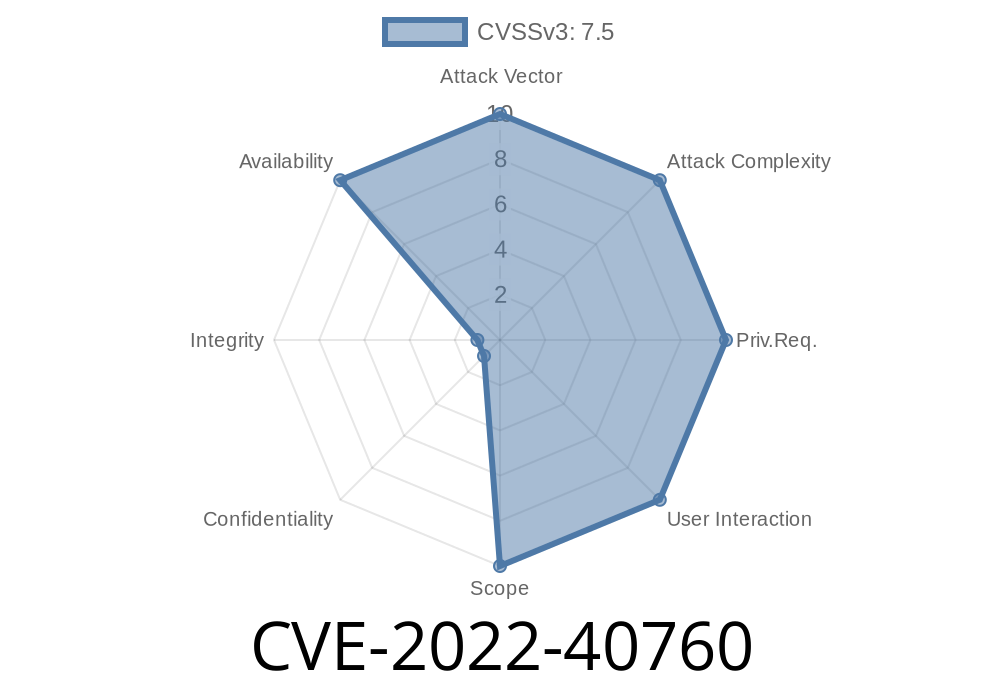
The chunkSize parameter defines the size of the data block which is sent to the TEE. When the value of this parameter is set excessively high, the data block will be sent to the TEE which will lead to a DoS. A remote attacker can exploit this vulnerability to trigger a DoS against the TEE by sending malicious data block with a chunkSize value of -1.
When the length value of the data block is not checked, a remote attacker can send a malicious data block with an excessive length value of chunkSize to the TEE_MACUpdate function of the mTower application with the mTower application as a trusted application.
An attacker can leverage this type of vulnerability to cause DoS to the TEE by sending large amounts of data with excessive length values to the TEE_MACUpdate function, resulting in the application not being able to receive the data block, causing the application to crash.
Buffer Overflow in the TEE_MACUpdate function through 0.3.0 in
Samsung mTower through 0.3.0 allows a trusted application to trigger a Denial of Service (DoS) by invoking the function TEE_MACUpdate with an excessive length value of chunkSize.
When the length value of the data block is not checked, a remote attacker can send a malicious data block with an excessive length value of chunkSize to the TEE_MACUpdate function of the mTower application with the m
Discovery of the Vulnerability
The vulnerability was discovered by security researcher Vincenzo Iozzo, working for Kaspersky Lab.
Vulnerable packages:
The vulnerability affects the following packages:
- mTower
Timeline
Published on: 09/16/2022 22:15:00 UTC
Last modified on: 09/21/2022 19:42:00 UTC
References
- https://github.com/Samsung/mTower/blob/efd36709306a9afcca5b4782499d01be0c7a02a5/tee/lib/libutee/tee_api_operations.c#L1188
- https://github.com/Samsung/mTower/blob/efd36709306a9afcca5b4782499d01be0c7a02a5/crypto/libtomcrypt/include/tomcrypt_hash.h#L397
- https://github.com/Samsung/mTower/issues/81
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-40760