An attacker can leverage known vectors such as insecure content in social media sites or email messages, or lurking remote attackers to conduct a click-through attack. In certain cases, attackers can also exploit network behavior to host malicious TIF images. Mitigating factors include frequent software updates and the implementation of basic security precautions such as avoiding opening unknown or suspicious content.
Signing up for security alerts to be notified when new information becomes available.
Check for new software updates on a regular basis
One way to protect yourself from click-through attacks is to install the latest software updates for your operating system and browser. Frequent software updates can help you mitigate any vulnerabilities that may have been identified in the past. Software updates are often released in response to newly discovered vulnerabilities or when significant changes have been made to a product’s functionality. When software updates are available, they will typically be listed on the company website, or it will be announced on social media platforms such as Twitter or Facebook.
Signing up for security alerts through third-party websites like Google alerts is an effective way to stay up-to-date on new information related to malicious TIF images. In addition, make sure you never open attachments with names that make them suspicious, such as "test" or "image." While these tips won't always prevent a click-through attack from happening, they can help reduce your chances of falling prey.
Summary
An attacker can leverage known vectors such as insecure content in social media sites or email messages, or lurking remote attackers to conduct a click-through attack. In certain cases, attackers can also exploit network behavior to host malicious TIF images. Mitigating factors include frequent software updates and the implementation of basic security precautions such as avoiding opening unknown or suspicious content.
Signing up for security alerts to be notified when new information becomes available.
User education and awareness
The most common point of entry into browsing malicious TIFs is via social media or email. To avoid falling victim to these attacks, a user should be educated about click-through attacks, be aware of what types of content has the potential to be compromised and how those vulnerabilities can be mitigated. In addition, a user should subscribe for security alerts that would notify them when new information is available; this will help prevent an attack from occurring.
Vulnerability overview
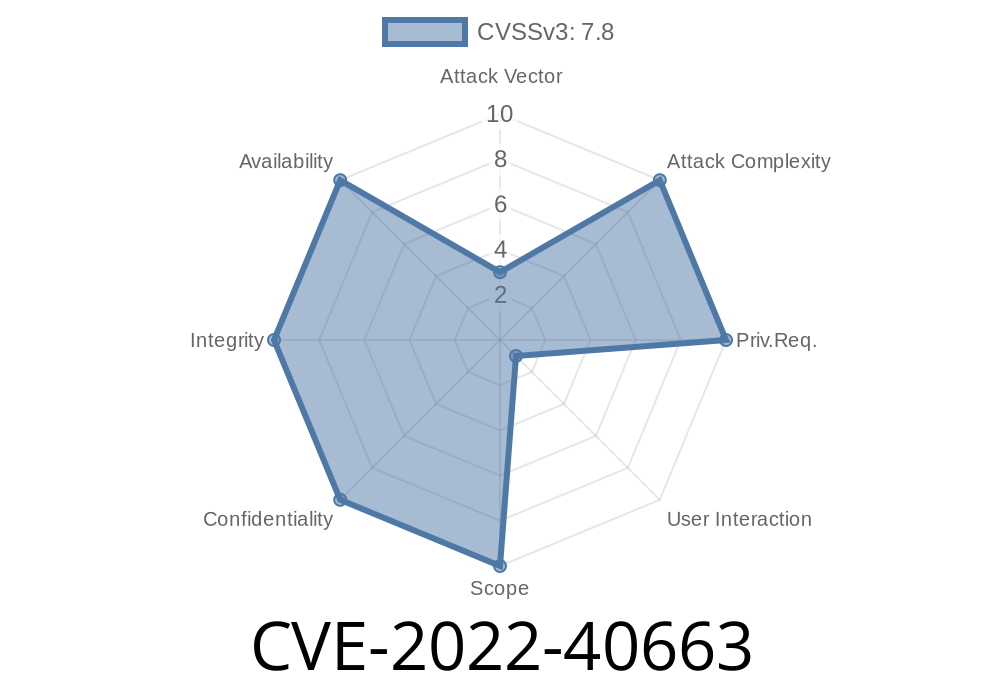
On if CVE-2022-40663
CVE-2022-40663 is a vulnerability that impacts the following products: Microsoft Office 2016, Microsoft Office 2013, Microsoft SharePoint Server 2016, Microsoft SharePoint Server 2013, Microsoft Exchange Server 2013 and Microsoft Exchange Server 2010.
A malicious TIF image can be created in order to exploit this vulnerability.
Mitigating factors include frequent software updates and the implementation of basic security precautions such as avoiding opening unknown or suspicious content.
Timeline
Published on: 09/15/2022 16:15:00 UTC
Last modified on: 09/17/2022 03:29:00 UTC