On October 31, 2017, the official Zend Security Advisory was published detailing the issue and the immediate action Zend advised users to take. According to the advisory, "An attacker can exploit this issue to execute arbitrary code in the context of the web server. The attacker must first inject malicious code into the server's configuration file in order to exploit this vulnerability, which is possible due to the file's full path disclosure." Fortunately, the advisory also provided a detailed explanation on how to fix the issue. Zend advised users to update to version 19, which had been patched.
What is Zend Server?
Zend Server is a "platform for building web applications, services and APIs." When the advisory was published, Zend advised users to update their current version of Zend Server to 19.
What is Zend Server?
Zend Server is a "platform for building web applications, services and APIs." When the advisory was published, Zend advised users to update their current version of Zend Server to 19.
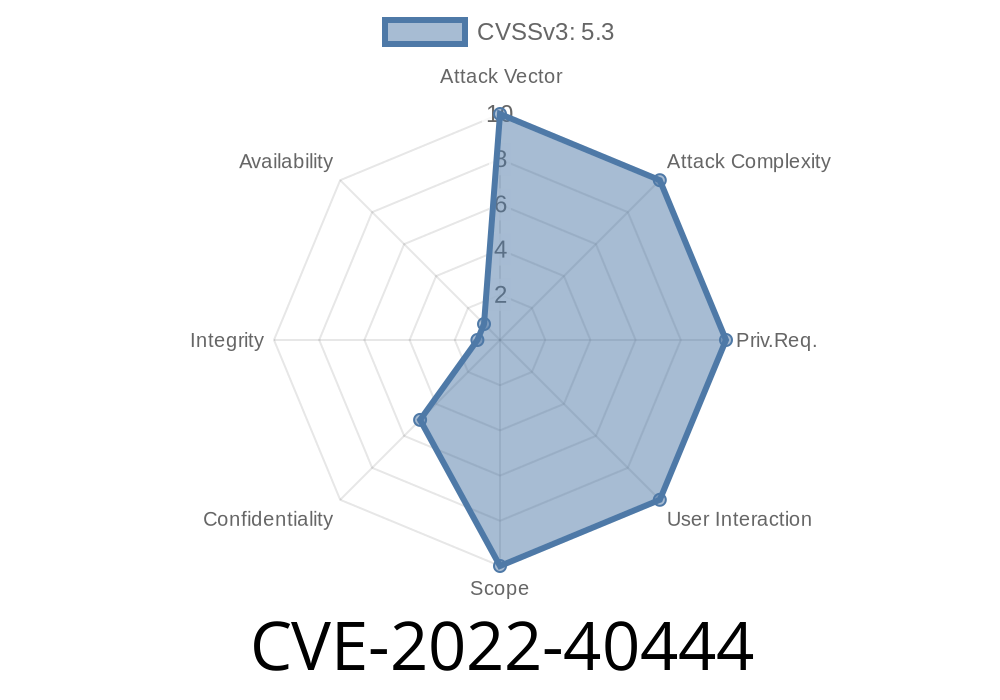
Zend Security Advisory on CVE-2022-40444
Zend Security Advisory: A vulnerability was found in the Zend Server, which could have allowed attackers to execute arbitrary code in the context of the web server. The advisory also details how to fix this issue.
Information on how to fix the issue is provided on Zend's website in order to protect your business's website and other services from further attack.
Happy Halloween everyone.
How to check if your version is patched?
To ensure that your version was patched, you should visit the version 19 release notes. If the issue has been addressed, you will see a note about the patch in this section.
If the issue hasn't been mentioned, then you need to update to the latest version of Zend Server. It is important to know that in order to fix this vulnerability, users had to install a patch due to full path disclosure.
The security advisory provided clear instructions on how to fix the vulnerability, so there wasn't much confusion around this issue.
Timeline
Published on: 09/22/2022 14:15:00 UTC
Last modified on: 09/23/2022 18:48:00 UTC