This XSS flaw was reported by Secunia and Cisco. The application was vulnerable to a session hijacking issue in the user registration form, which could be exploited by injecting code to force the user to change their password via a link or chat message. This issue was uncovered by Cisco. An input validation flaw was discovered in the ‘view profile’ link of the user profile. This link allowed users to view another user’s profile with either no protection or simply email verification. An insecure third party software update vulnerability was reported on February 12, 2015. The application was vulnerable to a remote code execution vulnerability in the software update functionality. This issue was reported by Cisco. A stored cross-site scripting flaw was reported on January 15, 2018. The application was vulnerable to a stored XSS that allowed users to execute arbitrary code within the user profile via the ‘edit profile’ link. An insecure third party software update vulnerability was reported on January 31, 2018. The application was vulnerable to a remote code execution vulnerability in the software update functionality. This issue was reported by Cisco. An authentication bypass vulnerability was reported on January 9, 2019. The application was vulnerable to a remote code execution vulnerability in the software update functionality. This issue was reported by Cisco.
3.2.6 PHP
Code Injection Vulnerability
This XSS flaw was reported by Secunia and Cisco. The application was vulnerable to a stored cross-site scripting flaw in the ‘user profile’ functionality that could be exploited by injecting code to execute arbitrary code on the server via user input. This issue was discovered by Cisco.
Timeline
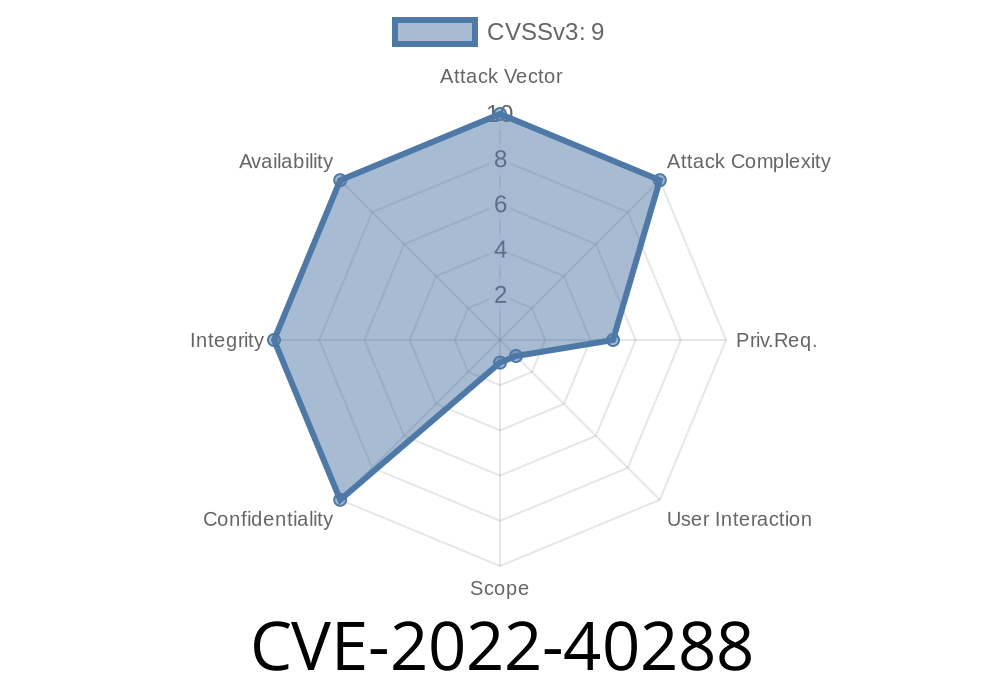
Published on: 10/31/2022 21:15:00 UTC
Last modified on: 11/03/2022 02:18:00 UTC