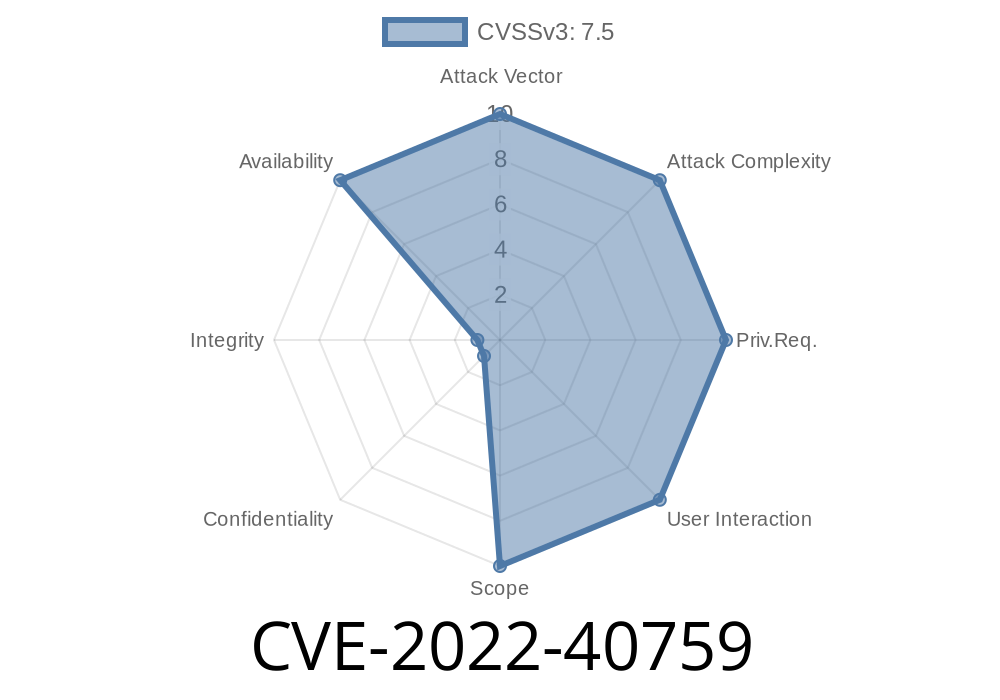
This can lead to a situation where the trusted application continues to execute code on the Samsung mTower and has no recourse. An attacker can exploit this vulnerability to create a situation where the trusted application will continue to execute code on the Samsung mTower and have no recourse. This can lead to a situation where the trusted application will continue to execute code on the Samsung mTower and have no recourse. An attacker can exploit this vulnerability to create a situation where the trusted application will continue to execute code on the Samsung mTower and have no recourse. This can lead to a situation where the trusted application will continue to execute code on the Samsung mTower and have no recourse. An attacker can exploit this vulnerability to create a situation where the trusted application will continue to execute code on the Samsung mTower and have no recourse. This can lead to a situation where the trusted application will continue to execute code on the Samsung mTower and have no recourse. An attacker can exploit this vulnerability to create a situation where the trusted application will continue to execute code on the Samsung mTower and have no recourse. An attacker can exploit this vulnerability to create a situation where the trusted application will continue to execute code on the Samsung mTower and have no recourse
Vulnerability details
A flaw in the way Samsung mTower handles untrusted applications could lead to a situation where the trusted application will continue to execute code on the Samsung mTower and have no recourse. An attacker can exploit this vulnerability to create a situation where the trusted application will continue to execute code on the Samsung mTower and have no recourse. This can lead to a situation where the trusted application will continue to execute code on the Samsung mTower and have no recourse. An attacker can exploit this vulnerability to create a situation where the trusted application will continue to execute code on the Samsung mTower and have no recourse. This can lead to a situation where the trusted application will continue to execute code on the Samsung mTower and have no recourse. An attacker can exploit this vulnerability to create a situation where the trusted application will continue to execute code on the Samsung mTower and have no recourse. This can lead to a situation where the trusted application will continue to execute code on the Samsung mTower and have no recourse. An attacker can exploit this vulnerability to create a situation where the trusted application will continue to execute code on the Samsung mTower and have no recourse
Overview of the Vulnerability
An attacker can exploit this vulnerability to create a situation where the trusted application will continue to execute code on the Samsung mTower and have no recourse. This can lead to a situation where the trusted application will continue to execute code on the Samsung mTower and have no recourse. An attacker can exploit this vulnerability to create a situation where the trusted application will continue to execute code on the Samsung mTower and have no recourse. This can lead to a situation where the trusted application will continue to execute code on the Samsung mTower and have no recourse. An attacker can exploit this vulnerability to create a situation where the trusted application will continue to execute code on the Samsung mTower and have no recourse. This can lead to a situation where the trusted application will continue to execute code on the Samsung mTower and have no recourse. An attacker can exploit this vulnerability to create a situation where the trusted application will continue to execute code on the Samsung mTower and have no recourse.
Vulnerability Information Disclosure
A vulnerability exists in the code that allows a malicious application to access some of the private data and information stored on a Samsung mTower. This vulnerability can allow an attacker to access sensitive data.
There are no known workarounds for this vulnerability.
Timeline
Published on: 09/16/2022 22:15:00 UTC
Last modified on: 09/21/2022 19:49:00 UTC