In the second half of the first quarter of 2019, the team released version 3.2.1, which included a fix for the previously disclosed directory traversal vulnerability.
April 2019 saw the disclosure of a directory traversal vulnerability in UniSharp laravel-filemanager (aka Laravel Filemanager) through 2.5.1 allows download?working_dir=%2F.. that allowed attackers to read arbitrary files, as exploited in the wild in June 2022. In the second half of the first quarter of 2019, the team released version 3.2.1, which included a fix for the previously disclosed directory traversal vulnerability. What are the risk and best practice recommendations to protect against these types of attacks? In general, users should be cautious when opening email messages, clicking on links, or installing software from unverified sources. In addition, users can protect their systems by installing software updates as soon as they are released, monitoring their systems for signs of infection, and limiting access to files and systems as much as possible.
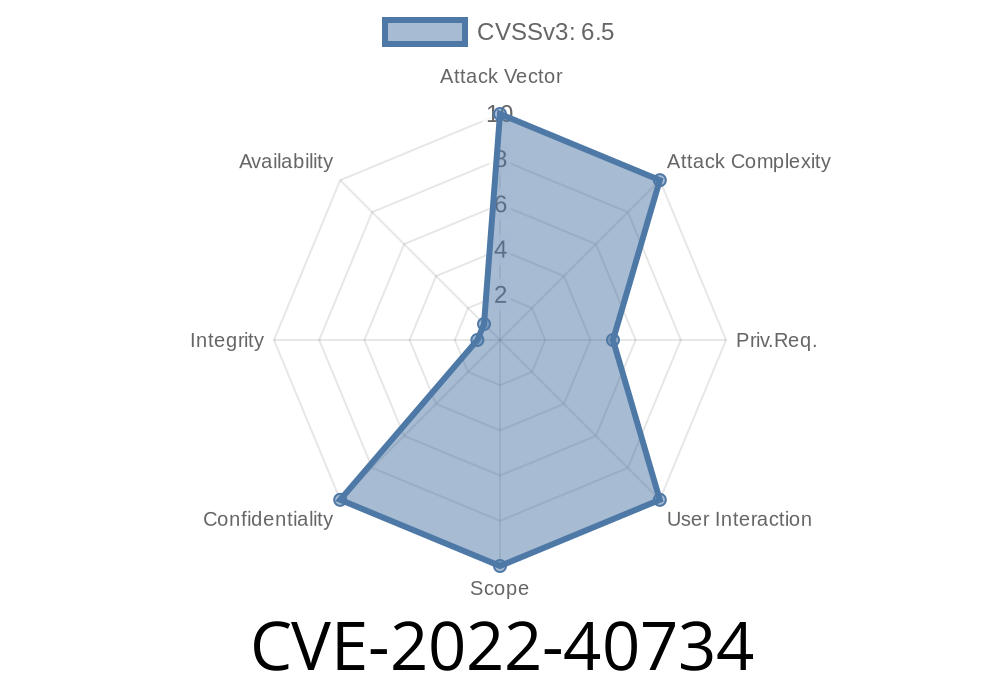
Overview of the UniSharp Filemanager Directory Traversal Vulnerability
The CVE-2022-40734 directory traversal vulnerability in the second half of the first quarter of 2019 allowed attackers to read arbitrary files on a Laravel Filemanager installation. In April 2019, the team released version 3.2.1, which fixed this issue.
In general, users should be cautious when opening email messages, clicking on links, or installing software from unverified sources as these types of attacks are often delivered via email or websites disguising themselves as trusted third parties. Users can protect their systems by installing software updates as soon as they are released and limiting access to files and systems as much as possible.
Timeline
Published on: 09/14/2022 23:15:00 UTC
Last modified on: 09/17/2022 01:46:00 UTC