CSRF occurs when an attacker tricks a user into performing unwanted actions on a site by tricking them via social engineering. For example, an attacker can send a victim a link via email that directs them to sign up for a site using their details. Since the site needs to be explicitly logged into for the attacker to be able to use it, the victim is forced to log into the site, giving the attacker access to the site. WordPress plugins can be vulnerable to this type of attack if they do not properly validate user input. With the right knowledge and tools, an attacker can easily exploit this vulnerability to perform actions on your site that they should not be able to do. IMPORTANT: Vulnerable WordPress plugins do not necessarily expose this vulnerability. This issue only affects the WordPress plugin where it is possible to set up a CSRF exploit. Last updated: January 15th, 2019
Many WordPress websites rely on third-party plugins to help make their lives easier. These plugins can be a valuable asset to your site, offering functionality that was either difficult to implement or too time-consuming to do so. However, due to the nature of these add-ons, they can also present a possible security risk to your site. One of the most common of these add-ons is the discussion forum plugin. These plugins are often installed in large numbers of WordPress websites. This makes them a critical component for any website
What is CSRF?
Cross-site request forgery (CSRF) is a type of security exploit whereby an attacker tricks a user into performing unwanted actions on a site by tricking them via social engineering.
For example, an attacker can send a victim a link via email that directs them to sign up for a site using their details. Since the site must be explicitly logged into for the attacker to be able to use it, the victim is forced to log in to the site, giving the attacker access to the site.
WordPress plugins can be vulnerable to this type of attack if they do not properly validate user input. With the right knowledge and tools, an attacker can easily exploit this vulnerability to perform actions on your site that they should not be able to do.
IMPORTANT: Vulnerable WordPress plugins do not necessarily expose this vulnerability. This issue only affects the WordPress plugin where it is possible to set up a CSRF exploit.
Overview and motivation behind the vulnerability
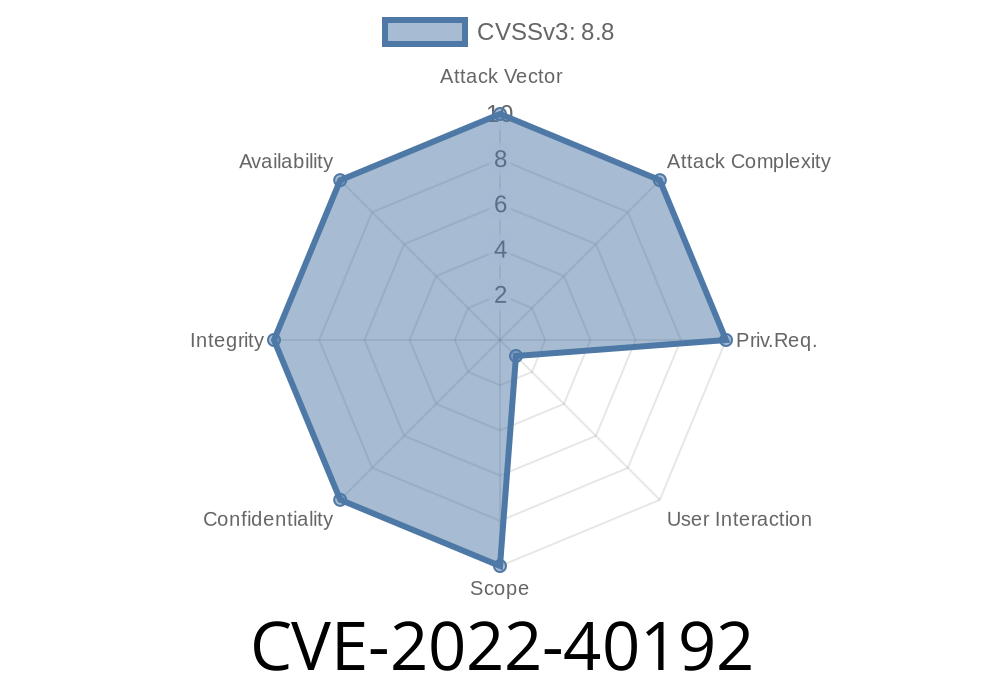
One of the most common vulnerabilities in WordPress plugins that can be exploited is the Cross-Site Request Forgery (CSRF). This vulnerability allows an attacker to perform actions on your site that they should not be able to do. In this case, CVE-2022-40192 allows an attacker to carry out any action on a website where a vulnerable discussion forum plugin has been installed. The specific vulnerability exposed within this plugin allows an attacker to set up a CSRF exploit without any user interaction.
The motivation behind this vulnerability comes from the ability of this particular vulnerability to bypass all security measures implemented by the plugin. By taking advantage of it, the attacker will be able to perform actions with administrator privileges. This means that any settings for which you have administrator privileges in WP will now be changed on your site. Using some of these settings will allow you to carry out different attacks such as stealing passwords or redirecting content on your website.
Exploit overview
A CSRF exploit occurs when an attacker tricks a user into performing unwanted actions on a website by tricking them via social engineering. For example, an attacker can send a victim a link via email that directs them to sign up for a site using their details. Since the site needs to be explicitly logged into for the attacker to be able to use it, the victim is forced to log into the site, giving the attacker access to the site. WordPress plugins can be vulnerable to this type of attack if they do not properly validate user input. With the right knowledge and tools, an attacker can easily exploit this vulnerability to perform actions on your site that they should not be able to do. IMPORTANT: Vulnerable WordPress plugins do not necessarily expose this vulnerability. This issue only affects the WordPress plugin where it is possible to set up a CSRF exploit. Last updated: January 15th, 2019
Timeline
Published on: 11/17/2022 23:15:00 UTC
Last modified on: 11/22/2022 00:40:00 UTC