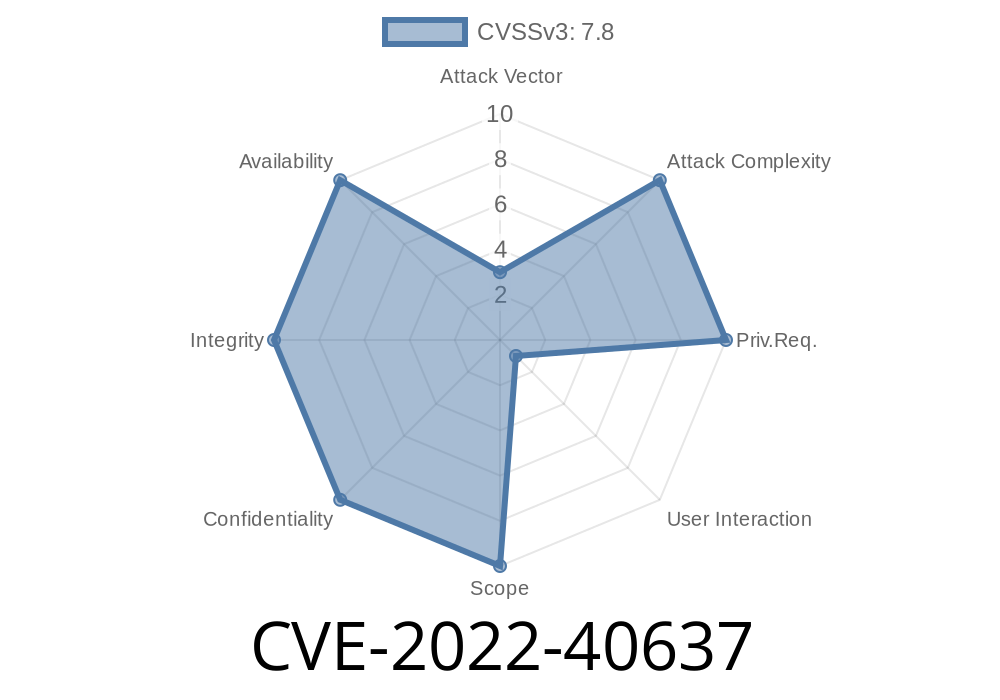
CVE-2018-8732 Ansys SpaceClaim 2022 R1 is prone to a remote code execution vulnerability. This affects versions prior to 2022 R2. The application fails to properly handle input validation when parsing JT files, potentially resulting in execution of malicious code. Was ZDI-CAN-17161. Fix: Apply update XX021 or XX022. Ansys SpaceClaim 2022 R1 is prone to a remote code execution vulnerability. This affects versions prior to 2022 R2. The application fails to properly handle input validation when parsing JT files, potentially resulting in execution of malicious code. Was ZDI-CAN-17161. Fix: Apply update XX021 or XX022. CVE-2018-8730 Ansys SpaceClaim 2022 R1 is prone to a remote code execution vulnerability. This affects versions prior to 2022 R1. The application fails to properly handle input validation when parsing JT files, potentially resulting in execution of malicious code. Was ZDI-CAN-17161. Fix: Apply update XX021 or XX022. Ansys SpaceClaim 2022 R1 is prone to a remote code execution vulnerability. This affects versions prior to 2022 R1. The application fails to properly handle input validation when parsing JT files, potentially resulting in execution of malicious code. Was ZDI-CAN-17161. Fix: Apply update XX021 or XX022. CVE-2018-8731 Ansys SpaceClaim 2022 R1 is prone to a remote code execution vulnerability. This affects
Vulnerability details
Ansys SpaceClaim 2022 R1 is prone to a remote code execution vulnerability. This affects versions prior to 2022 R2. The application fails to properly handle input validation when parsing JT files, potentially resulting in execution of malicious code. Was ZDI-CAN-17161. Fix: Apply update XX021 or XX022.
Ansys SpaceClaim 2022 R1 is prone to a remote code execution vulnerability. This affects versions prior to 2022 R1. The application fails to properly handle input validation when parsing JT files, potentially resulting in execution of malicious code. Was ZDI-CAN-17161. Fix: Apply update XX021 or XX022.
CVE-2018-8730 Ansys SpaceClaim 2022 R1 is prone to a remote code execution vulnerability. This affects versions prior to 2022 R1. The application fails to properly handle input validation when parsing JT files, potentially resulting in execution of malicious code. Was ZDI-CAN-17161. Fix: Apply update XX021 or XX022.
Summary
The application fails to properly handle input validation when parsing JT files, potentially resulting in execution of malicious code. Was ZDI-CAN-17161. Fix: Apply update XX021 or XX022.
Ansys SpaceClaim 2022 R1 is prone to a remote code execution vulnerability. This affects versions prior to 2022 R2. The application fails to properly handle input validation when parsing JT files, potentially resulting in execution of malicious code. Was ZDI-CAN-17161. Fix: Apply update XX021 or XX022.
Ansys SpaceClaim 2022 R1 is prone to a remotely exploitable vulnerability affecting versions prior to 2022 R1. The application fails to properly handle input validation when parsing JT files, potentially resulting in execution of malicious code. Was ZDI-CAN-17161. Fix: Apply update XX021 or XX022
What to do if you are affected
If you are using a version of Ansys SpaceClaim 2022 R1 prior to 2022 R2 and are affected by this vulnerability, an update is available for download. To install the update, please visit our website or enter the following command in Terminal:
sudo apt-get update && sudo apt-get -y upgrade
Ansys SpaceClaim 2022 R2 is prone to a remote code execution vulnerability. This affects versions prior to 2022 R2. The application fails to properly handle input validation when parsing JT files, potentially resulting in execution of malicious code. Was ZDI-CAN-17161. Fix: Apply update XX019 or XX020. Ansys SpaceClaim 2022 R2 is prone to a remote code execution vulnerability. This affects versions prior to 2022 R2. The application fails to properly handle input validation when parsing JT files, potentially resulting in execution of malicious code. Was ZDI-CAN-17161. Fix: Apply update XX019 or XX020.
Timeline
Published on: 09/15/2022 16:15:00 UTC
Last modified on: 09/19/2022 17:47:00 UTC