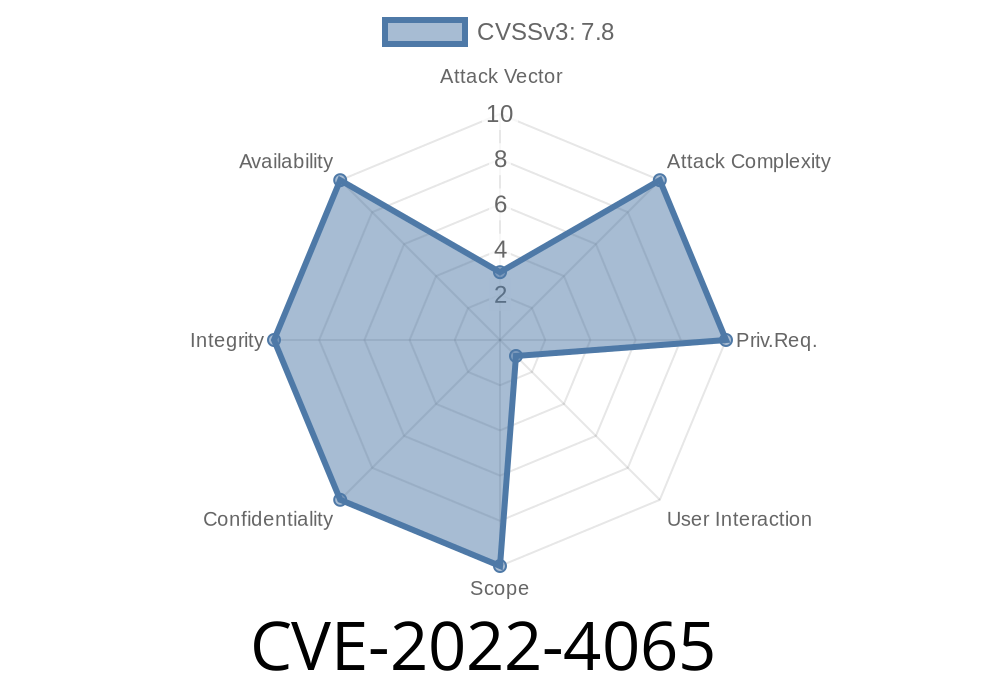
A vulnerability was found in cbeust testng. It has been declared as critical. Affected by this vulnerability is the function testngXmlExistsInJar of the file testng-core/src/main/java/org/testng/JarFileUtils.java of the component XML File Parser. The manipulation leads to path traversal. The attack can be launched remotely. The name of the patch is 9150736cd2c123a6a3b60e6193630859f9f0422b. It is recommended to apply a patch to fix this issue. The associated identifier of this vulnerability is VDB-214027. A vulnerability was found in cbeust testng. It has been declared as critical. Affected by this vulnerability is the function testngXmlExistsInJar of the file testng-core/src/main/java/org/testng/JarFileUtils.java of the component XML File Parser. The manipulation leads to path traversal. The attack can be launched remotely. The name of the patch is 9150736cd2c123a6a3b60e6193630859f9f0422b. It is recommended to apply a patch to fix this issue. The associated identifier of this vulnerability is VDB-214027. A vulnerability was found in cbeust testng. It has been declared as critical. Affected
Overview of the Vulnerability
The vulnerability is in testngXmlExistsInJar of the file testng-core/src/main/java/org/testng/JarFileUtils.java of the component XML File Parser.
Vulnerability Scenario
The manipulation leads to path traversal. The attack can be launched remotely.
Vulnerability Description:
A vulnerability was found in cbeust testng. It has been declared as critical. Affected by this vulnerability is the function testngXmlExistsInJar of the file testng-core/src/main/java/org/testng/JarFileUtils.java of the component XML File Parser. The manipulation leads to path traversal. The attack can be launched remotely.
Proof of Concept URL:
http://localhost//xmlparserservice?test=1&path=/testng-core%2Fsrc%2Fmain%2Fjava%2Forg%2Ftestng%2FJarFileUtils.java%20(CVE-2022-4065)
Keywords:
cbeust, remote, path, xml file parser
Vulnerability Description
This vulnerability has been found in the function testngXmlExistsInJar of the file testng-core/src/main/java/org/testng/JarFileUtils.java of the component XML File Parser. The manipulation leads to path traversal. The attack can be launched remotely.
The name of the patch is 9150736cd2c123a6a3b60e6193630859f9f0422b. It is recommended to apply a patch to fix this issue. The associated identifier of this vulnerability is VDB-214027
Timeline
Published on: 11/19/2022 19:15:00 UTC
Last modified on: 11/26/2022 03:24:00 UTC