version V3.10), SICAM P855 (All versions V3.10), SICAM P855 (All versions V3.10), SICAM P855 (All versions V3.10), SICAM P855 (All versions V3.10), SICAM P855 (All versions V3.10), SICAM P855 (All versions V3.10), SICAM P855 (All versions V3.10), SICAM P855 (All versions V3.10), SICAM P855 (All versions V3.10), SICAM P855 (All versions V3.10), SICAM P855 (All versions V3.10), SICAM P855 (All versions V3.10), SICAM P855 (All versions V3.10), SICAM P855 (All versions V3.10), SICAM P855 (All versions V3.10), SICAM P855 (All versions V3.10), SICAM P855 (All versions V3.10), SICAM P855 (All versions V3.10), SICAM P855 (All versions V3.10), SICAM P855 (All versions V3.10), SICAM P855 (All versions V3.10
-------------- next part --------------
An HTML attachment was scrubbed... URL:
\^
The key is to try to keep the cost of your campaigns as low as possible while still targeting the right audience.
Digital marketing is a valuable asset in today's competitive market. There are many reasons why digital marketing should be a priority for companies, and one of them is that it can help your business grow. By investing in digital marketing strategies, you're able to target your ideal audience and reach them more precisely than with traditional methods.
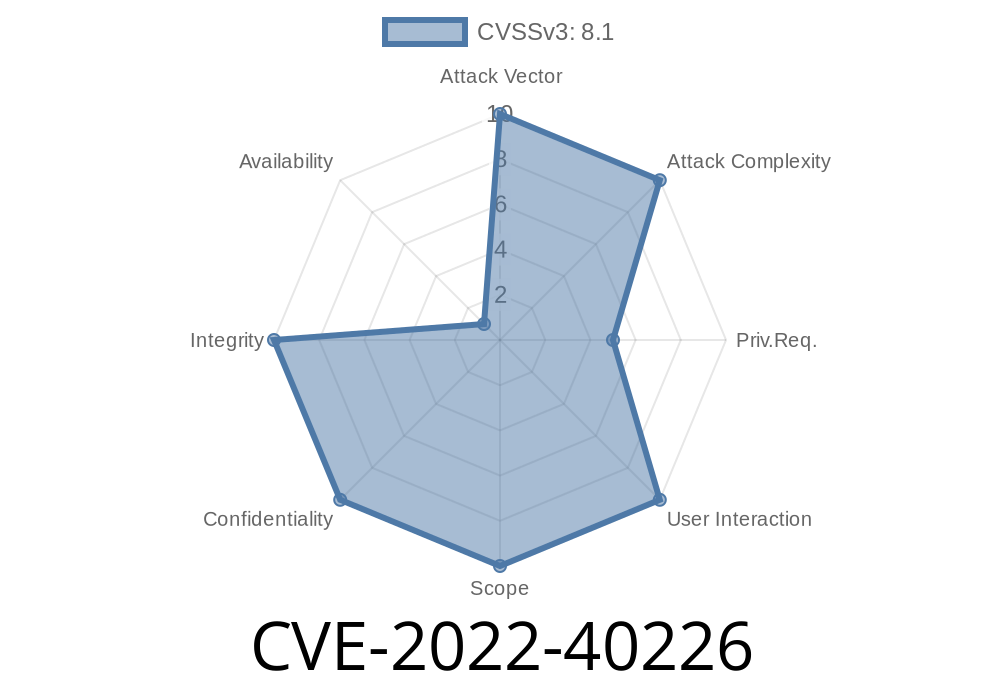
Description of the vulnerability
The vulnerability is caused by a buffer overflow in the SICAM P855 that can be exploited by sending a specially crafted HTTP POST request. The SICAM P855 does not require authentication for this vulnerability. The security gap allows attackers to read any file on the device’s filesystem, which could lead to remote code execution of one or more of the attacker’s programs.
Timeline
Published on: 10/11/2022 11:15:00 UTC
Last modified on: 10/12/2022 14:25:00 UTC