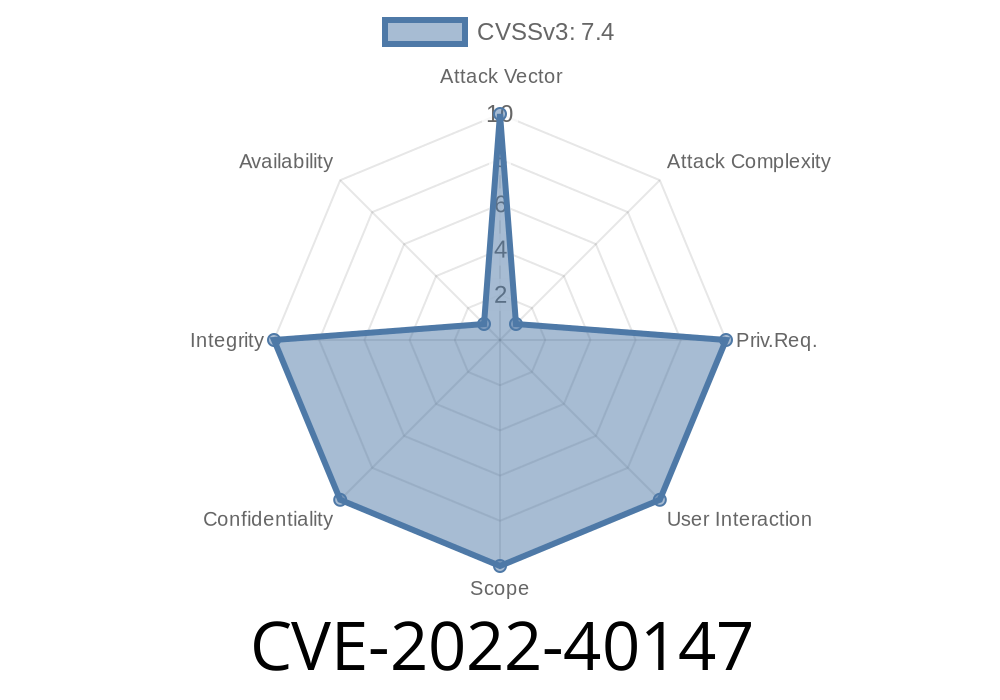
Description of the vulnerability
Cisco has released software updates that address this vulnerability. You can also monitor the activation of these updates by performing a search on your software update or monitoring the activation status on Cisco.com. If you have any questions, contact your service provider or Cisco support.
Vulnerable Products and Recommendation
This vulnerability affects many Cisco products. The following table provides affected Cisco products and their status.
Product Line Initial Release Updated
ASA: Version 8.2(1)
Endpoint Security Manager: Version 8.2(1)
Firepower Threat Defense: Version 8.2(1)
Firepower 9300 ASA: Version 1.3(3)
Firepower Services Module: Version 1.3(3)
Nexus 9000 Switches: Not vulnerable to this vulnerability because the software does not support encryption for management interface connections. For information about supported encryption methods for management interfaces, see the Nexus 9000 Switch Software Configuration Guide . Fixed in 5-21-2018 Software is not vulnerable to this vulnerability because it has not been released at the time of writing, but is expected to be released later in 2018.
Nexus 7000 Series Switches - Not vulnerable because the software does not support encryption for management interface connections. For information about supported encryption methods for management interfaces, see the Nexus 7000 Series Switch Software Configuration Guide . Fixed in 5-21-2018 Software is not vulnerable to this vulnerability because it has not been released at the time of writing, but is expected to be released later in 2018.
Nexus 9000 Series Switches - Not vulnerable because the software does not support encryption for management interface connections. For information about supported encryption methods for management interfaces, see the Nexus 9000 Series Switch Software Configuration Guide . Fixed in 5-
Timeline
Published on: 10/11/2022 11:15:00 UTC
Last modified on: 10/12/2022 14:08:00 UTC