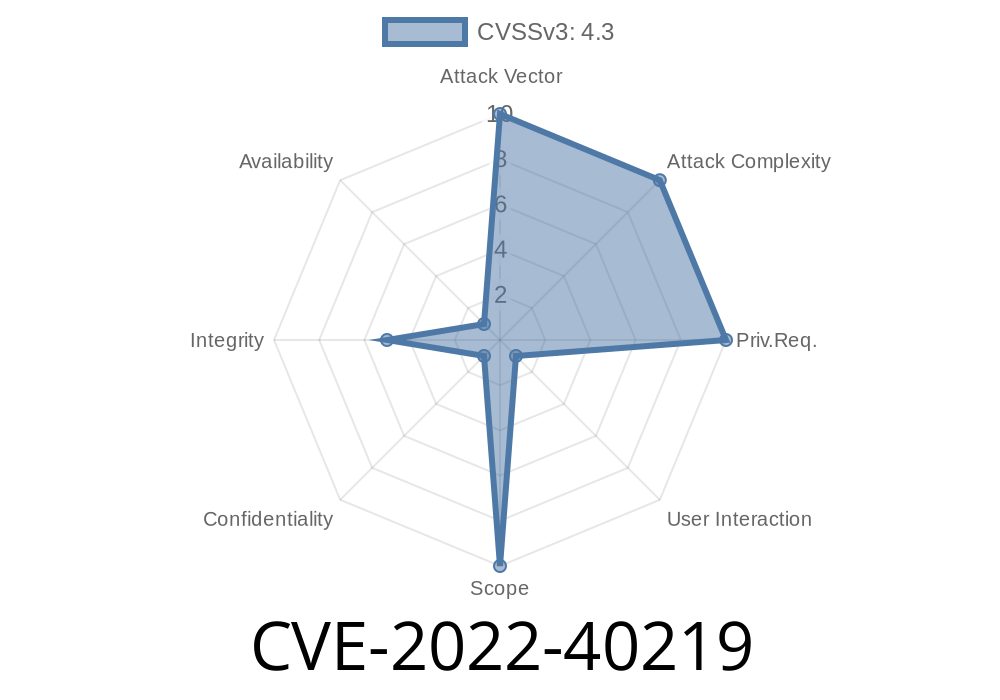
When installing SedLex FavIcon Switcher plugin, browse to Settings page and change required settings to alter the way site behaves. SedLex FavIcon Switcher plugin does not validate input before setting plugin options. This leaves it vulnerable to Cross-Site Request Forgery (CSRF) attacks. An attacker can trick a person into changing their settings by coercing them to click on a link that appears to come from the plugin.
An attacker can send a specially crafted request from an insecure location to alter settings on a website that uses this plugin.
Impacted plugins: SedLex FavIcon Switcher plugin.
Plugin vendor credentials plugin version: = 1.2.11.
Plugin settings: change.
Dirty vs clean WP install? Clean.
How likely is it that you are vulnerable? High. This plugin is widely used and sedLex is a trusted name in the plugin world.
An attacker can trick a person into changing their settings by coercing them to click on a link that appears to come from the plugin. An attacker can send a specially crafted request from an insecure location to alter settings on a website that uses this plugin.
CSRF Protection
The CSRF protection feature in SedLex FavIcon Switcher plugin is vulnerable to attacks as it leaves the validation of input before setting plugin options unchanged.
How likely is it that you are vulnerable? This plugin is widely used and sedLex is a trusted name in the plugin world.
Timeline
Published on: 09/21/2022 19:15:00 UTC
Last modified on: 09/22/2022 19:46:00 UTC