There are two ways this can happen. The first is when input data is supplied that the parser doesn’t understand, such as an illegal character. The second way is when the parser is supplied with data that the parser already understands. For example, if the parser is given an XML document that contains a start tag with an ID attribute, then this already understood data will cause a stack overflow. The same applies if the parser is given an XML document that contains an end tag with an ID attribute. Therefore, it is important to always validate input data before parsing. Some best practices for validation include: - Validation of user input data - Validation of data inside data structures
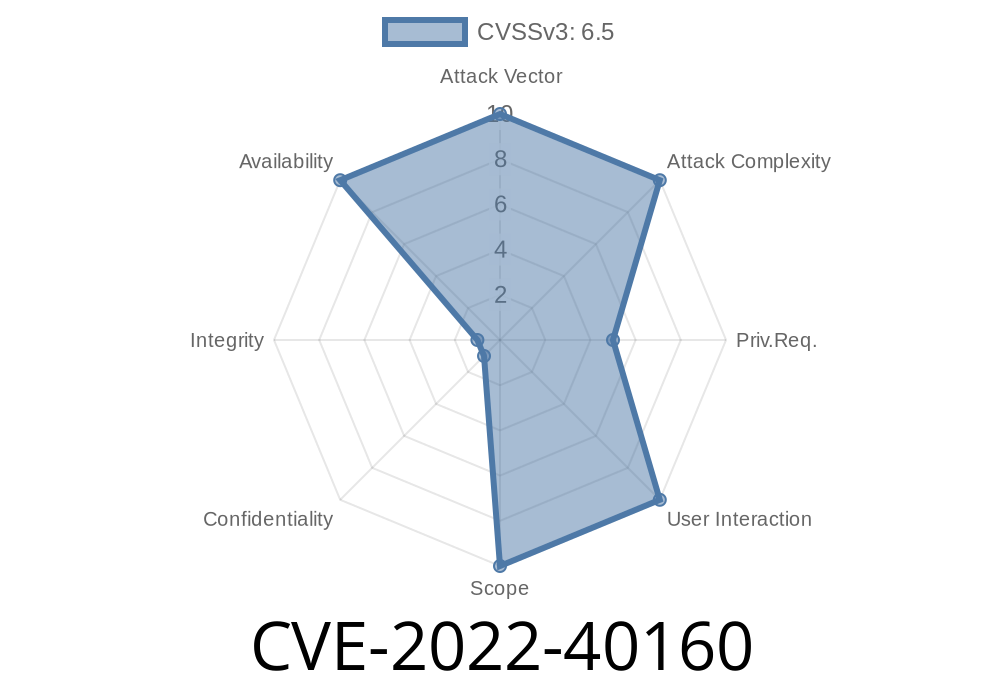
CVE-2022-40161
The second way that this can happen is when the parser is supplied with data that the parser already understands. For example, if the parser is given an XML document that contains a start tag with an ID attribute, then this already understood data will cause a stack overflow. The same applies if the parser is given an XML document that contains an end tag with an ID attribute. Therefore, it is important to always validate input data before parsing. Some best practices for validation include: - Validation of user input data - Validation of data inside data structures
Data Parsing
Data parsing is the process of converting an input data stream, such as a file or network packet, into a sequence of tokens. This conversion can be performed in any number of ways; these methods are known as lexical analysis and syntax analysis.
What you should do
The best way to avoid this type of vulnerability is to validate input before passing it to the parser. This can be accomplished by using regular expressions or XML Entity Definitions (EEDs). Some best practices for validation include: - Validation of user input data - Validation of data inside data structures
Why Outsourcing SEO Is Important
SQL Injection
: Misunderstood Attacks on Database Systems
SQL injection is a type of attack that occurs when a hacker sends malicious SQL queries to the server. The best defense against this threat is to allow only specific IPs from trusted sources to access your database. You can also use dynamic SQL which prevents the user from specifying an arbitrary string for their query. For example, you can create a function that returns "Hello" if the user inputs "world".
Timeline
Published on: 10/06/2022 18:16:00 UTC
Last modified on: 10/07/2022 18:57:00 UTC