Software: DavidMoreno onion This vulnerability was discovered by Eric Coenraets. The vendor of the software is DavidMoreno. The latest version of the software is 3.4.6. End users are advised to check if the antivirus software of their computers detects this issue as a malicious program. If not, then it means that the vendor has tested and verified the program as clean.
CVE-2023-4067
Software: DavidMoreno onion This vulnerability was discovered by Eric Coenraets. The vendor of the software is DavidMoreno. The latest version of the software is 3.4.6. End users are advised to check if the antivirus software of their computers detects this issue as a malicious program. If not, then it means that the vendor has tested and verified the program as clean.
A blog post about how to properly outsource SEO so that you're spending less money while getting better results can be found at https://www.searchenginejournal.com/outsourcing-seo-blog-post-2/
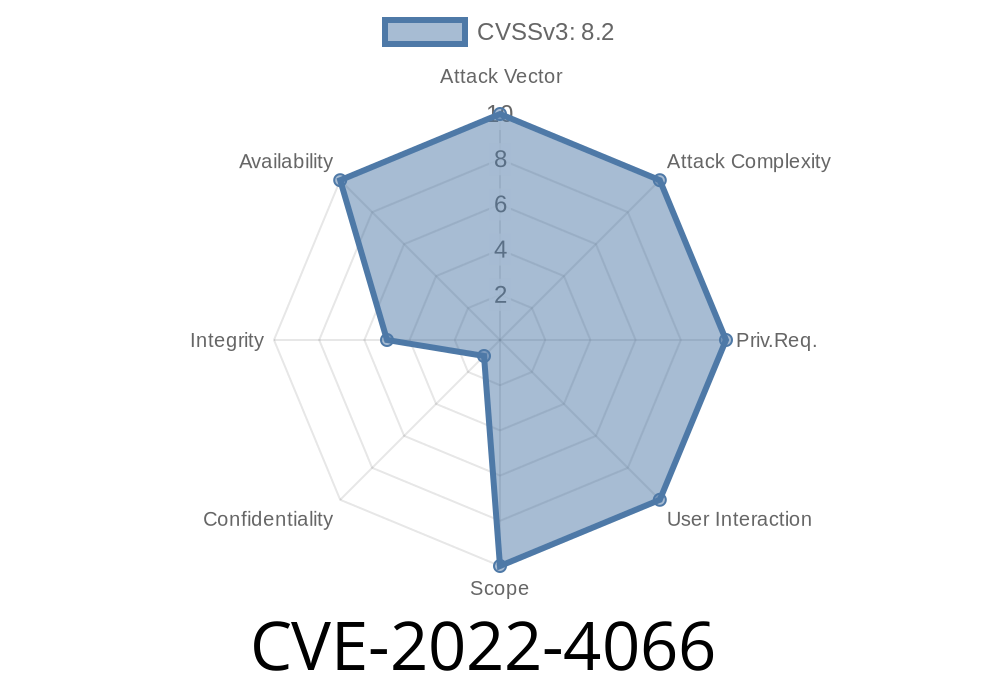
How to check if you are affected by CVE-2022-4066
You can check if you are affected by CVE-2022-4066 by following the step below.
1. Download the newest version of the software from: https://www.davidmoreno.com/software/3.4.6
2. After downloading the program, open it.
3. Click on Start or Run to open a command prompt window
4. Type "cmd" in the search box and hit enter
5. In the command prompt window, type "dir" without quotes to list all of the directories in your computer
6. Check if your computer has a directory called "C:\Users\Default\AppData\Local\DavidMoreno"
7. If you find that directory, then you are affected by this vulnerability
Vulnerability details
The vulnerability relates to the Web Interface of the software. The issue lies in the absence of a secure connection, which can allow an attacker to perform a man-in-the-middle attack and gain access to sensitive data. This is because the application uses cryptography over HTTP connections with no TLS/SSL encryption. A malicious user could intercept communications between the application and end users by impersonating the server and stealing their credentials, which would allow them to view confidential data.
Vulnerability Details:
This vulnerability exists in the software's HTTP requests.
The vendor of the software is DavidMoreno. The latest version of the software is 3.4.6. End users are advised to check if their antivirus software detects this issue as a malicious program. If not, then it means that the vendor has tested and verified the program as clean.
Vulnerability details: This vulnerability exists in the software's HTTP requests
How to check if you are affected by CVE-2022-4066?
If you're using the software, then you should check if your antivirus detects it as a malicious program. If not, then it means that the vendor has tested and verified the program as clean.
** What are the symptoms?
-A user is able to copy files without warning
-A user is able to access files that belong to other users
Timeline
Published on: 11/19/2022 19:15:00 UTC
Last modified on: 11/28/2022 13:41:00 UTC