Metacharacters can also be used to bypass content filters, for example by using a non-word character such as ` to bypass spell checks and prevent autocorrect. There are a variety of other ways to exploit this issue, such as by creating a file with a specially-crafted filename, or by uploading a file with a specially-crafted filename to Snyk's web-based plugin management page. In the latter case, the user would need to navigate to the file system where the uploaded package is stored in order to view its contents. There are a variety of other ways to exploit this issue, such as by creating a file with a specially-crafted filename. Exploitation could follow from the common practice of viewing untrusted files in the Visual Studio Code editor, for example. The original demonstration was with shell metacharacters in the vendor.json ignore field, affecting snyk-go-plugin before 1.19.1. This affects, for example, the Snyk TeamCity plugin (which does not update automatically) before 20220930.142957.
This issue affects Snyk CLI before 1.996.0, Snyk IDE before 1.996.0, and the snyk npm package. It can be exploited in various ways, including via viewing an untrusted file in an editor, via uploading an untrusted file to a web-based plugin management system, or via symlinking to an untr
Dependency Updates
The following versions of the project have been updated:
* 1.996.0 - Dependency Updates
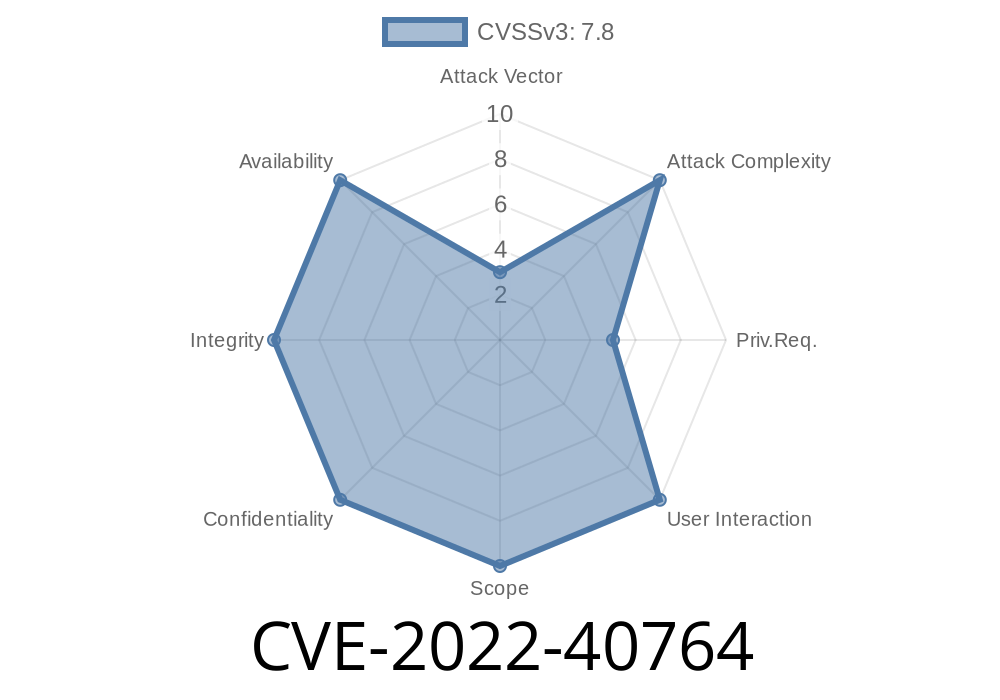
** 1.19.1 - CVE-2022-40764
** 1.20.0 - CVE-2018-15458
** 1.21.2 - CVE-2019-10892
** 1.23.6 - CVE-2019-11100
Timeline
Published on: 10/03/2022 15:15:00 UTC
Last modified on: 10/05/2022 17:08:00 UTC
References
- https://github.com/snyk/snyk-go-plugin/releases/tag/v1.19.1
- https://github.com/snyk/cli/releases/tag/v1.996.0
- https://support.snyk.io/hc/en-us/articles/7015908293789-CVE-2022-40764-Command-Injection-vulnerability-affecting-Snyk-CLI-versions-prior-to-1-996-0
- https://www.imperva.com/blog/how-scanning-your-projects-for-security-issues-can-lead-to-remote-code-execution/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-40764