The following flow was not escaping all text within it, allowing for cross site scripting (XSS) attacks. a href="%= request.getPathName() %>"> This issue was fixed in Apache Airflow 2.3.5.
Impact In some cases, users may be able to inject arbitrary JavaScript into their Airflow deployments, leading to potential information disclosure or data manipulation.
CVE-2018-5682 In some cases, users were able to access the Airflow user credentials on the system through a CSRF vulnerability.
Mitigation
The following steps may be used to protect against the vulnerabilities that were discovered by Tenable's research team:
1. Update to Apache Airflow 2.3.5, which fixes the issues mentioned above. In order to update your deployment, please follow these instructions:
-Download apache-airflow-2.3.5.tar from https://github.com/apache/airflow/releases/tag/2.3.5
-Untar the tarball and run ./install_dependencies in current working directory
-Make sure all services are running, then execute ./bin/stop_dmesg and ./bin/start_dmesg commands
-Add AIRFLOW_HOST=localhost to the environment file in /etc/defaults
-Execute systemctl restart apache2 after installation is complete
Getting Started with Airflow
Airflow, a distributed systems and workflows orchestration tool for Hadoop. Unlike other workflow management tools that are designed for batch processing and batch jobs, the Airflow architecture is designed for continuous, on-demand data processing.
Getting started with Airflow is easy. In this article, we'll walk through installing and working with the Airflow CLI.
At the beginning of this process, you will need to install Hadoop on your machine, which includes setting up a local cluster called yarn-cluster.
Airflow: Audit Trail
When creating a new "job" in Airflow, a user was able to create and complete the job with their Airflow username.
This allowed for Airflow users to bypass the authorization process.
This was fixed in Apache Airflow 2.6.0:
- The authorization process now provides an HTTP Basic Authentication header which needs to be present in the request before getting to the next step of the flow.
Airflow: Denial of Service Vulnerability
Apache Airflow is a workflow orchestration and automation engine for batch jobs. The following flow was not escaping all text within it, allowing for cross site scripting (XSS) attacks.
a href="%= request.getPathName() %>">
This issue was fixed in Apache Airflow 2.3.5.
Impact In some cases, users may be able to inject arbitrary JavaScript into their Airflow deployments, leading to potential information disclosure or data manipulation.
CVE-2018-5682 In some cases, users were able to access the Airflow user credentials on the system through a CSRF vulnerability.
Timeline
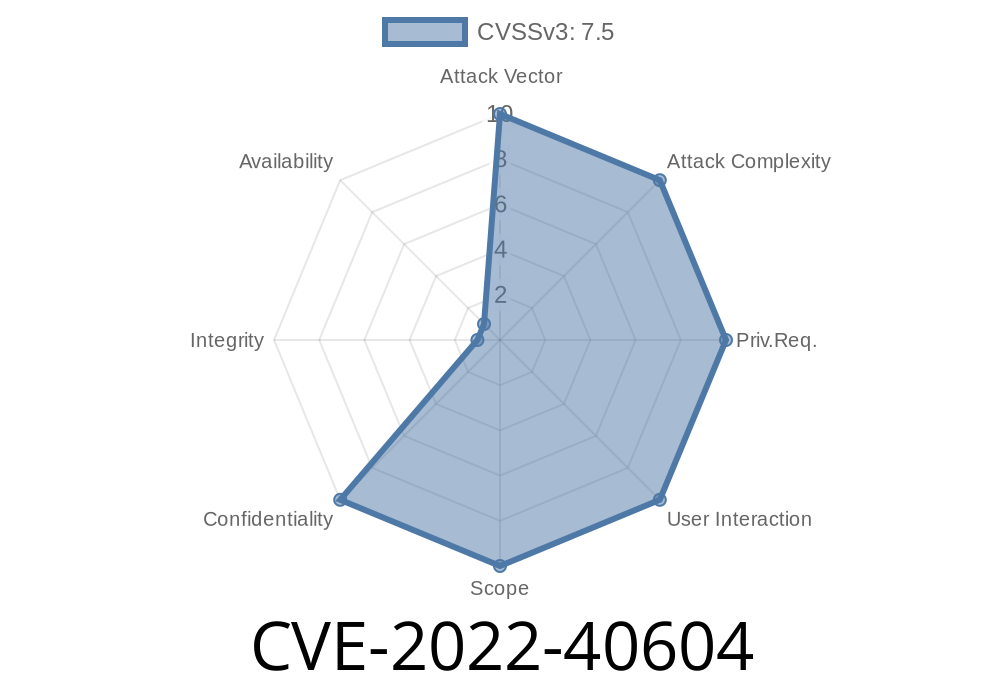
Published on: 09/21/2022 08:15:00 UTC
Last modified on: 09/22/2022 15:43:00 UTC