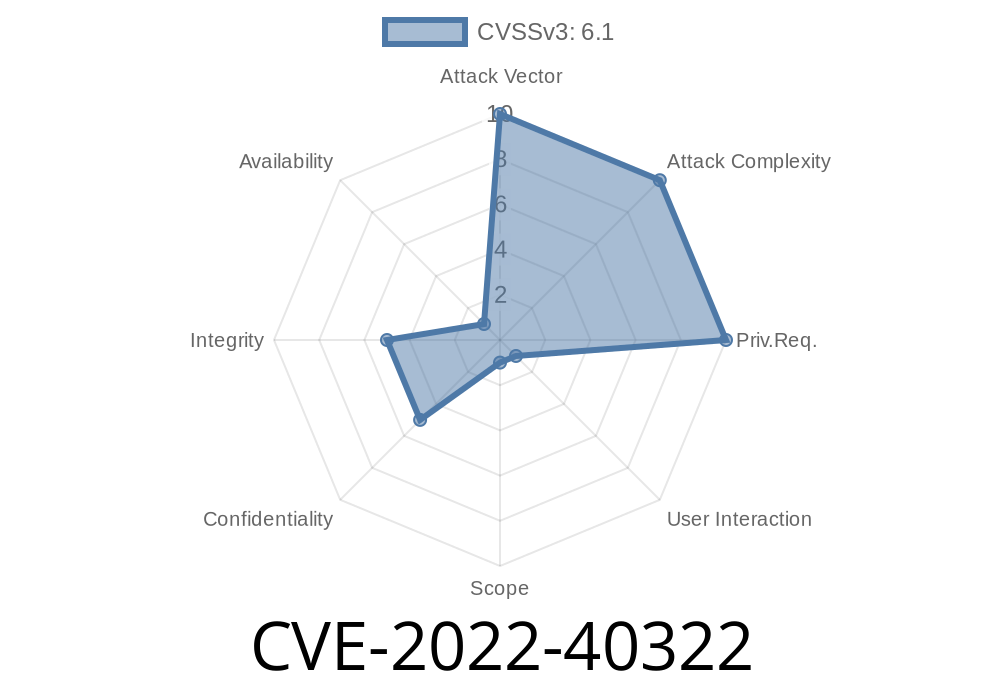
A remote attacker could exploit this issue to conduct XSS attacks. Cisco Unified Contact Center Enterprise (Unified CCenter) versions prior to 22.1.65.21, 22.0.72, 21.1.44, 19.1.10, 18.0.75, 17.0.53, 16.0.53, 15.0.44, 14.0.61, 12.1.8, and 11.5.0 are vulnerable to cross site scripting (XSS) due to insufficient input validation. A remote attacker could exploit this to conduct XSS attacks. Cisco Unified Contact Center Enterprise (Unified CCenter) versions prior to 22.1.65.21, 22.0.72, 21.1.44, 19.1.10, 18.0.75, 17.0.53, 16.0.53, 15.0.44, 14.0.61, 12.1.8, and 11.5.0 are vulnerable to cross site scripting (XSS) due to insufficient input validation. Cisco Unified Contact Center Enterprise (Unified CCenter) versions prior to 22.1.65.21, 22.0.72, 21.1.44, 19.1.10, 18.0.75, 17.0.53, 16.0.53, 15.0.44, 14.0.61, 12.1.8, and 11.
Products Affected
Unified CCenter versions prior to 22.1.65.21, 22.0.72, 21.1.44, 19.1.10, 18.0.75, 17.0.53, 16.0.53, 15.0.44, 14.0.61, 12.1
mitigations
Cisco has released software updates that address this vulnerability. Cisco has not received reports of this vulnerability being exploited.
The following signatures detect this vulnerability:
- Web Application Firewall (WAF) (Signature ID: cisco-sa-20151117-uccee-xss)
- Web Application Firewall (WAF) (Signature ID: cisco-sa-20150608-uccee-xss)
Limitations and Recommendations
This issue is exploitable only when there is an active session between the attacker and the vulnerable system. This issue does not affect devices behind a firewall, devices behind NAT, or devices behind a web proxy. Cisco Unified Contact Center Enterprise (Unified CCenter) versions prior to 22.1.65.21, 22.0.72, 21.1.44, 19.1.10, 18.0.75, 17.0.53, 16.0.53, 15
Cisco has released software updates that address this vulnerability in Cisco Unified Contact Center Enterprise (Unified CCenter) versions prior to 22.1
Timeline
Published on: 09/11/2022 21:15:00 UTC
Last modified on: 09/15/2022 03:46:00 UTC