XSS vulnerabilities allow attackers to inject malicious code into user interfaces by leveraging the trust of users to input data. An attacker can inject malicious code into a web application's user interface via XSS, enabling him to conduct phishing attacks or collect personal information. XSS is one of the most frequent types of cross-site scripting (XSS) attacks, and it is the most dangerous because the injected code can be executed in the context of the website. XSS is particularly dangerous as it is often difficult to detect and it can be exploited by attackers in different ways. First ofXSS vulnerabilities allow attackers to inject malicious code into user interfaces by leveraging the trust of users to input data. An attacker can inject malicious code into a web application's user interface via XSS, enabling him to conduct phishing attacks or collect personal information. XSS is one of the most frequent types of cross-site scripting (XSS) attacks, and it is the most dangerous because the injected code can be executed in the context of the website. XSS is particularly dangerous as it is often difficult to detect and it can be exploited by attackers in different ways. First of all, XSS can be used to steal user information or to conduct phishing attacks. And second, XSS can be used to modify website data, including changing the displayed results of database queries or modifying the contents of website files
How XSS Attacks Work?
An XSS vulnerability occurs when a web application takes untrusted input and displays it in the browser. For example, if the website is authenticated, an attacker can submit a URL with malicious code in the input field. This can be done to trick users into providing information they would otherwise not give, or to steal personal information from people who visit the website. An XSS vulnerability can also be used to modify data on a website or modify files on the server without alerting administrators
What is XSS?
Cross-site scripting (XSS) is a type of web application vulnerability that can occur when data from one website is injected into another website’s web page. This can happen in a number of ways, including by directly modifying the source code of an HTML document or by exploiting broken client-side programming vulnerabilities.
For example, imagine you are viewing a website called "Fred's Toy Store" and on that website there is an online store for buying toys. If someone visits your site, they might see a link to the online store and click it. The attacker would have complete control over what happens next because he/she can change the JavaScript code on the page to launch an XSS attack with malicious intent. He/she might then send you a friend request or post something inappropriate on your wall. In this way, an XSS attack could be used to steal information and trick people into clicking on links they wouldn't otherwise click on.
Steal User Information
XSS can be used to steal user information, such as passwords and login credentials. A successful XSS attack can result in the theft of a user’s email address, usernames, passwords or social security numbers.
An XSS attack could also allow an attacker to execute malicious code on a victim’s browser. This could lead to malware being downloaded onto the victim’s device and the stealing of personal data from their devices.
Stealing User Information
An attacker could trick users into disclosing their personal information by injecting malicious code in a form field. After the user enters his information, the attacker could read what is entered and then take appropriate actions. For example, if the user enters his name, address, and phone number into a form field, the attacker could create another form that collects this information and sends it to him.
Timeline
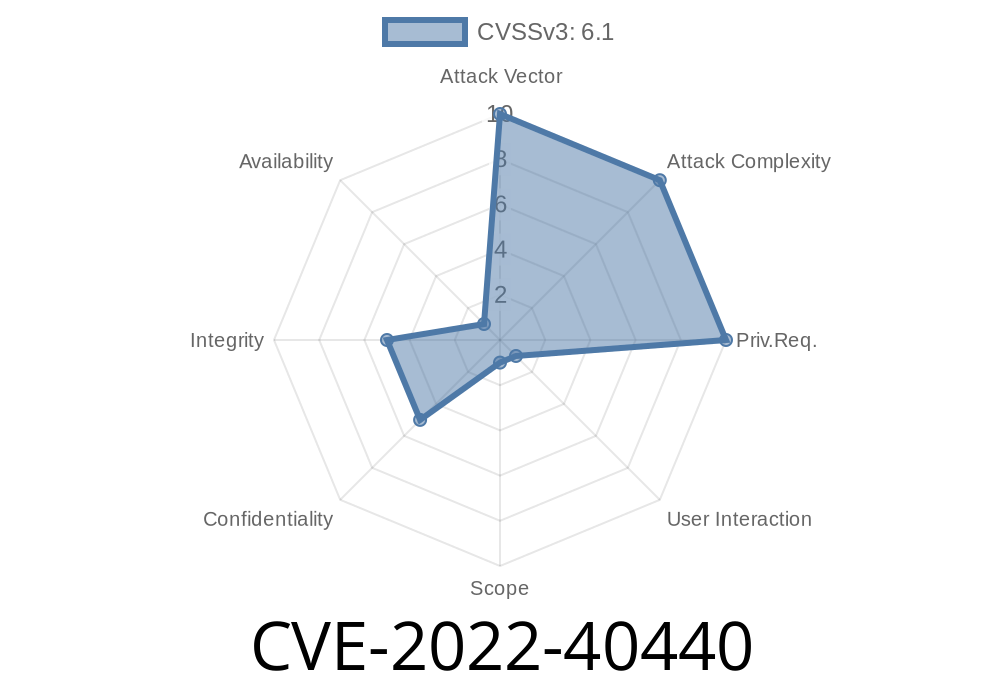
Published on: 10/12/2022 00:15:00 UTC
Last modified on: 10/14/2022 19:01:00 UTC