If your app makes a request for data from an untrusted source, it is always a good idea to validate the data received before using it. To validate user input or to confirm that the user actually wants to perform an action, you can use the strcpy function. Unfortunately, the strcpy function has an important limitation: it copies a maximum of 19 characters at a time. If you need to copy a larger block of data, you must make sure to break it up into smaller chunks. Unfortunately, many apps do not take this into account, leading to a situation where a large amount of user data can be copied into a stack buffer. When this happens, the stack buffer overflows, causing a crash and potentially exposing sensitive information to attackers. You can protect yourself from this vulnerability by always validating user input.
CVE-2023-40785
: Strcpy Stack Buffer Overflow
Buffer overflow vulnerabilities are a common type of vulnerability that occur when there is insufficient memory to accommodate the data that the application is working with. The attacker takes advantage of this by sending more data than the process can handle, and that additional data overwrites other areas of memory. This is an important problem to avoid because it allows an attacker to gain access to sensitive information like passwords or cookies. To protect against buffer overflows, apps should be engineered so they cannot overrun their buffers. If a buffer overflow occurs, you can use the strcpy function to limit how much data can be copied into the stack buffer at any given time. The strcpy function stops copying after a maximum of 19 characters have been copied in each pass. This will help prevent overflow attacks from occurring for large amounts of user data.
Browsers and JavaScript Overview
Browsers and JavaScript
The most common type of browser is a web browser. Web browsers are programmable, so they can run JavaScript to help your website perform tasks such as create interactive graphs or animations. If you want to see what kind of information is available in the JavaScript console, click on the button in the address bar that says "JavaScript Console."
Overview of the vulnerability
Strcpy copies a maximum of 19 characters at a time. If you need to copy a larger block of data, you must make sure to break it up into smaller chunks. Unfortunately, many apps do not take this into account.
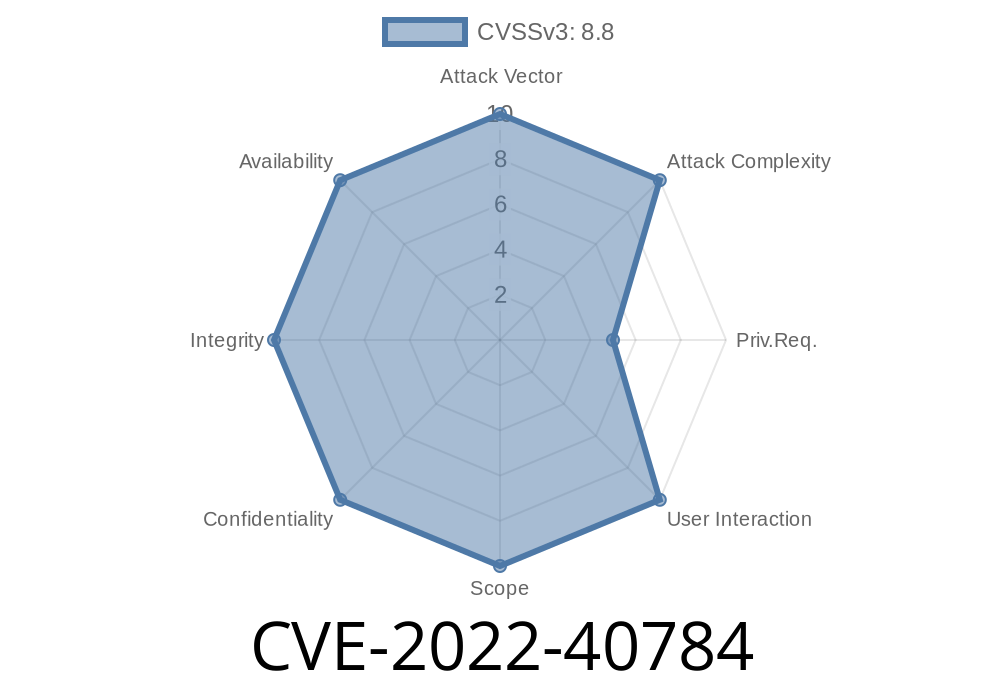
If your app makes a request for data from an untrusted source, it is always a good idea to validate the data received before using it. To validate user input or to confirm that the user actually wants to perform an action, you can use the strcpy function. Unfortunately, the strcpy function has an important limitation: it copies a maximum of 19 characters at a time. If you need to copy a larger block of data, you must make sure to break it up into smaller chunks. Unfortunately, many apps do not take this into account, leading to a situation where a large amount of user data can be copied into a stack buffer. When this happens, the stack buffer overflows and causes an overflow crash and potentially exposing sensitive information through stack buffer overflow vulnerabilities (CVE-2022-40784).
How do you know if your app is vulnerable?
To know if your app is vulnerable to this vulnerability, you will need to verify your app's stack buffer. You can do so by letting the app make a request for data from an untrusted source and checking to see if the resulting buffer overflow causes a crash. If it does, then your app is potentially vulnerable and should be updated.
Timeline
Published on: 09/26/2022 16:15:00 UTC
Last modified on: 09/28/2022 19:37:00 UTC